Summary
Secureworks® Counter Threat Unit™ (CTU) researchers investigated reports that the LV ransomware had the same code structure as REvil. This overlap could indicate that the GOLD SOUTHFIELD cybercriminal threat group that operates REvil sold the source code, that the source code was stolen, or that GOLD SOUTHFIELD shared the code with another threat group as part of a partnership. CTU™ analysis confirmed that the GOLD NORTHFIELD threat group, which operates LV, replaced the configuration of a REvil v2.03 beta version to repurpose the REvil binary for the LV ransomware.
CTU researchers have not observed LV ransomware advertisements on underground forums as of this publication. However, variations in partner and campaign IDs across LV configurations and the practice of naming and shaming victims could indicate that GOLD NORTHFIELD is launching a ransomware-as-a-service (RaaS) offering.
LV packer
The packed LV ransomware samples identified by CTU researchers appear to use the same basic crypter. Figure 1 shows the entire contents of the packed executable's main function, which contains five of the executable's nine functions.

Figure 1. Main function for the packer used to unpack and execute LV ransomware. (Source: Secureworks)
The packed executable stores the LV ransomware binary as RC4-encrypted data within a section named 'enc' (see Figure 2).
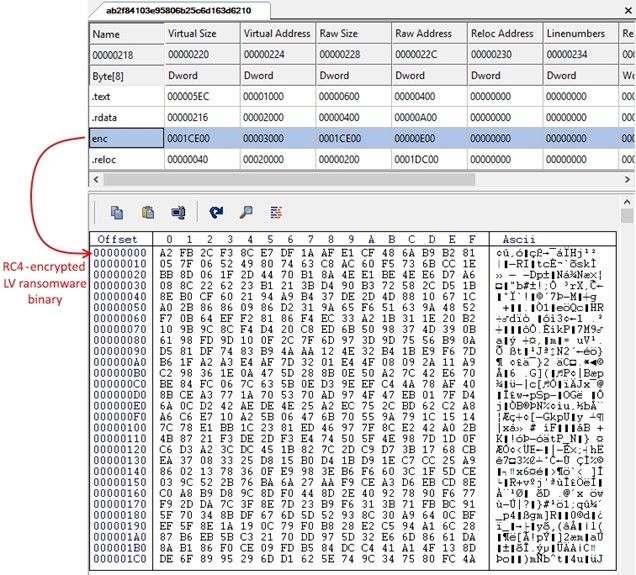
Figure 2. Encrypted LV ransomware binary stored in the enc section of the packer executable. (Source: Secureworks)
The packed samples analyzed by CTU researchers use the hard-coded "kZlXjn3o373483wb6ne1LIBNWD3KWBEK" key to decrypt the contents of the enc section. The "This program cannot be run in DOS mode" string is removed from decrypted binaries' PE headers (see Figure 3).

Figure 3. Strings removed from header of decrypted LV binary. (Source: Secureworks)
Once decrypted, the ransomware binary is copied into a new memory allocation created with Read/Write/Execute (RWE) access rights. The packer then executes the unpacked ransomware binary by jumping to the entry point defined in the PE header.
Origin and configuration
The code structure and functionality of the LV ransomware sample analyzed by CTU researchers are identical to REvil. The version value in the LV binary is 2.02, its compile timestamp is 2020-06-15 16:24:05, and its configuration is stored in a section named '.7tdlvx'. These characteristics align with REvil 2.02 samples first identified in the wild on June 17, 2020. The LV sample also contains a code segment that is unique to REvil 2.03. The only purpose of this code segment in REvil binary is to taunt prominent security researchers. LV replaces the insults with the space character (see Figure 4).

Figure 4. LV code segment duplicating REvil 2.03 code but replacing strings with spaces. (Source: Secureworks)
This type of code modification suggests that GOLD NORTHFIELD does not have access to REvil's source code. The threat actors likely used a hex editor to remove potentially identifying characteristics from the binary to conceal that LV is a repurposed version of REvil. The hard-coded 2.02 version value and the unique REvil 2.03 code suggests that GOLD NORTHFIELD used a beta version of REvil 2.03 as the basis for LV ransomware.
REvil binary repurposing
The GOLD NORTHFIELD threat actors replaced the REvil configuration stored within the binary's '.7tdlvx' section with their own configuration. Successful replacement required the format of the REvil and LV configurations to be identical. Figure 5 shows the LV configuration extracted from the REvil binary. It is a JSON-formatted string containing key elements utilized by REvil (e.g., sub, net, dmn, pk).

Figure 5. LV configuration. (Source: Secureworks)
GOLD NORTHFIELD then had to RC4-encrypt the LV configuration with a 32-byte key. To bypass REvil's anti-tamper control that ensures the integrity of the configuration (see Figure 6), GOLD NORTHFIELD also had to generate a CRC32 hash of the updated encrypted configuration and then replace the hard-coded precalculated CRC32 hash stored in the binary with the updated configuration's CRC32 hash. These changes are necessary because the REvil code calculates the configuration's CRC32 hash value at runtime and terminates if the calculated and hard-coded hashes do not match.

Figure 6. Configuration anti-tamper control implemented in the REvil binary. (Source: Secureworks)
Finally, GOLD NORTHFIELD could add the RC4 key used to encrypt the configuration, the CRC32 hash of the encrypted configuration, the length of the encrypted configuration, and the encrypted configuration itself to the REvil binary via the identified configuration section (.7tdlvx) in the defined order (see Figure 7).

Figure 7. REvil configuration structure when stored in the binary. (Source: Secureworks)
If done correctly, the binary will successfully execute using LV's updated configuration. Files on the victim's system will be encrypted with session keys that are protected by LV's public key, and victims will be directed to LV's ransom payment site via the updated ransom note.
Configuration comparisons
CTU analysis of numerous LV configurations led to several insights:
- The dmn configuration element was consistently assigned an empty string (e.g., "dmn": ""). In a standard REvil configuration, this value contains over 1,200 command and control (C2) domains that the malware uses to communicate infection information to the threat actor. This information can include the ransomware version, session keys used for file encryption, public key used to encrypt the session keys, and victims' details such as username, hostname, and region. Although the net configuration key is set to False in the LV samples, removal of all domains from the dmn configuration key ensures that LV ransomware victims' data is not sent to REvil C2 servers. Removing these domains rather than replacing them with C2 domains operated by GOLD NORTHFIELD suggests that the group may not be capable of maintaining C2 infrastructure or developing the backend automation required to process and track victims' data.
- The partner ID (pid) varied in some of the configurations. This variation suggests that GOLD NORTHFIELD could leverage this element to track individual RaaS partners, which is how GOLD SOUTHFIELD uses this element. However, LV configurations had matching bcrypted partner IDs across different configurations. Although the pid is hashed, a partner could be tracked using the bcrypted hash value. REvil generates a new bcrypted hash for each configuration, making partner tracking impossible.
- The campaign ID (sub) varied in some of the configurations. GOLD NORTHFIELD might have adopted GOLD SOUTHFIELD's approach of using this element to track individual campaigns or configuration builds.
- The attacker's public key (pk) was different in each configuration. GOLD NORTHFIELD needs a master encryption key pair to decrypt files encrypted by LV ransomware. The pk rotation across configurations suggests the creation of a unique key pair for each victim, which prevents file decryption across multiple victims if the attacker's private key is obtained.
- The only ransom note (nbody) change from the standard REvil format was replacing REvil's ransom payment Tor domain with LV's domain (see Figure 8).

Figure 8. LV ransom note. (Source: Secureworks)
Ransom payment site
After accessing the ransom payment site, victims are presented with a basic form that requests the key from the ransom note (see Figure 9).
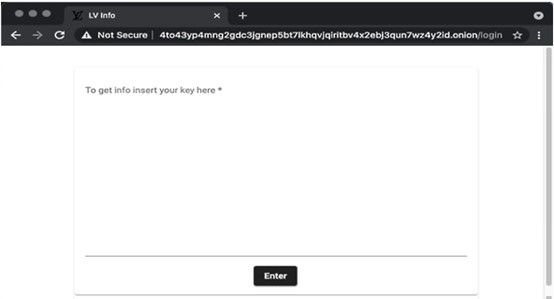
Figure 9. LV ransom payment site key submission form. (Source: Secureworks)
Previous CTU analysis of the REvil ransom note determined that this key represents information about the ransomware infection that has been encrypted and then Base64-encoded:
- Compromised host details:
- CPU architecture (32-bit or 64-bit)
- Fixed-drive information (drive letter, drive type, total size, and free space)
- Workgroup/domain
- Configured locale, and whether it aligns with one of the specified countries where the malware cannot be used
- Hostname
- Operating system
- Ransomware details:
- Configured partner ID
- Threat actor's configured public key
- Encrypted session private key
- Configured campaign ID
- Unique ID based on host's volume serial number and CPUID
- Victim's username
- Ransomware version
As of this publication, CTU researchers have identified three ransom payment Tor domains specified in LV ransom notes. Each of the domains successfully loads the landing page, but CTU researchers' attempts to submit the key from the ransom note returned HTTP errors (see Table 1).
| Ransom payment domain | HTTP error |
| 4to43yp4mng2gdc3jgnep5bt7lkhqvjqiritbv4x2ebj3qun7wz4y2id . onion | 502 - Bad Gateway |
| l55ysq5qjpin2vq23ul3gc3h62vp4wvenl7ov6fcn65vir7kc7gb5fyd . onion | 403 - Forbidden |
| 36yvrbzhbzyuzia7qxahsaw2yizcr3heljw2jtde3smyuhkokjnb2sid . onion | 403 - Forbidden |
Table 1. LV ransom payment domains and HTTP errors.
The HTTP errors may be caused by anti-analysis controls implemented by GOLD NORTHFIELD to inspect characteristics of the submitted key for suspicious or undesirable activity. They may also indicate that the threat group is struggling to maintain resilient infrastructure due to lack of skill or insufficient resources.
When key submission is successful, the site displays a page showing the ransom amount in U.S. dollars and how much time the victim has to pay the ransom before sensitive data is disclosed (see Figure 10). The page also includes a live chat function for the victim to interact with the threat actors.

Figure 10. LV ransom payment site. (Source: ID Ransomware blog)
Leak sites
CTU researchers identified two LV ransomware leak sites that have an identical structure but appear to be operated independently. The sites listed victims during the same timeframe, but only one victim was listed on both sites (see Figure 11). It is unclear why GOLD NORTHFIELD would operate two leak sites.

Figure 11. Victims added to LV leak sites between March 7 and April 14, 2021. Only one victim (highlighted in yellow) was listed on both sites. (Source: Secureworks)
The leak sites name and shame victims. The threat actors coerce the victims into paying the ransom by threatening to publish their sensitive information (see Figure 12).

Figure 12. LV leak site. (Source: Secureworks)
GOLD NORTHFIELD typically threatens to publicly release sensitive information if victims do not initiate contact within 72 hours. The threat actors post screenshots of the victim's sensitive files on the leak sites to support their claims. However, it appears that none of the victims' data has been released as of this publication. It is unclear if victims paid the ransom and the threat actors just keep the full list of victims on the leak site as evidence of their conquests.
Conclusion
CTU analysis revealed that the LV ransomware is not a distinct ransomware family; it is repurposed REvil ransomware. By modifying the binary of a prolific ransomware family, the GOLD NORTHFIELD threat actors significantly expedited their maturity within the ransomware ecosystem. Without expending resources on ransomware development, the group can operate more efficiently than its competitors while still offering a best-in-class ransomware offering, ultimately resulting in a more profitable business model. GOLD NORTHFIELD's unauthorized manipulation of REvil will likely prompt GOLD SOUTHFIELD to implement additional anti-tamper controls and modify configuration storage and processing to impede future attempts to overwrite the REvil configuration.
It is too early in GOLD NORTHFIELD's evolution to evaluate the threat it poses. The ability to repurpose the REvil binary suggests that the threat actors have technical capabilities. Additionally, the complexity required for this repurposing and the configuration variations across LV samples suggest that GOLD NORTHFIELD may have automated the process. Although a RaaS for the LV ransomware could provide direct competition for GOLD SOUTHFIELD's RaaS offering, the lack of a reliable and organized infrastructure needed to operate a successful RaaS offering suggests that GOLD NORTHFIELD has to expand its capabilities and resources to compete with other ransomware operations.
Threat indicators
The threat indicators in Table 2 can be used to detect activity related to LV ransomware. The domains may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| 6f0b92488eae3ccefc0db7a6b0d652ee | MD5 hash | Packed LV ransomware |
| 45adc4224d2ae9fd75b19417ca6913515c5222ee | SHA1 hash | Packed LV ransomware |
|
457936c28938616495836c472b3389a0870574bee6 a5dc026d5bd14979c6202c |
SHA256 hash | Packed LV ransomware |
| 58682ca2a49ed4bfb8d5aaf76cf0fade | MD5 hash | Packed LV ransomware |
| b00d58e9ffd784db86e77a6a31c76e1bd58ba79b | SHA1 hash | Packed LV ransomware |
|
ab2f84103e95806b25c6d163d6210a21fb3283cd29 dddee917d33e654d733425 |
SHA256 hash | Packed LV ransomware |
| 7b1cf5fc0bfb1021fe0e14e518c32026 | MD5 hash | Packed LV ransomware |
| 380cd990a9e5aec85233ef1d2635dc04d5a96e6b | SHA1 hash | Packed LV ransomware |
|
d4fc76bf8baae39feec23990857c52199e80265a34 faeece0d830eb77645c944 |
SHA256 hash | Packed LV ransomware |
| a4331ff805b0a8f2a2892777c224b65e | MD5 hash | Packed LV ransomware |
| 2c5521077dd1a6f5f3558351370880aee9ab7c71 | SHA1 hash | Packed LV ransomware |
|
329983dc2a23bd951b24780947cb9a6ae3fb80d5ef 546e8538dfd9459b176483 |
SHA256 hash | Packed LV ransomware |
| fa8117afd2dbd20513522f2f8e991262 | MD5 hash | Packed LV ransomware |
| f7b876edb8fc0c83fd8b665d3c5a1050d4396302 | SHA1 hash | Packed LV ransomware |
|
78b592a2710d81fa91235b445f674ee804db39c8cc 34f7e894b4e7b7f6eacaff |
SHA256 hash | Packed LV ransomware |
| d1c9c12e08c8e2111da989e2318b1c42 | MD5 hash | Unpacked LV ransomware |
| d0c7f3c8de28d0fccec9d4925afeb5fa9dd62b5d | SHA1 hash | Unpacked LV ransomware |
|
e25eaaac03aa958688cbe950275156169eb4955e14 5bc9627fcbfb36cd832a84 |
SHA256 hash | Unpacked LV ransomware |
|
4to43yp4mng2gdc3jgnep5bt7lkhqvjqiritbv4x2e bj3qun7wz4y2id.onion |
Domain name | LV ransomware payment site |
|
l55ysq5qjpin2vq23ul3gc3h62vp4wvenl7ov6fcn6 5vir7kc7gb5fyd.onion |
Domain name | LV ransomware payment site |
|
36yvrbzhbzyuzia7qxahsaw2yizcr3heljw2jtde3s myuhkokjnb2sid.onion |
Domain name | LV ransomware payment site |
|
rbvuetuneohce3ouxjlbxtimyyxokb4btncxjbo44f bgxqy7tskinwad.onion |
Domain name | LV ransomware leak site |
|
4qbxi3i2oqmyzxsjg4fwe4aly3xkped52gq5orp6ef pkeskvchqe27id.onion |
Domain name | LV ransomware leak site |
Table 2. Indicators for this threat.
References
Gillespie, Michael (@demonslay335). "Sodinokibi." Twitter, November 13, 2020, 5:24 pm. https://twitter.com/demonslay335/status/1327376936935493635
Ivanov, Andrew. "LV Ransomware." ID Ransomware blog. November 13, 2020. Original (in Russian): https://id-ransomware.blogspot.com/2020/10/lv-ransomware.html. English translation: https://translate.google.com/translate?hl=en&sl=ru&u=https://id-ransomware.blogspot.com/2020/10/lv-ransomware.html&prev=search&pto=aue
Secureworks. "GOLD NORTHFIELD." Accessed June 1, 2021. https://www.secureworks.com/research/threat-profiles/gold-northfield
Secureworks. "GOLD SOUTHFIELD." Accessed April 22, 2021. https://www.secureworks.com/research/threat-profiles/gold-southfield
Secureworks. "REvil/Sodinokibi Ransomware." September 24, 2019. https://www.secureworks.com/research/revil-sodinokibi-ransomware
xiaopao (@Kangxiaopao). "LV ransomware." Twitter, October 23, 2020, 5:43 am. https://twitter.com/Kangxiaopao/status/1319575086995652609