- Author: Pat Litke and Joe Stewart with assistance from Ben Small, Dell SecureWorks Counter Threat Unit™ Threat Intelligence
- Date: 26 February 2014
Introduction
Bitcoin, a digital currency and payment system introduced in 2009, has been subject to an increasing amount of attention from thieves. Although the system itself is protected by strong cryptography, thieves have stolen millions of dollars of bitcoin[i] from victims by exploiting weaknesses in Bitcoin private key storage systems.
Since Bitcoin's introduction, an increasing number of alternative digital currencies (altcoins) have been created, based on the original Bitcoin client's source code. Even though none of these altcoins have approached the per-coin value of Bitcoin, some have achieved total market caps measuring in the millions of dollars. As a result, these altcoins have also been targeted for theft.
Mass theft of cryptocurrency is usually accomplished through the hacking of exchanges or marketplaces. These thefts are typically well-publicized, and the total number of stolen coins is known. However, another category of Bitcoin theft targets individual users' wallets or exchange accounts via malware such as general-purpose remote access trojans (RATs) or specialized cryptocurrency-stealing malware (CCSM). Due to the skyrocketing value of cryptocurrencies since the beginning of 2013 and the relative simplicity of coding malware and tools to steal cryptocurrency, the Dell SecureWorks Counter Threat Unit(TM) (CTU) research team predicts that CCSM will become one of the fastest-growing categories of malware.
CCSM classification project
To understand the scope of this new threat, CTU researchers embarked on a project to obtain and classify as many CCSM samples as possible. Researchers scanned incoming malware streams with YARA rules, searching for samples that refer to known cryptocurrency software wallet filenames and locations. These samples were classified into families based on similarity. As of this publication, there are more than 100 unique families of malware on the Internet with functionality to steal wallet files or to steal cryptocurrency using other means.
Overall trends
Figure 1 shows the increase in the Windows-compatible CCSM over time. This chart tracks only Windows malware because the Windows portable executable format includes a timestamp in the file headers showing exactly when the malware was compiled. Most malware authors do not bother to alter this timestamp post-release, so it a reasonable and reliable indicator of when a particular sample was created. This chart shows the relationships between average monthly Bitcoin price, new family emergence, and overall total number of families. These variables show a correlation between malware emergence and the price (acceptance) of the currency.
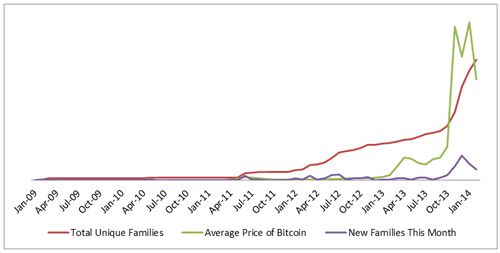
Figure 1. The correlation between Bitcoin price, new malware emergence, and total threat of cryptocurrency-stealing malware. (Source: Dell SecureWorks)
The trend shown in Figure 1 closely follows the overall price trend of Bitcoin. As Bitcoin has become more valuable, more malware authors are targeting it. The record-breaking highs in Bitcoin value from the end of 2013 into 2014 have been accompanied by record-breaking numbers of new CCSM families.
Popularity of coins in CCSM
All CCSM analyzed by CTU researchers targeted Bitcoin. Figure 2 shows the distribution of CCSM-targeted altcoins between January 2009 and the middle of February, 2014.

Figure 2. The distribution of altcoins targeted by CCSM between January 2009 and mid-February, 2014. (Source: Dell SecureWorks)
Figure 3 shows the overall ratio of samples belonging to each malware family. A few malware families seem to be in widespread distribution, while others may have only one or two variants. The "Unclassified" group represents cryptocurrency malware that CTU researchers have not classified as of this publication. The "Miscellaneous" group includes the cryptocurrency malware families the CTU research team has discovered that would not fit into the chart.
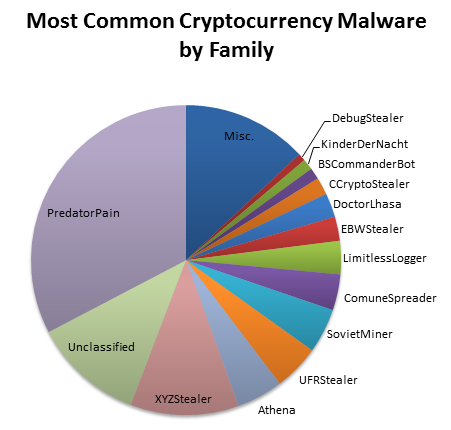
Figure 3. The overall ratio of discovered samples belonging to each malware family. (Source: Dell SecureWorks)
CCSM categories
Wallet stealer
The most common type of CCSM is the wallet stealer, a category that includes nearly every family of CTU-analyzed CCSM. This type of malware searches for "wallet.dat" or other well-known wallet software key storage locations, either by checking known file locations or by searching all hard drives for matching filenames. Typically, the file is uploaded to a remote FTP, HTTP, or SMTP server where the thief can extract the keys and steal the coins by signing a transaction, transferring the coins to the thief's Bitcoin/altcoin address.
Most cryptocurrency security guides recommend protecting the wallet with a strong passphrase, preventing the thief from decrypting and using the private keys if the file is stolen. To counter this protection, many of the analyzed wallet-stealer malware families use a keylogger or clipboard monitor to obtain the wallet file's passphrase and send it to the thief.
Credential stealer
Many wallet-stealer families also steal credentials for various web-based wallets, such as Bitcoin exchanges. Some individuals keep a significant amount of bitcoin or other currency in exchanges to trade on price movements. Malware authors are aware of this activity, and many victims have reported that their exchange wallets were emptied without their authorization. In most cases, it is impossible to know exactly what malware was used in the theft, because a full forensic analysis of the victim's hard drive is rarely performed.
Many exchanges have implemented two-factor authentication (2FA) using one-time PINs (OTP) to combat unauthorized account logins. However, advanced malware can easily bypass OTP-based 2FA by intercepting the OTP as it is used and creating a second hidden browser window to log the thief into the account from the victim's computer. Simultaneously, the malware displays a fake "authentication failed" message and blocks the victim's access to the website while the thief empties the account. CTU researchers have not observed a verified example of this type of attack against cryptocurrency exchanges. However, this technique has been successfully used against online banking sites for several years, and it is only a matter of time before CCSM uses this approach.
Man in the middle
CTU researchers have observed at least one family of CCSM that does not exfiltrate wallet files or private keys. Instead, it acts as a "man in the middle," altering the recipient address of a transaction before it is signed. The observed sample runs in the background, monitoring the contents of the clipboard. The malware checks new data in the clipboard for a valid Bitcoin address. If the data is a valid address, the malware replaces it with the thief's Bitcoin address. Victims who do not notice the replacement send the bitcoins to the thief.
RPC automation
Bitcoin and altcoin "reference client" software includes remote procedure call (RPC) functionality, which allows another program to interact with the wallet software. In many cases, a thief with access to this functionality could connect to a running client on a local TCP port and steal the balance of an unencrypted wallet using only two commands (three if the wallet is encrypted and the malware has obtained the passphrase). CTU researchers have not witnessed any CCSM malware taking advantage of this technique as of this publication. It would be difficult to detect this type of theft from a network standpoint, as the transaction would look like any authorized transaction. Another advantage to this technique is that it requires no external command and control (C2) or exfiltration server that can be shut down or blocked.
Detection rates
Across the CCSM samples analyzed by CTU researchers, the average unweighted detection rate across all major antivirus (AV) vendors was 48.9%. Figure 4 lists the major CCSM families classified by the CTU research team and their respective detection rates averaged across all major AV vendors.
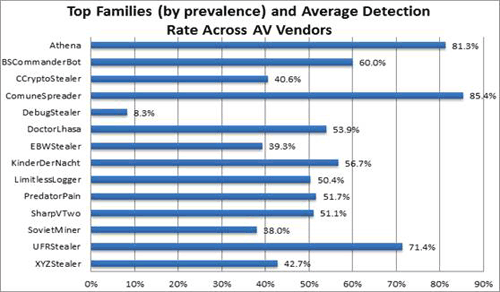
Figure 4. Top CCSM families and their detection rate across AV vendors as of February 20, 2014. (Source: Dell SecureWorks)
Wallet protection
Client software choices
When the private keys for a cryptocurrency are stored on a computer connected to the Internet, the potential for theft exists. For Bitcoin there are alternative wallets, such as Armory and Electrum, which can protect against theft-by-malware by using a split arrangement for key storage. One computer, disconnected from any network, runs a copy of the software and holds the private key that can sign transactions. A second computer connected to the Internet holds only a master public key of which addresses belong to the offline wallet. This computer can generate transactions, but it cannot sign them because it does not have the private key. A user wishing to transfer coins generates an unsigned transaction on the online computer, carries the transaction to the offline computer, signs the transaction, and then carries it to the online computer to broadcast the transaction to the Bitcoin network.
Using a split Armory or Electrum wallet can make processing transactions much safer, although the user must still verify the transaction details to ensure malware on the online computer has not altered the transaction before it is signed. Unfortunately, no such clients currently exist for altcoins, although the need for them is recognized and bounties have been offered for their development.
Hardware wallets
Using two computers in a split arrangement where transactions are carried via "sneakernet" is relatively secure, but the logistics are complicated. A much more convenient method would be to use a dedicated hardware device to store the private keys and verify transactions without the possibility of theft. These devices are already in development, with one (the "Trezor" wallet) due to be shipped within the first quarter of 2014.
Transaction integrity verification
Hardware wallets work well for local transactions but not for safely interacting with a remote website on a potentially infected computer. Securely verifying a transaction that has transited a potentially compromised waypoint requires an offline device that can display the details of the transaction before it is processed. Public-key cryptography signs the transaction data on the bank's server before the data is sent to the user. The offline device can verify the signature of the transaction and determine if any changes occurred in transit. If the transaction shows no tampering, the offline device generates a one-time code that authenticates the transaction. This transaction integrity verification (TIV) should become standard for all financial entities, including institutions and sites that accept cryptocurrencies.
Conclusion
After observing CCSM, CTU researchers drew the following conclusions:
- Encrypting the wallet file is ineffective against malware that uses keyboard or clipboard logger functionality.
- Two-factor authentication is ineffective against malware that uses modern banking malware techniques.
- Antivirus is mostly ineffective against newly created malware, especially one-off, customized, single-file stealers.
- On an infected system, the malware can do anything a user can do. It can pretend to be the user to a remote website, and it can pretend to be the remote website to the user.
As discussed in Enterprise Best Practices for Cryptocurrency Adoption, wallet security is the most pivotal aspect to keeping funds secure. Implementing the practices outlined in that publication will mitigate most, if not all, of the current threats to cryptocurrency wallets.
Appendix
Table 1 lists the most commonly observed malicious filenames in the CTU research team's sample set.
| 1.exe | 11.exe | 111.exe | 112.exe |
| 12.exe | 123.exe | 141.exe | 1414.exe |
| 20-Jun-11-00f09f5e0c195e8-Cam.exe | 4.exe | 45.exe | aa.exe |
| aaa.exe | admin.exe | amin.exe | as.exe |
| asd.exe | Asphyxia v8.0.exe | Asphyxia v9.0.exe | Auto-Proxy Locator v1.0 - www.WizNest.info.exe |
| Bitcoin.exe | Bitcoin_Generator.exe | Bitcoin_s.exe | Bitcoin-generator.exe |
| Clash Of Clans Hack.exe | Clash of Clans Hack.exe | done.exe | ds.exe |
| etheretdriver.exe | ethernetdriv1er.exe | ethernetdriver.exe | ethernetdriver11.exe |
| file-3831235_exe | file-3831251_exe | file-6441495_exe | file-6441496_exe |
| file-6459250_exe | file-6459258_exe | GameMasterStory v111.exe | GPU_Cluster_Miner.exe |
| GPUClusterMiner.exe | GuiMiner.exe | Hinjector109.exe | HinjectorV109.exe |
| iMiner.exe | Install.exe | install.exe | keygen.exe |
| Keygen.exe | lan.exe | ll.exe | lol.exe |
| microsoft.exe | Microsoft.exe | Minecraft Brute Toolkit.exe | Minecraft.exe |
| MinecraftSP.exe | Miner.exe | minerd64_sse2.exe | minerd64_sse3.exe |
| ms.exe | mz_74.exe | nacl64.exe | NSWallet.exe |
| octworm.exe | one.exe | pi.exe | pic.exe |
| po.exe | pro.exe | pror.exe | Rs DDoSer ~RsMultiHackTeam.exe |
| RsboxingDdos2.exe | RsboxingDdos3.exe | rsdf.exe | Run_wind.exe |
| Runescape Money Hack (1).exe | Runescape Money Hack.exe | s.exe | sample.exe |
| samples.exe | sdf.exe | serve2r.exe | server t.exe |
| server.exe | server1.exe | Shad's Billionaire Guide.exe | sof.exe |
| soft.exe | srvhost.exe | steal.exe | Steal.exe |
| stealer.exe | Stealer.exe | stealer1.exe | stealerr.exe |
| steam.exe | stub.exe | stub2.exe | svchost.exe |
| test.exe | test1.exe | test123.exe | ustream.exe |
| VIDEOMAKERpro.exe | view bot.exe | w.exe | Wallet.exe |
| Windows Update.exe | WindowsUpdate.exe | Winupdate.exe | winupdate.exe |
| wlan.exe | worm.exe | wormz.exe | ws.exe |
| ws1.exe | ws4.exe | ww.exe |
Table 1. Common filenames in malware samples.
Endnotes
[i] Bitcoin (capitalized) refers to the protocol, software, and community, while bitcoins (lowercase) are currency units.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
