- Date: August 11, 2006
- Author: Joe Stewart
Summary
Multiple sources are sounding alarms based on the MS06-040 exploit, predicting an imminent worm outbreak of Blaster-like proportions. We at SecureWorks would like to offer an alternative point of view.
First, although the vulnerability affects all versions/service pack levels of Windows NT up to 2003/XP, the exploit only provides remote-code-execution on Windows 2000 and XP SP1 and 2003 SP0. This limits the potential target for a worm to systems that are frankly, probably already running one or more worms.
The exploit must traverse TCP port 139 or 445. Aside from being firewalled on almost all network firewalls, many ISPs have begun blocking these ports which are almost 100% guaranteed to be used by only worms as far as residential customers are involved.
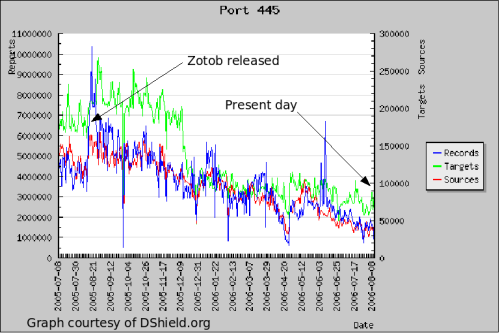
Based on the decreasing number of targets, we posit that the realized impact of an MS06-040-based worm would be even less than that of Zotob, which appeared one year ago. Although there were a few major organizations burned by Zotob, it had little impact on the Internet as a whole.
With each Microsoft Networking worm we see, companies eventually learn and adapt, deploying patch management solutions, network firewall/ACLs and containment systems. They have no choice - either prevent a future outbreak or be unable to continue business. Most of the time it only takes one such outbreak to convince the corporate powers-that-be to employ a defense of some kind.
So, even if the worst-case scenario appears, it will likely be fairly uneventful for organizations following a reasonable patch policy. The typical scenario we used to see of road warriors/consultants bringing an infected system inside a vulnerable network and causing an outbreak has largely been mitigated by laptops shipping with XP SP2 over the past two years.
So, will we see a worm based on MS06-040? Probably - at the very least someone will incorporate it into an already-existing bot. Will it infect many people? Not even as many as Zotob. Essentially it will hit the group of people who are already infected with Zotob and other worms, and the ones who patched against Zotob but left their system open to other exploits.
Update:
As expected, someone has integrated the exploit into the Mocbot IRC bot. It is not especially threatening, and appears to be virtually the same functionality as previous variants, except the substitution of MS06-040 for MS06-039.
Based on the current numbers of IP addresses on the Internet scanning for TCP port 445 (presumably vulnerable and infected with some other worm), shown in the graph below, we'd say the total number of worldwide infections of such a worm would be on the order of 20,000 to 50,000. Zotob at its peak was probably 100,000 to 200,000, based on DShield data. Microsoft's malware removal tool statistics only report 6,132 computers infected with Zotob between January 2005 and March 2006. By way of comparison, Blaster was estimated to have infected 8 million computers and Microsoft's stats show it was removed from 85,434 computers in that same Jan 2005 through Mar 2006 timeframe.
Now, we're not saying don't patch your systems. If you are using pre-XP SP2/2003 SP1 throughout your organization, it should be a priority right now. However, the world is not ending, the sky is not falling, and when all is said and done, the hype from MS06-040 may do more damage than any worm based off of it will.