Introduction
In part one of this article, we examined the workings of the rogue antivirus program "Antivirus XP 2008". In this part we will take a look inside the affiliate program responsible for this software and reveal the enormous amount of money being made by rogue anti-malware software.
Pandora Software == Bakasoftware
The name "Pandora Software" has been associated with many rogue anti-malware products over the years. The basic functionality of the programs stays the same, but the names are changed and the front-end is redesigned in order to stay "fresh".
Below are just some of the previous programs that have been pushed by this rogue software company:
 Easy Spyware Cleaner |
 SpyRid |
 InfeStop |
 WinIFixer |
 Advanced XP Defender |
 Advanced XP Fixer |
 Malware Protector 2008 |
 Antivirus XP 2008 |
However, this name is just a front for an affilate program that is more deeply hidden. The operation is called "Bakasoftware", and it is run by a user known as "krab". Below is a screenshot of a posting (in Russian) made by krab, advertising Bakasoftware to members of one of the largest pharmaceutical spam affiliate forums:

The Russian Connection
Several of these types of affiliate programs are Russian in origin, and Bakasoftware is no exception. The Bakasoftware website is entirely in Russian:
There is no other language translation available on the website - therefore it can be safely assumed that the entirety of forced installs of Antivirus XP 2008 are being performed by Russian-speaking individuals against non-Russian-speaking victims.
How do we know that the targeted victims of this software are mainly non-Russian users? On startup, the AV XP 08 installer first checks the locales installed on the victim system using the Windows API GetKeyboardLayout. It will exit immediately if it finds the user has one of the following locales, all of which are countries with large Russian-speaking populations:
- Russia
- Czech Republic
- Ukraine
- Belarus
- Estonia
- Latvia
- Lithuania
Additionally, the installer checks the URL cache for Internet Explorer to see if the user has recently visited one of the following sites:
- vkontakte.ru
- google.ru
- tibsystems.*
- statsbank.com
- boards.cexx.org
- adultwebmasterinfo.com
- spywareinfo.*
- dialerschutz.de
- webmasterworld.com
- crutop.nu
- go[removed]yourself.com
Between the locale and cache checks, this is enough to pretty much guarantee that Russian-speaking users will not ever see an Antivirus XP 2008 install show mysteriously up on their machine like it does on so many others worldwide. However, in the most recent installer version the locale/cache checks are performed but the results are not evaluated (probably due to a coding error) so the newest version (to be called AntiMalware 2009) might actually make it onto Russian machines. We hate to see anyone have to deal with this pest, but perhaps this might help raise awareness of the problem in those countries.
Affiliate System
Bakasoftware is a closed system - only invited users may sign up with the program. Invitations can be handed out only by existing users. Once a new member joins, he/she is given access to a control panel which provides information about the program and number of different distributions (activeX controls, "codec" installs and standalone executables) of the rogue antivirus to install on victim machines. Or the affiliate can simply use links/popup ads to push traffic to an "online scanner" that convinces unsuspecting users that they are infected and need to buy the full version of the program.
The image below shows all the different installer options that an affiliate can choose for AV XP 08:
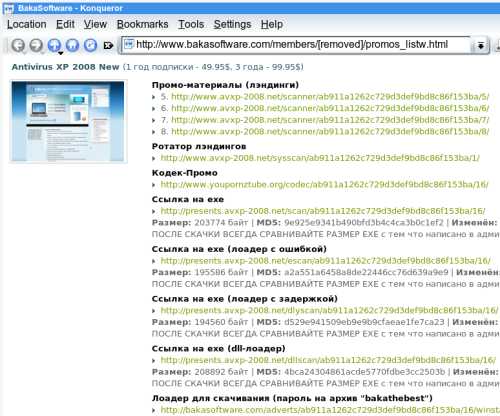
Earnings
Members also get access to a statistics page to show the numbers of installs they have made, the number purchases of the program by victims, and profits made. Affiliates can earn anywhere from 58 to 90 percent commission on sales of the software, depending on the volume of sales. This is an extraordinarily high commission, so one can see why affiliate programs involving rogue anti-malware products are so popular among hackers and spammers. There is a great deal of money to be made pushing these programs.
In the forum posting shown above, krab even shows some statistics for one of the top Bakasoftware earners (we've translated the column meanings below in red):
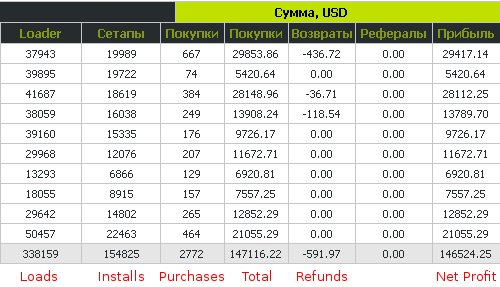
If these stats are to be believed, one affiliate was able to install 154,825 copies of AV XP 08 in ten days' time, and 2,772 of those copies were actually purchased by the victims. This only represents a one to two percent conversion rate, but with the generous commission structure, was enough to earn the affiliate $146,525.25 for that time period. At that rate, the affiliate could be expected to earn over 5 million U.S. dollars a year, simply by maintaining a large botnet and forcing AV XP 08 installs on 10,000 to 20,000 computers a day.
Bakasoftware Hacked At the same time we were investigating the Bakasoftware program, a Russian hacker going by the handle "NeoN" posted a great deal of inside information about Bakasoftware to the Internet. Apparently an acquaintance of NeoN was able to hack into the Bakasoftware website through a SQL injection exploit and obtain the administrative password. Using this information, NeoN was able to learn about and reveal several interesting details about the Bakasoftware operation, including a list of the top earners in the affiliate program:
| Affiliate ID | Affiliate Username | Account Balance (USD) |
|---|---|---|
| 4928 | nenastniy | $158,568.86 |
| 56 | krab | $105,955.76 |
| 2 | rstwm | $95,021.16 |
| 4748 | newforis | $93,260.64 |
| 5016 | slyers | $85,220.22 |
| 3684 | ultra | $82,174.54 |
| 3750 | cosma2k | $78,824.88 |
| 5050 | dp322 | $75,631.26 |
| 3886 | iamthevip | $61,552.63 |
| 4048 | dp32 | $58,160.20 |
NeoN did not indicate what time ranges these balances represent, but we believe these are totals for a single week. Even putting aside the tremendous amounts of money involved here, there are several interesting points of data in this list. The top earner, nenastniy is in all likelihood the same person we wrote about last year who sent political spam using the Srizbi botnet. With access to a major spam botnet, earnings from delivering Antivirus XP 2008 as a payload can be quite handsome it seems.
Credit-Card Fraud and Money Laundering
Also interesting in the top earners list is the fact that krab, although the number two earner and supposedly administrator of the site, has a user ID in the 50s, where the next top earner, rstwm, has a user ID of "2". NeoN had a theory about rstwm's earnings which he/she developed from looking into the stats page for rstwm:
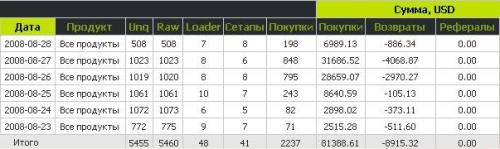
It seems that rstwm maintains a conversion rate some days of over 75% - as opposed to the one or two percent of normal users. Also, rstwm has a very high refund rate - in this context, refund probably means "chargeback", suggesting rstwm is likely using stolen credit card numbers to purchase the software and having the money credited to his affiliate ID. The Bakasoftware system would provide the adminstrator(s) an excellent way to launder money from stolen credit cards. As long as the administrator didn't get too greedy, there would always be enough legitimate (meaning not-charged-back) purchases of the software to avoid making the merchant account provider suspicious that the operation was entirely fraudulent and closing the account.
Conclusion
Bakasoftware is just one of many rogue anti-malware affiliate programs. It should now be clear just why this particular scheme is so prevalent in today's Internet - the sheer amounts of money involved in installing just one rogue program are mind-boggling even to veteran security researchers. Even Macintosh users are no longer immune to the threat of rogue AV attempting to worm its way onto systems, looking for that gullible one to two percent of users. In this case, user education might be the root of the problem: users are constantly bombarded with "helpful" warnings and alerts by every conceivable security application. The rogue AV developers are growing rich off of this fact.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
