Summary
In December 2023, Secureworks® Counter Threat Unit™ (CTU) researchers found a way to exploit a security issue in Microsoft Entra ID access reviews, which help administrators audit who has access to sensitive resources in an organization. The flaw allowed any multi-tenant service principal registered under a victim's tenant to modify access reviews through a vulnerable API, despite lacking necessary permissions.
CTU™ researchers reported the issue to Microsoft in December 2023. Microsoft confirmed that privilege escalation was possible and assigned an 'important' severity rating. On January 15, 2024, Microsoft notified CTU researchers that the issue had been fixed.
Access reviews
Access reviews are a feature under Microsoft Entra ID Governance, and they play a vital role in Microsoft Entra ID. Deploying access reviews enables organizations to ensure that users have appropriate roles, memberships, and permissions (see Figure 1).
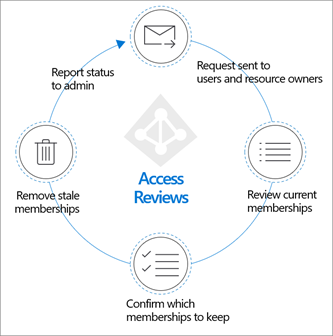
Figure 1. Access reviews process. (Source: https://learn.microsoft.com/en-us/entra/id-governance/deploy-access-reviews)
Discovery
CTU researchers created a scanner add-on that substitutes administrator access tokens with tokens of a multi-tenant service principal to demonstrate the potential impact (see Figure 2). This choice underscores the risk because multi-tenant service principals, as external applications, are significantly more detached from the tenant than internal service principals. This detachment makes them less trustworthy, as they are not managed within the customer's tenant, their credentials are not transparent, and their ownership is unclear. The focus on multi-tenant service principals is deliberate. Their registrations cannot be monitored by the target organization, so attackers can control credentials outside the target tenant's control. Our scanner add-on leverages MITMProxy for transparent proxying. It then forwards the request to an internal service that is based on Node.js, which handles the logic for token swapping and reissues the request to APIs related to Entra ID.
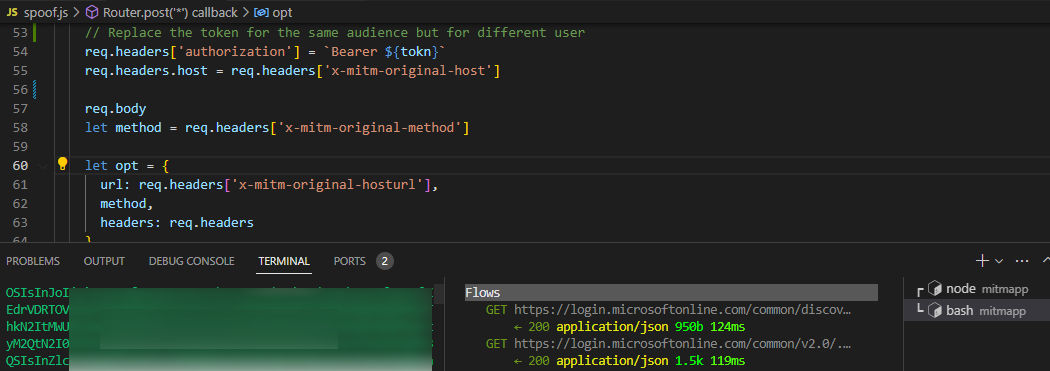
Figure 2. Scanner add-on to swap tokens. (Source: Secureworks)
In this process, we observed that the ‘api . accessreviews . identitygovernance . azure . com' endpoint, which is associated with the access reviews API, correctly denies authorization for user-based tokens but failed to do the same for tokens issued to the service principal. We continued our experiment by developing a proof of concept to determine if malicious access would be recorded in the Entra ID audit logs. As illustrated in Figure 3, the request made by the service principal led to an ‘update access review' for an existing access review. This event should not have been possible, as the service principal was not assigned any permissions (see Figure 4).
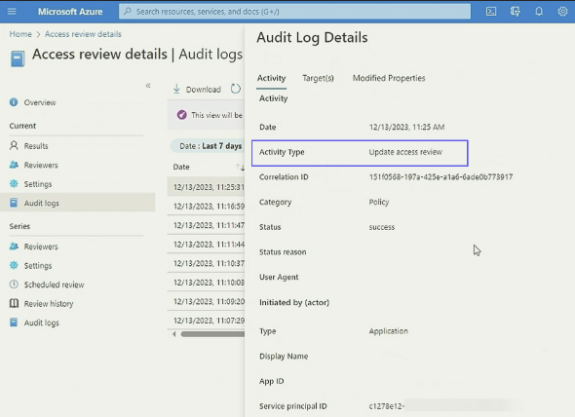
Figure 3. Arbitrary modification to update access review. (Source: Secureworks)
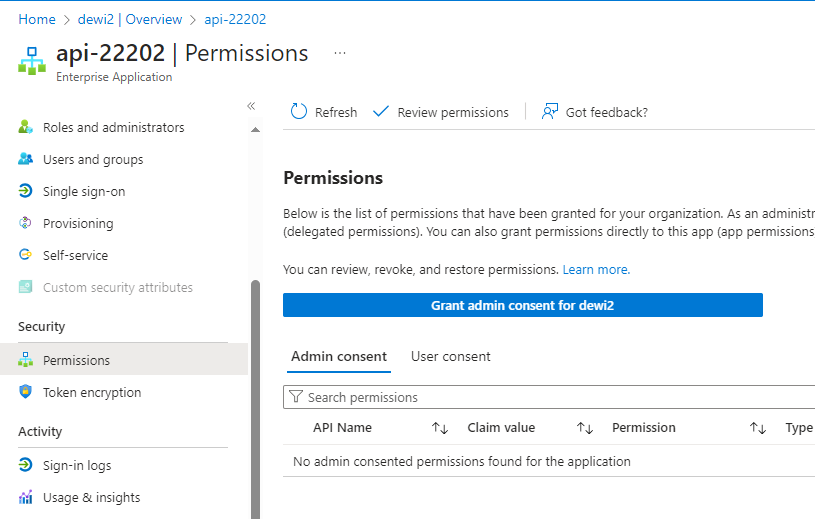
Figure 4. No roles assigned for the service principal. (Source: Secureworks)
Impact
This attack could impair an organization's ability to oversee access to other services that the threat actor wanted to hide. For example, an attacker could have exploited this vulnerability to hide accesses they obtained through a compromised account, which would have otherwise been monitored via the access review.
Communication with Microsoft
CTU researchers reported this issue to the Microsoft Security Response Center (MSRC) on December 15, 2023. On January 15, 2024, MSRC notified CTU researchers that they had released a fix, which consisted of ensuring that API endpoints checked the service principal permissions. CTU researchers confirmed that the update addressed the issue.
Conclusion
This research highlighted the need for automated tooling to search for vulnerabilities across multiple API endpoints. Although automation helped CTU researchers discover this vulnerability, development of a full exploit required additional knowledge. Given that this issue was API vulnerability, there were no Entra ID Governance configuration options that would protect customers from the attack. There are no indications that threat actors exploited this vulnerability.