- Author: Brett Stone-Gross
Dell SecureWorks Counter Threat Unit™ Threat Intelligence - Date: 28 March 2012
Overview
On Wednesday, March 21, 2012, security experts from Dell SecureWorks, CrowdStrike, Kaspersky, and the Honeynet Project initiated efforts to detect and disrupt the operations of a botnet known as Waledac/Kelihos (also known as Hlux). This botnet is believed to be the successor to the infamous Storm Worm DDoS attack because of shared code, architecture, and functionality.
The Waladec/Kelihos botnet is organized through a peer-to-peer network that contains a tiered infrastructure. As shown in Figure 1, the top tier consists of a set of servers managed by the botnet controllers, which can push commands to a set of middle-tiered nodes. These router nodes relay messages to neighboring peers and to worker nodes at the bottom tier, which are primarily responsible for sending spam email, harvesting email addresses and credentials, and stealing Bitcoin wallets.
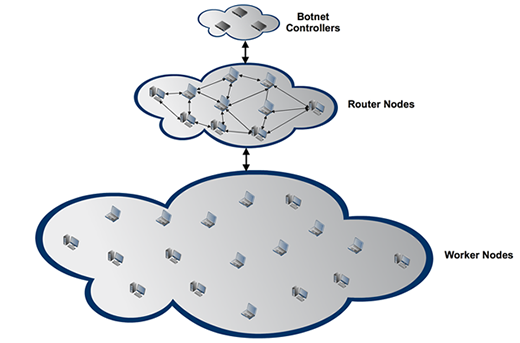
Figure 1. High-level overview of the peer-to-peer network architecture of the Waledac/Kelihos botnet.
Waledac/Kelihos Botnet, Distribution and AV Coverage
SecureWorks Counter Threat Unit TM(CTU) researchers have observed that the Waledac/Kelihos botnet malware is being distributed through pay-per-install (PPI) affiliate programs that often install additional trojans (e.g., Fifesock) and fake antivirus software.
The malware packer used by Waledac/Kelihos is rather effective against antivirus (AV) botnet detection. As of March 27, 2012, VirusTotal showed relatively low botnet detection rates for the samples analyzed by the CTU team:
(MD5) db95341667fb5e5553a1cb0113e21205: 13/42 results
(MD5) 84cbcfababd4eafd1a8a4872b9169362: 15/42 results
Key Detection Findings from Waledac/Kelihos Botnet Takeover
In September 2011, Kaspersky and Microsoft performed a similar takeover of a previous version of the Waledac/Kelihos botnet. The new version differs from its predecessor with a few new features and a slightly modified communication protocol. With our partners in the March 2012 botnet takeover, we were able to identify vulnerabilities that allowed us to introduce fake node entries into the peer-to-peer network. These entries propagated throughout the network. As a result, the peer list of infected nodes was replaced entirely with our fake nodes, and all compromised hosts began contacting our sinkhole awaiting instructions.
Botnet Detection Statistics
The previous version of the Waledac/Kelihos botnet that was taken down in September 2011 was estimated to consist of 40,000 infected computers. In comparison, the Waledac/Kelihos botnet that we sinkholed has more than 118,000 systems (unique bot IDs) under its control. Figure 2 shows the connections detected from botnet-infected computers to our sinkhole.

Figure 2. Each line represents a connection from a Waledac/Kelihos infected machine to our sinkhole on March 21, 2012. (Source: Dell SecureWorks)
The number of hosts in Poland accounted for more than 24% of the overall number of bots. It is not apparent why there was such a large concentration botnet infections dectected specifically in Poland, but one possible explanation is that the PPI network that was distributing the Waledac/Kelihos botnet had compromised a large number of Polish websites. Consequently, the hacked websites could have been used to serve exploits that lead to the installation of the malware through drive-by-download attacks.
Overall, we observed more than 430,000 unique IP addresses since our sinkhole came online on March 21, 2012. Interestingly, we detected more unique botnet IDs than IP addresses during the first few hours of the sinkhole operation due to Network Address Translation (NAT) and firewall/proxy effects. In other words, some of the infected computers shared the same external IP address. Table 1 shows the statistics of infections per country. The United States ranked second in the overall number of botnet infections detected, even though bots located in the U.S. typically cost more through PPI affiliate programs.
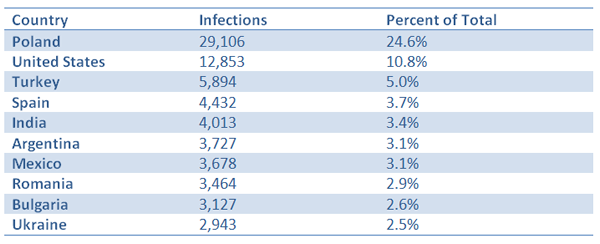
Table 1. Listing of the top 10 countries with Waledac/Kelihos infections.
Figure 3 shows the number of unique bot IDs observed per hour. On average, there were 13,855 bots online, and the number peaked at 21,215 bots. The low points on the graph indicate a normal diurnal pattern of botnets where infected systems are turned on in the morning and turned off at night.
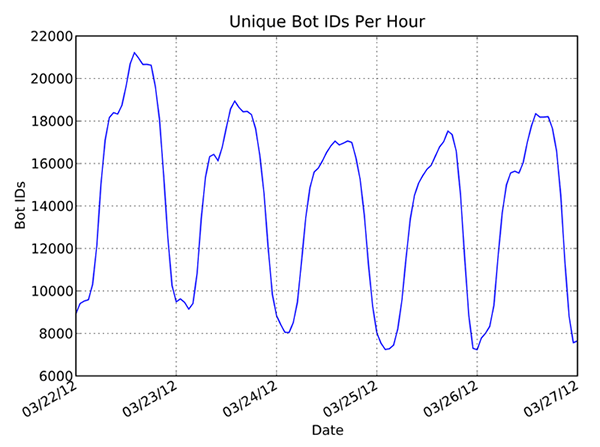
Figure 3. The number of live Waledac/Kelihos bots per hour based on unique bot ID. (Source: Dell SecureWorks)
Figure 4 shows the difference between the total number of infected systems counted by unique bot IDs versus the number of unique IP addresses that contacted our sinkhole.
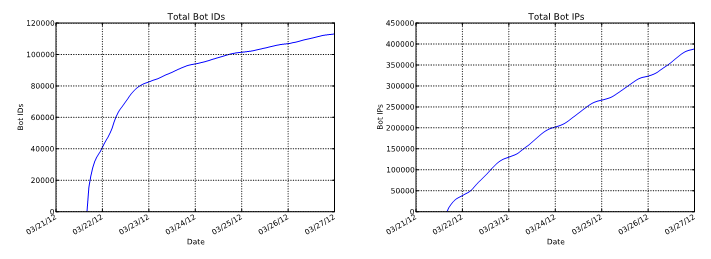
Figure 4. Comparison between unique IP addresses and bot IDs. Note that the effects of DHCP distort the number of actual infections over time. (Source: Dell SecureWorks)
Lastly, we examined how well connected the Waledac/Kelihos peer-to-peer network was by analyzing each node's peers list. Because each node maintains a list of up to 250 other peers, the network organizes itself almost into a single cluster. Figure 5 shows how the peer-to-peer network appeared at the start of our sinkhole.
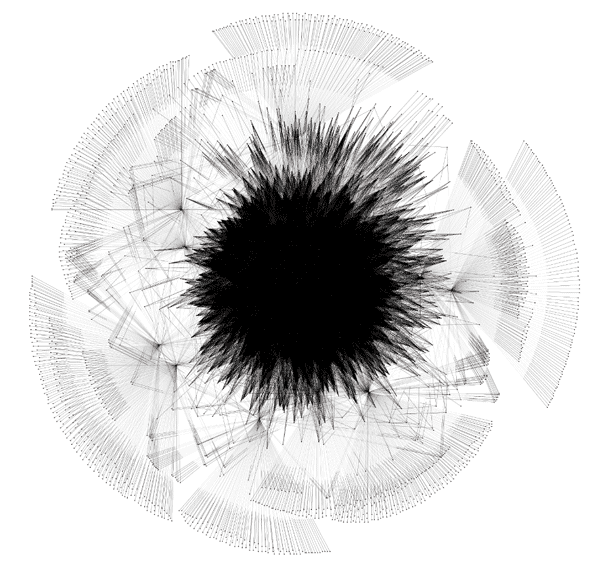
Figure 5. The peer-to-peer network graph. The edges between nodes indicate a link between two nodes based on their peer lists. (Source: Dell SecureWorks)
Botnet Protection Recommendations
The CTU research team recommends that businesses continue to educate employees on botnet protection and enforce policies to keep the software on systems up to date. It's important to note that even if operating systems and third-party applications are updated, the end user can still fall victim to the social engineering aspect. To combat the threats, the CTU research team recommends a defense-in-depth botnet protection strategy:
- Deploy countermeasures for the Waledac/Kelihos botnet malware
- Deploy countermeasures for the Fifesock malware, which is currently downloading the Waledac/Kelihos malware onto victim computers
- Instruct end users not to store passwords on their computer, or use a password manager such as KeepPass that stores passwords in an encrypted form
- Keep third-party applications updated, including the operating system and web browsers
- Keep web browser extensions and plugins updated, especially Adobe Reader, Adobe Flash, and Java
- Educate end users on the threats posed by attachments and links contained in emails
- Keep antivirus products up to date to enable better botnet detection
- Use different antivirus software on the endpoint workstations and at the gateway
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
