Summary
In May 2017, SecureWorks® Counter Threat Unit® (CTU) researchers investigated a widespread and opportunistic WCry (also known as WanaCry, WanaCrypt, and Wana Decrypt0r) ransomware campaign that impacted many systems around the world. Some affected systems have national importance. CTU® researchers link the rapid spread of the ransomware to use of a separate worm component that exploited vulnerabilities in the Windows Server Message Block (SMB) v1 protocol. Microsoft addressed the SMBv1 vulnerabilities in March 2017 with Security Bulletin MS17-010.
Delivery
The campaign’s use of an SMB worm to distribute WCry contributed to the ransomware’s virulence. As of this publication, the specific delivery method for the SMB worm is unclear. Upon starting, the worm attempts an HTTP connection to www . iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea . com. If the connection is successful, then the worm stops running and exits. The threat actors may have added this HTTP connection test to prevent automated sandboxes from running and analyzing the malware.
The worm leverages an SMBv1 exploit that originates from tools released by the Shadow Brokers threat group in April. The worm specifically scans for the existence of the DoublePulsar backdoor on compromised systems. If the DoublePulsar backdoor does not exist, then the SMB worm attempts to compromise the target using the Eternalblue SMBv1 exploit. Propagation relies on two process threads. After the first thread determines the local network subnet, the SMB worm scans local addresses beginning at the start of the netblock and increasing by one to the end of the netblock. The second thread scans randomly chosen external IP addresses.
The SMB worm delivers itself to the compromised system as a DLL file payload. After the DLL is executed with a single exported function named PlayGame, it writes a copy of the original SMB worm to C:\Windows\mssecsvc.exe and then executes this file. The SMB worm then drops a secondary payload from its resources section to C:\Windows\tasksche.exe and executes this file. In the samples analyzed by CTU researchers, this secondary payload is the WCry ransomware.
Infection
After encrypting the file system, WCry displays the ransom demand shown in Figure 1.
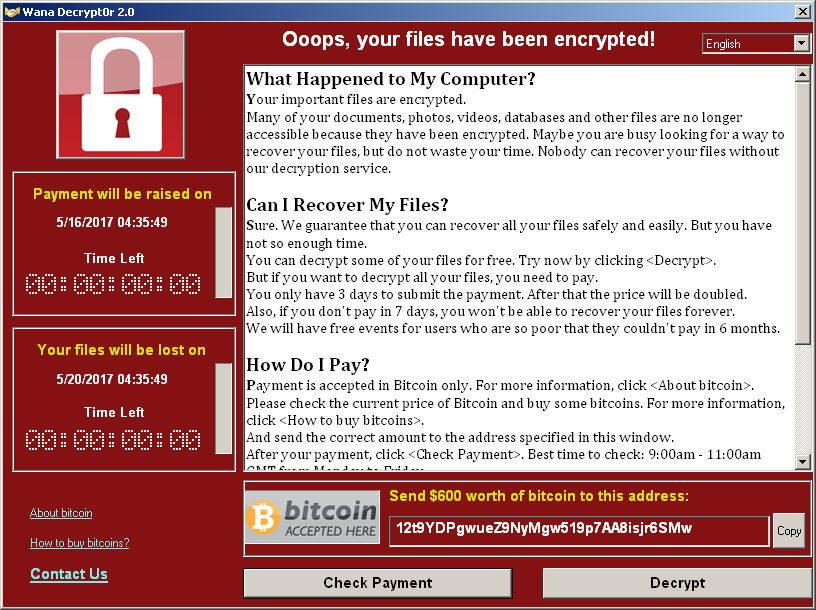
Figure 1. WCry (also known as Wana Decrypt0r) ransom demand interface. (Source: SecureWorks)
The malware continually monitors this window to ensure it remains in focus, reopening it if it is closed. WCry also launches a small program named taskse.exe that enumerates active RDP sessions and ensures the remote user can see the window. Additionally, the malware changes the desktop wallpaper to the image in Figure 2.
Figure 2. Desktop wallpaper set by WCry ransomware. (Source: SecureWorks)
WCry is distributed as an executable file that contains a password-protected ZIP archive in its resources section. When executed, this archive is unpacked (using the password “WNcry@2ol7”) in the current directory and contains the following files:
- b.wnry — Bitmap image used as desktop wallpaper (shown in Figure 2)
- c.wnry — Configuration containing Tor command and control (C2) addresses, Bitcoin addresses, and other data
- r.wnry — Ransom demand text
- s.wnry — ZIP archive containing Tor software to be installed on the victim’s system; saved in TaskData directory
- t.wnry — Encrypted DLL containing file-encryption functionality
- u.wnry — Main module of the WCry ransomware “decryptor”
- taskdl.exe — WNCRYT temporary file cleanup program
- taskse.exe — Program that displays decryptor window to RDP sessions
- msg — Directory containing Rich Text Format (RTF) ransom demands in multiple languages
WCry creates additional files during the infection:
- 00000000.pky — Microsoft PUBLICKEYBLOB containing the RSA-2048 public key (The WCry threat actors presumably hold the private key.)
- 00000000.res — Data for C2 communication
- 00000000.eky — Victim-unique RSA private key encrypted with embedded RSA public key
- 00000000.dky — Decrypted RSA private key transmitted to victim after ransom payment
- f.wnry — A list of randomly chosen files encrypted with an embedded RSA private key that allows WCry to “demonstrate” decryption to victims
- @[email protected] — Main module of the WCry ransomware “decryptor,” identical to u.wnry
- @[email protected] — Ransom demand text, identical to r.wnry
When started, WCry executes two commands:
- attrib +h .
- icacls . /grant Everyone:F /T /C /Q
WCry executes the following single command (formatted for readability) to complicate system and data recovery. If the malware is not running with elevated privileges, WCry executes this with the “runas” command.
cmd.exe /c vssadmin delete shadows /all /quiet &
wmic shadowcopy delete &
bcdedit /set {default} bootstatuspolicy ignoreallfailures &
bcdedit /set {default} recoveryenabled no &
wbadmin delete catalog -quiet
WCry terminates several services so that their data stores can be encrypted:
- taskkill.exe /f /im mysqld.exe
- taskkill.exe /f /im sqlwriter.exe
- taskkill.exe /f /im sqlserver.exe
- taskkill.exe /f /im MSExchange*
- taskkill.exe /f /im Microsoft.Exchange.*
WCry creates a batch file using a randomly generated large integer (e.g., 46631494859358.bat, 37061494619317.bat) that creates a shortcut to the malware executable (see Figure 3).
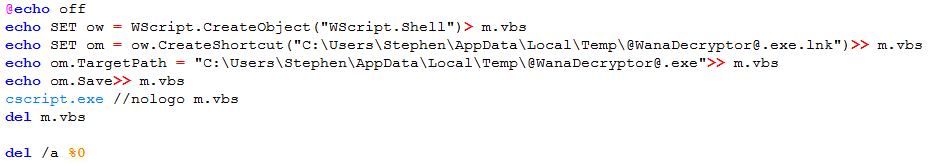
Figure 3. Batch file executed by WCry ransomware. (Source: SecureWorks)
The malware’s current working directory is saved to the “wd” registry value under the \SOFTWARE\WanaCrypt0r key (see Figure 4). If WCry is running with elevated privileges, the key is created in the HKLM registry hive; otherwise, it is created in the HKCU hive.
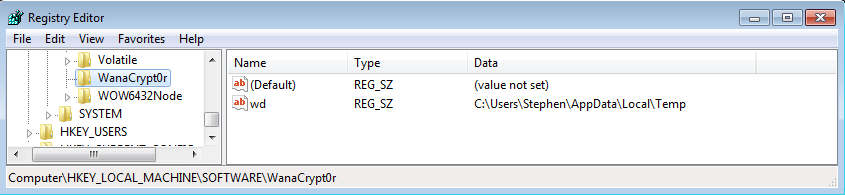
Figure 4. Metadata stored in registry by WCry ransomware. (Source: SecureWorks)
WCry creates a registry Run key value (see Figure 5) to ensure the ransomware GUI is displayed when victims log in or restart the computer.
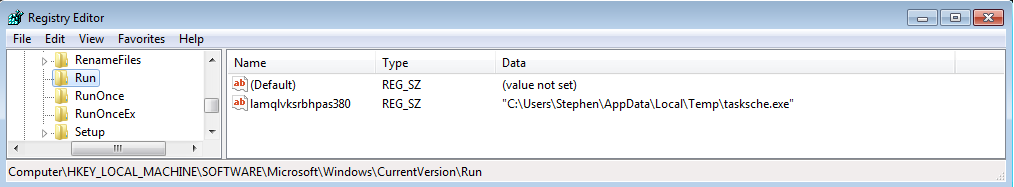
Figure 5. Run key created by WCry ransomware. (Source: SecureWorks)
Encryption
WCry uses a combination of the RSA and AES algorithms to encrypt files. It uses the Windows Crypto API for RSA encryption and random key generation; however, a third-party implementation of AES is statically linked within the malware. CTU researchers did not identify any flaws in the cryptographic implementation, so file recovery through decryption is likely not possible without a decrypted private key from the ransomware operators.
Prior to encryption, WCry enumerates all available disks on the system. This enumeration includes local drives (e.g., hard disks), removable drives (e.g., USB thumb drives), and network drives (e.g., a remote file share mapped to a drive letter). The malware does not contain functionality to search the local network for unmapped file shares. WCry also searches for the presence of the Global\MsWinZonesCacheCounterMutexA mutex prior to file encryption and exits if the mutex exists.
WCry targets file extensions associated with productivity and database applications, compressed archives, and multimedia formats (see Figure 6). The encryption process skips files whose pathnames contain the directory names and language listed in Table 1.
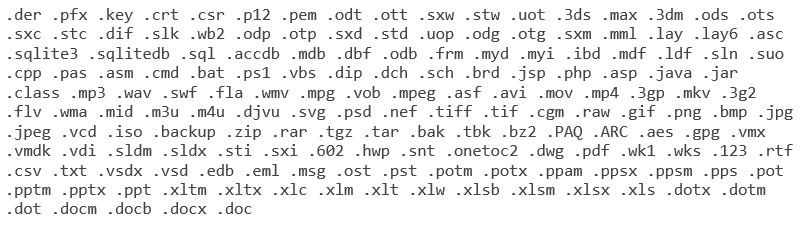
Figure 6. File extensions targeted by WCry ransomware. (Source: SecureWorks)
|
Content.IE5 |
Temporary Internet Files |
\LocalSettings\Temp |
ppData\Local\Temp |
|
\Program Files |
\Program Files (x86) |
\WINDOWS |
\ProgramData |
|
\Intel |
This folder protects against ransomware. Modifying it will reduce protection |
Table 1. Whitelisted directory name components.
WCry generates a private RSA-2048 key pair specific to each infection and stores it on the local disk with an .eky extension (e.g., 00000000.eky) after encrypting it with an embedded RSA public key. This generated RSA key is used to encrypt the random AES-128 key generated for each encrypted file.
Each targeted file is opened, read, encrypted in memory, and then written to a new file in the malware’s working directory using the filename format <random number>.WNCRYT. The files are then renamed to their original filename followed by the .WINCRY extension and moved to their original directory. The taskdl.exe process launched by the malware periodically deletes the remaining WINCRYT temporary files. The encryption process does not directly overwrite file data, so forensic recovery of file contents may be possible depending on the environment. The entire contents of the file are encrypted and saved with a custom header (see Figure 7).
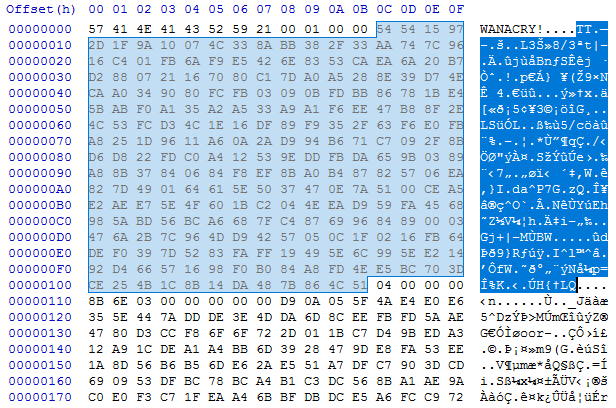
Figure 7. WCry file header prepended to encrypted file (encrypted AES key highlighted). (Source: SecureWorks)
The header follows the pattern shown in Figure 8, which allows the malware to identify previously encrypted files and reliably decrypt them.
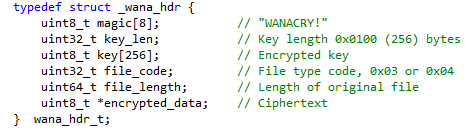
Figure 8. WCry encrypted file header. (Source: SecureWorks)
Payment
After infecting a system, WCry displays a timer that counts down to the dates when the ransom amount increases (four days) and when files will be irrecoverable (seven days). WCry can be configured to demand different ransom amounts in dollars or bitcoins. CTU researchers observed WCry variants demanding Bitcoin payments equivalent to $300 and $600. The Bitcoin address is provided in the c.wnry configuration file and can vary across samples. If no configuration file is present, the malware uses a hard-coded Bitcoin address. CTU researchers have identified the following Bitcoin addresses associated with the WCry ransomware:
- 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
- 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
- 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 (hard-coded)
CTU researchers have no evidence that the WCry threat actors have the capability or intent to decrypt files for paying victims. Many ransomware families assign each victim a unique Bitcoin address so the threat actors can attribute a payment directly to an infection and associated decryption key. WCry does not include this feature, so the threat actor must rely on communication with the victim to make the connection.
Command and control (C2) traffic
WCry installs the Tor network anonymity software on the infected system in the TaskData folder within the malware’s working directory. The local Tor server is renamed and executed as taskhsvc.exe. Tor establishes a SOCKS5 proxy server on the loopback interface (127.0.0.1) that listens on TCP port 9050. WCry connects to this proxy and attempts to contact the configured C2 hidden services:
- gx7ekbenv2riucmf . onion
- 57g7spgrzlojinas . onion
- xxlvbrloxvriy2c5 . onion
- 76jdd2ir2embyv47 . onion
- cwwnhwhlz52maqm7 . onion
After connecting to a C2 server, the malware uses a custom encrypted protocol over TCP port 80 through the Tor circuit to transmit encryption keys, to allow victims to communicate with the operators, and to check payment status. WCry does not exfiltrate documents, steal stored credentials, or receive and execute additional files.
Conclusion
WCry is an opportunistic ransomware family whose propagation methods allow it to spread quickly. CTU researchers recommend that clients implement the following best practices to mitigate the threat:
- Apply the Microsoft security updates for MS17-010, including the updates for the Windows XP and Windows Server 2003 legacy operating systems.
- Disable SMBv1 on systems where it is not necessary (e.g., hosts that do not need to communicate with Windows XP and Windows 2000 systems). Carefully evaluate the need for allowing SMBv1-capable systems on interconnected networks compared to the associated risks.
- Segment networks to isolate hosts that cannot be patched, and block SMBv1 from traversing those networks.
- Scan networks for the presence of the DoublePulsar backdoor using plugins for tools such as Nmap.
- Use network auditing tools to scan networks for hosts that are vulnerable to the vulnerabilities described in MS17-010.
- Filter emails containing potentially dangerous file types such as executables, scripts, or macro-enabled documents.
- Implement a backup strategy that includes storing data using offline backup media. Backups to locally connected, network-attached, or cloud-based storage are often insufficient because ransomware frequently accesses and encrypts files stored on these systems.
Threat indicators
The threat indicators in Table 2 can be used to detect activity related to WCry and associated delivery mechanisms. The domains may contain malicious content, so consider the risks before opening them in a browser.
|
Indicator |
Type |
Context |
|
gx7ekbenv2riucmf.onion |
Tor address |
WCry C2 server |
|
57g7spgrzlojinas.onion |
Tor address |
WCry C2 server |
|
xxlvbrloxvriy2c5.onion |
Tor address |
WCry C2 server |
|
76jdd2ir2embyv47.onion |
Tor address |
WCry C2 server |
|
cwwnhwhlz52maqm7.onion |
Tor address |
WCry C2 server |
|
Microsoft Security Center (2.0) Service |
Service display name |
WCry SMB worm |
|
mssecsvc2.0 |
Service name |
WCry SMB worm |
|
C:\Windows\mssecsvc.exe |
Filename |
WCry SMB worm |
|
C:\Windows\Tasksche.exe |
Filename |
WCry SMB worm payload |
|
C:\Windows\qeriuwjhrf |
Filename |
WCry SMB worm payload copy |
|
db349b97c37d22f5ea1d1841e3c89eb4 |
MD5 hash |
WCry SMB worm |
|
e889544aff85ffaf8b0d0da705105dee7c97fe26 |
SHA1 hash |
WCry SMB worm |
|
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
SHA256 hash |
WCry SMB worm |
|
Global\MsWinZonesCacheCounterMutexW |
Mutex |
WCry exclusion flag |
|
%PROGRAMDATA%\%RAND%\00000000.eky |
Filename |
WCry encryption key |
|
63fb6dd827559c0ed40c4c3725f7fc0a |
MD5 hash |
WCry encryption key |
|
8e7211b1455dedfe1f84cc60a7ed593f78dfb6e1 |
SHA1 hash |
WCry encryption key |
|
24076e8485c72e4f9cf997c1f3670337231e401a043505e489606fff5758150f |
SHA256 hash |
WCry encryption key |
|
00000000.pky |
Filename |
WCry public key |
|
f5c0755e5f08dabf1119c193e96539a6 |
MD5 hash |
WCry public key |
|
5109c0738c126e65db8a92e1ff24f3291837f627 |
SHA1 hash |
WCry public key |
|
c863b4b4780d6ce53827049d3733863283aaeb4d4ae806fc2c5cfbd9eb236ab8 |
SHA256 hash |
WCry public key |
|
00000000.res |
Filename |
WCry C2 communication data |
|
492c258c5bcbdd812fddd99b2427da99 |
MD5 hash |
WCry C2 communication data (00000000.res) |
|
0c16196d93b076f4648a9b1b027e7735845cab20 |
SHA1 hash |
WCry C2 communication data (00000000.res) |
|
6fa17600177c2032c3c3a3c06df6cf7d8dba1d32db146d9dd87aecf3f39fb898 |
SHA256 hash |
WCry C2 communication data (00000000.res) |
|
b.wnry |
Filename |
WCry ransom demand desktop wallpaper |
|
c17170262312f3be7027bc2ca825bf0c |
MD5 hash |
WCry ransom demand desktop wallpaper (b.wnry) |
|
f19eceda82973239a1fdc5826bce7691e5dcb4fb |
SHA1 hash |
WCry ransom demand desktop wallpaper (b.wnry) |
|
d5e0e8694ddc0548d8e6b87c83d50f4ab85c1debadb106d6a6a794c3e746f4fa |
SHA256 hash |
WCry ransom demand desktop wallpaper (b.wnry) |
|
c.wnry |
Filename |
WCry configuration file |
|
fa44d43242f0bcc6d64569e4869e4913 |
MD5 hash |
WCry configuration file (c.wnry) |
|
29da372c816ac0d636657a76ab7712ae8106cb45 |
SHA1 hash |
WCry configuration file (c.wnry) |
|
3324483d27e716feb408b5d16b82540731faf435b9325497df779d72e7a6b765 |
SHA256 hash |
WCry configuration file (c.wnry) |
|
f.wnry |
Filename |
WCry decryption demonstration file list |
|
Filename |
WCry ransom note |
|
|
r.wnry |
Filename |
WCry ransom note |
|
3e0020fc529b1c2a061016dd2469ba96 |
MD5 hash |
WCry ransom note |
|
c3a91c22b63f6fe709e7c29cafb29a2ee83e6ade |
SHA1 hash |
WCry ransom note |
|
402751fa49e0cb68fe052cb3db87b05e71c1d950984d339940cf6b29409f2a7c |
SHA256 hash |
WCry ransom note |
|
s.wnry |
Filename |
WCry ZIP archive containing Tor software |
|
ad4c9de7c8c40813f200ba1c2fa33083 |
MD5 hash |
WCry ZIP archive containing Tor software |
|
d1af27518d455d432b62d73c6a1497d032f6120e |
SHA1 hash |
WCry ZIP archive containing Tor software |
|
e18fdd912dfe5b45776e68d578c3af3547886cf1353d7086c8bee037436dff4b |
SHA256 hash |
WCry ZIP archive containing Tor software |
|
taskdl.exe |
Filename |
WCry temporary file cleanup program |
|
4fef5e34143e646dbf9907c4374276f5 |
MD5 hash |
WCry temporary file cleanup program (taskdl.exe) |
|
47a9ad4125b6bd7c55e4e7da251e23f089407b8f |
SHA1 hash |
WCry temporary file cleanup program (taskdl.exe) |
|
4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79 |
SHA256 hash |
WCry temporary file cleanup program (taskdl.exe) |
|
tasksche.exe |
Filename |
WCry installer |
|
84c82835a5d21bbcf75a61706d8ab549 |
MD5 hash |
WCry installer |
|
5ff465afaabcbf0150d1a3ab2c2e74f3a4426467 |
SHA1 hash |
WCry installer |
|
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa |
SHA256 hash |
WCry installer |
|
taskse.exe |
Filename |
WCry RDP session decryptor display tool |
|
8495400f199ac77853c53b5a3f278f3e |
MD5 hash |
WCry RDP session decryptor display tool (taskse.exe) |
|
be5d6279874da315e3080b06083757aad9b32c23 |
SHA1 hash |
WCry RDP session decryptor display tool (taskse.exe) |
|
2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d |
SHA256 hash |
WCry RDP session decryptor display tool (taskse.exe) |
|
t.wnry |
Filename |
WCry file encryption DLL |
|
5dcaac857e695a65f5c3ef1441a73a8f |
MD5 hash |
WCry file encryption DLL |
|
7b10aaeee05e7a1efb43d9f837e9356ad55c07dd |
SHA1 hash |
WCry file encryption DLL |
|
97ebce49b14c46bebc9ec2448d00e1e397123b256e2be9eba5140688e7bc0ae6 |
SHA256 hash |
WCry file encryption DLL |
|
Filename |
WCry decryptor |
|
|
u.wnry |
Filename |
WCry decryptor |
|
7bf2b57f2a205768755c07f238fb32cc |
MD5 hash |
WCry decryptor (u.wnry and @[email protected]) |
|
45356a9dd616ed7161a3b9192e2f318d0ab5ad10 |
SHA1 hash |
WCry decryptor (u.wnry and @[email protected]) |
|
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25 |
SHA256 hash |
WCry decryptor (u.wnry and @[email protected]) |
|
Filename |
WCry decryptor shortcut |
Table 2. Threat indicators for WCry.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

