Summary
During 2017, the cryptocurrency market grew nearly 20-fold, reportedly increasing from approximately $18 billion to more than $600 billion (USD). Those gains amplified threat actors' interest in accessing the computing resources of compromised systems to mine cryptocurrency. Secureworks® incident response (IR) analysts responded to multiple incidents of unauthorized cryptocurrency mining in 2017, and network and host telemetry showed a proliferation of this threat across Secureworks managed security service clients. Financially motivated threat actors will continue to use malware infections to deploy cryptocurrency mining software for as long as it remains profitable.
Compared to complete loss of availability caused by ransomware and loss of confidentiality caused by banking trojans or other information stealers, the impact of unauthorized cryptocurrency mining on a host is often viewed as more of a nuisance. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively.
Furthermore, the deployment and persistence of unauthorized cryptocurrency mining software in an environment reflects a breakdown of effective technical controls. If activity of this nature can become established and spread laterally within the environment, then more immediately harmful threats such as ransomware could as well. The technical controls used to mitigate the delivery, persistence, and propagation of unauthorized cryptocurrency miners are also highly effective against other types of threat.
Key points
- This threat can have a significant impact. If critical and high-availability assets are infected with cryptocurrency mining software, then computational resources could become unusable for their primary business function. Heavy processing loads could accelerate hardware failure, and energy costs could be significant for an organization with thousands of infected hosts.
- Unauthorized cryptocurrency mining indicates insufficient technical controls. If it is possible for an initial malware infection to deliver and spread cryptocurrency miners within an environment without being detected, then that same access vector could be used to deliver a wide range of other threats.
- The threat of cryptocurrency mining malware increased in 2017. Financially motivated threat actors are drawn to its low implementation cost, high return on investment, and arguably lower risk of law enforcement action than traditional malware because the impact is less visible or disruptive.
- The upward trend of cryptocurrency miner infections will continue while they offer a positive return on investment. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection and remediation.
- Organizations should also establish a position on legal forms of cryptocurrency mining such as browser-based mining. While this form of mining has a legitimate use, organizations might still consider it an unacceptable use of corporate resources.
Cryptocurrency mining economics
The idea of using a decentralized electronic payment method that relies on cryptographic proof, known as a cryptocurrency, has existed since at least 2008 when an anonymous author using the pseudonym 'Satoshi Nakamoto' published a paper outlining the Bitcoin concept. Although Bitcoin was reportedly used to purchase goods for the first time in May 2010, serious discussions of its potential as an accepted form of currency began in 2011, which coincided with the emergence of other cryptocurrencies. There were approximately 1,370 cryptocurrencies as of December 2017 with new currencies added every day, although many cryptocurrencies cannot be mined. The price and volatility of popular cryptocurrencies surged in late 2017 (see Figure 1).
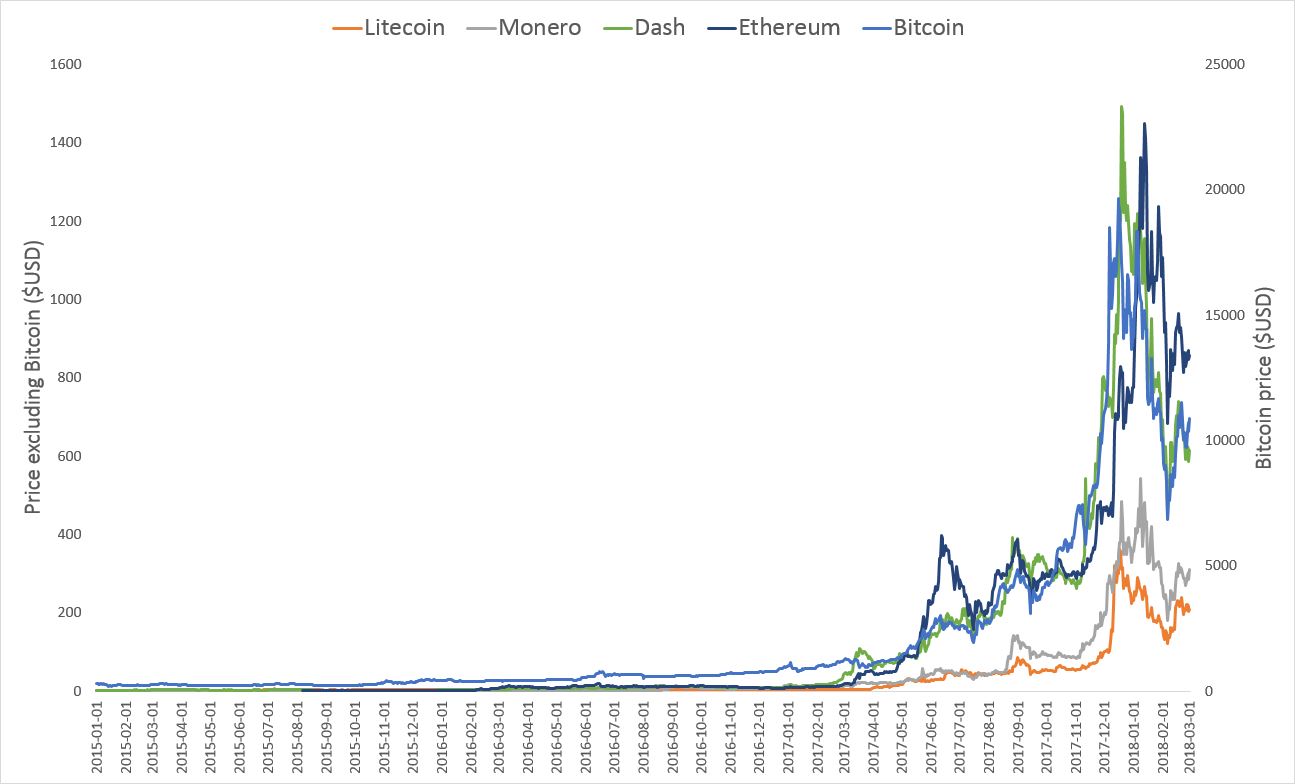
Figure 1. Market price of various cryptocurrencies from January 2015 to March 2018. (Source: CoinGecko)
In cryptocurrency 'mining,' computational power is expended to add transactions to a public ledger, or blockchain. Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners. Consequently, cryptocurrency mining can be profitable for as long as the reward outweighs the hardware and energy costs. Bitcoin's reward rate is based on how quickly it adds transactions to the blockchain; the rate decreases as the total Bitcoin in circulation converges on a predefined limit of 21 million. Most other cryptocurrencies are modeled on Bitcoin's architecture and concepts, but they may modify features such as transaction privacy or the predefined circulation limit to attract potential investors.
Individuals who want to mine a cryptocurrency often join a mining 'pool.' Adding transactions to the blockchain, thereby receiving a reward, requires computers to compete to be the first to solve a complex mathematical puzzle. Aggregating computing power, and then splitting any rewards received among the contributors, is a more profitable way of mining cryptocurrency than individual efforts. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications.
Cryptocurrency mining criminality
Cryptocurrency is attractive to financially motivated threat actors as a payment method and as a way to generate revenue through mining:
- The decentralized nature of many cryptocurrencies makes disruptive or investigative action by central banks and law enforcement challenging.
- Multiple cryptocurrencies promote anonymity as a key feature, although the degree of anonymity varies. For example, security researchers were able to analyze publicly viewable records of Monero payments made to the Shadow Brokers threat group for their leaked tools.
- For criminals with control of an infected system, cryptocurrency mining can be done for free by outsourcing the energy costs and hardware demands to the victim. Access to networks of infected computers can be sold as a service. Cryptocurrency miners can be combined with threats such as information stealers to provide additional revenue.
- Organizations may not detect and respond quickly to cryptocurrency mining because they consider it less harmful and immediately disruptive than other malicious revenue-generating activity such as ransomware. As a result, threat actors have more time to generate revenue and law enforcement may take longer to react.
Reports of Bitcoin mining as a criminal activity emerged in 2011 as Bitcoin became widely known. In August 2011, the Secureworks Counter Threat Unit™ (CTU) research team analyzed a peer-to-peer botnet installing Bitcoin mining software. In July 2014, CTU™ researchers observed an unknown threat actor redirecting cryptocurrency miners' connections to attacker-controlled mining pools and earning approximately $83,000 in slightly more than four months. Between 2014 and 2017, there were several notable developments in cryptocurrency mining malware:
- Cryptocurrency mining malware developers quickly incorporated highly effective techniques for delivery and propagation. The Apache Struts vulnerability used to compromise Equifax in mid-2017 was exploited as a delivery mechanism for the Zealot multi-platform campaign that mined Monero cryptocurrency. The SMBv1 vulnerabilities disclosed by the Shadow Brokers threat group in April 2017 and exploited by the WCry ransomware in May 2017 were used to deliver the Adylkuzz mining malware as early as late-April 2017. The combination of SMBv1 exploits and the Mimikatz credential-theft tool used by the NotPetya malware in June 2017 has been used to distribute Monero mining software.
- Mining malware has increasingly become a multi-platform threat, as financially motivated threat actors have deployed it wherever they can generate the highest return on investment. There are numerous examples of miners that work on Windows, Linux and mobile operating systems.
- Browser-based mining software, such as the CoinHive software launched in mid-September 2017, allows website owners to legitimately monetize website traffic. However, as shown in Figure 2, threat actors can also use CoinHive to exploit vulnerable websites, which impacts both the website owner and visitors. Techniques that circumvent the traditional downside to browser-based mining — that mining only occurs while the page hosting the mining code is open in the browser — are likely to increase the perceived opportunity for criminals to monetize their activities.

Figure 2. CoinHive code inserted into CBS's Showtime website. (Source: The Register)
Threat actors exploit any opportunity to generate revenue, and their activity can affect unknowing facilitators as well as the end victim. For example, in December 2017, a customer at a Starbucks in Brazil noticed that the store's public Wi-Fi imposed a ten-second delay when web browsers connected to the network so that CoinHive code could mine a few seconds of Monero from connecting hosts. Starbucks responded swiftly and confirmed the malicious activity exploited the store's third-party Internet service.
Impact
Although cryptocurrency mining is legal, using a corporate system may violate an organization's acceptable use policies and result in law enforcement action. The impact to an individual host is the consumption of processing power; IR clients have noted surges in computing resources and effects on business-critical servers. This impact is amplified in large-scale infections.
To demonstrate the impact that mining software can have on an individual host, Figure 3 shows Advanced Endpoint Threat Detection (AETD) - Red Cloak™ detecting the XMRig cryptocurrency miner running as a service on an infected host. XMRig is advertised as a freely available high-performance Monero CPU miner with official full Windows support.
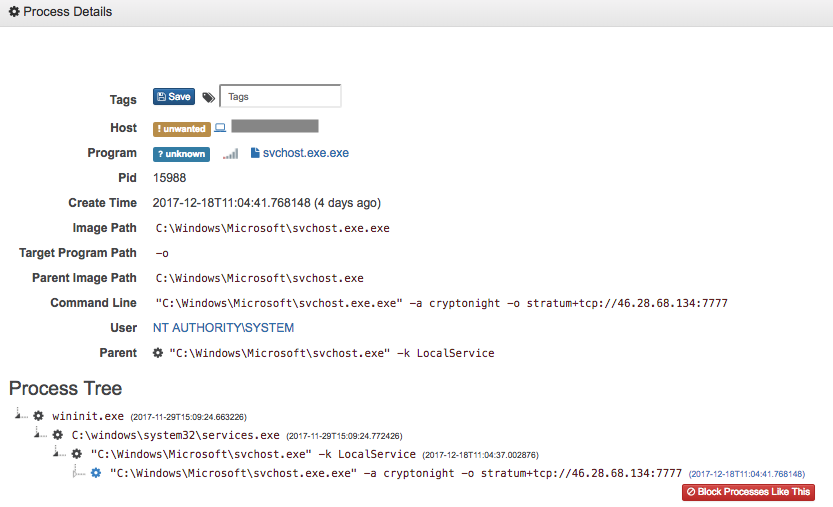
Figure 3. XMRig cryptocurrency miner running as local service on an infected host. (Source: Secureworks)
XMRig accepts several variables as inputs (see Figure 4), including the wallet, a username and password if required, and the number of threads to open on the system.
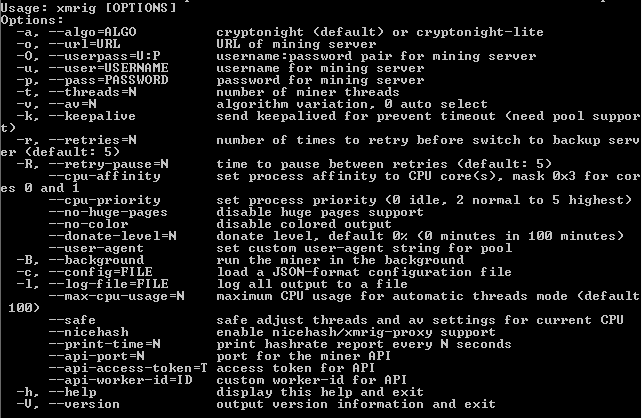
Figure 4. XMRig command-line options. (Source: Secureworks)
Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. Over time, this performance load forces the host to work harder, which also generates higher energy costs.
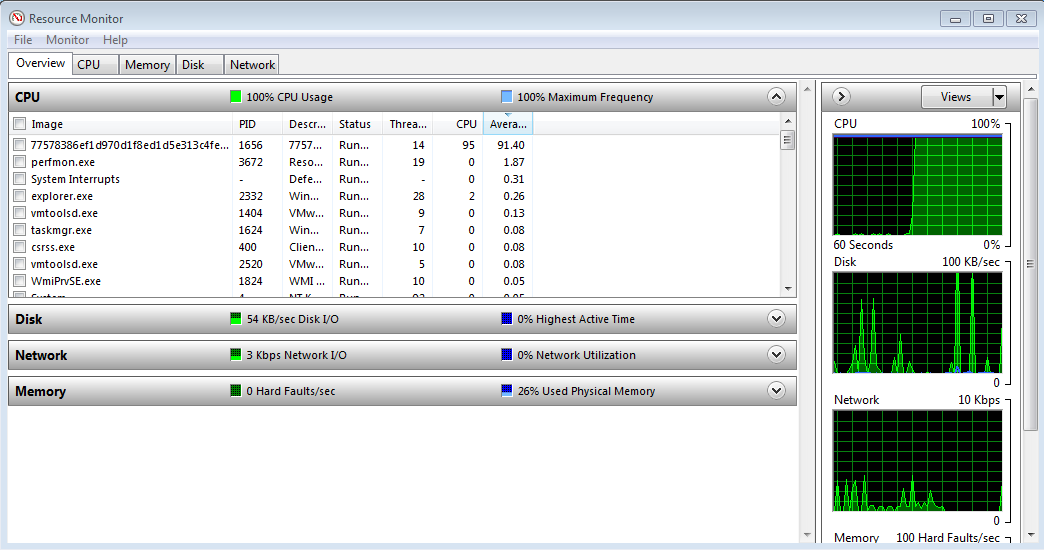 Figure 5. CPU utilization spike after executing XMRig miner software. (Source: Secureworks)
Figure 5. CPU utilization spike after executing XMRig miner software. (Source: Secureworks)
Cryptocurrency mining versus ransomware
After gaining the ability to run software on a compromised system, a threat actor chooses how to monetize the system. In 2017, CTU researchers reported that many financially motivated threat actors had shifted to using ransomware rather than traditional banking trojans, which have higher costs in terms of malware development and maintaining money muling networks. Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Individual payments from successful ransomware extortion can be lucrative, in some cases exceeding $1 million. However, there is a significant chance that victims will not pay the ransom, and that ransomware campaigns will receive law enforcement attention because the victim impact is immediate and highly visible.
In contrast, a victim may not notice cryptocurrency mining as quickly because it does not require capitulation, its impact is less immediate or visible, and miners do not render data and systems unavailable. These factors may make mining more profitable than deploying ransomware. If the threat actor manages resource demands so that systems do not crash or become unusable, they can deploy miners alongside other threats such as banking trojans to create additional revenue. Threat actors could also decide to deploy ransomware after mining cryptocurrency on a compromised network for a final and higher value payment before shifting focus to a new target.
Prevalence
Secureworks iSensor telemetry between 2013 and 2017 related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Intrusion detection system events are not a reliable indicator over time due to the addition of clients and better detections as network countermeasures evolve. Even accounting for these factors, the data shows that the trajectory of criminals' unauthorized Bitcoin mining activity broadly matches the increasing value of Bitcoin (see Figure 6). There was a noticeable acceleration around October 2016.

Figure 6. Bitcoin price compared to iSensor detections for Bitcoin network traffic on Secureworks client networks between December 2013 and February 2018. (Sources: Secureworks and bitcoincharts.com)
Client telemetry shows a similar increase in CoinHive traffic since its launch in September 2017. While CoinHive activity is typically a legitimate, if sometimes controversial, form of revenue generation, organizations need to consider how to manage the impact to corporate systems.
Tactics, techniques, and procedures
Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious artifacts. Most identified cryptocurrency miners generate Monero, probably because threat actors believe it provides the best return on investment. Unlike Bitcoin, Monero makes mining more equitable for computers with less computational power, which is suitable for exploiting a large number of standard corporate computing assets.
The techniques that Secureworks IR analysts have observed threat actors using to install and spread miners in affected environments align with common methods that CTU researchers have encountered in other types of intrusion activity. Threat actors will use the most effective techniques to create a large network of infected hosts that mine cryptocurrency.
Weaponization
Legitimate cryptocurrency miners are widely available. Underground forums offer obfuscation, malware builders, and botnet access to hide illegitimate mining (see Figure 7).

Figure 7. Forum advertisement for builder applications to create cryptocurrency mining malware. (Source: Secureworks)
Delivery, exploitation, and installation
Initial access and installation often leverage an existing malware infection that resulted from traditional techniques such as phishing. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads. Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol (FTP) servers or Terminal Services (also known as Remote Desktop Protocol (RDP)) via brute-force attacks or by guessing the default password to gain access. Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload.
Persistence
Because each instance of cryptocurrency mining malware slowly generates revenue, persistence is critical to accumulate significant returns. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation (WMI) event consumers, scheduled tasks, autostart Windows services, and registry modifications. For example, threat actors have set cron jobs on Linux systems to periodically download mining software onto the compromised host if it is not already present (see Figure 8). A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection.

Figure 8. Script setting cron job to periodically download and run mining software if not already present on Linux host. (Source: Secureworks)
Propagation
Miner malware payloads are often propagated using lateral movement. Threat actors have used malware that copies itself to mapped drives using inherited permissions, created remote scheduled tasks, used the SMBv1 EternalBlue exploit, and employed the Mimikatz credential-theft tool. In one incident, threat actors added iframe content to an FTP directory that could be rendered in a web browser so that browsing the directory downloaded the malware onto the system. This technique has also been observed on Internet-facing websites. Miner malware has also attempted to propagate over the Internet by brute force or by using default passwords for Internet-facing services such as FTP, RDP, and Server Message Block (SMB).
Mitigation
Figure 9 lists the top recommendations that Secureworks IR analysts provided after detecting cryptocurrency mining malware in clients' networks in 2017.

Figure 9. Recommendations provided during Secureworks IR engagements involving cryptocurrency malware. (Source: Secureworks)
These recommendations address techniques used by cryptocurrency miners and threat actors in compromised environments. Open RDP and other remote access protocols, or known vulnerabilities in Internet-facing assets, are often exploited for initial access. After compromising an environment, a threat actor could use PowerShell or remote scheduled tasks to install mining malware on other hosts, which is easier if the process attempting to access other hosts has elevated privileges. The most effective means of identifying mining malware on infected hosts is through endpoint threat detection agents or antivirus software, and properly positioned intrusion detection systems can also detect cryptocurrency mining protocols and network connections. Comprehensive and centralized logging is critical for a response team to understand the scale and timeline of an incident when mining malware has infected multiple hosts.
Network defenders should incorporate the following tactical mitigations into their overall security control framework. These mitigations are effective against a broad range of threats:
- Disable unnecessary services, including internal network protocols such as SMBv1 if possible. Remove applications that have no legitimate business function, and consider restricting access to integral system components such as PowerShell that cannot be removed but are unnecessary for most users.
- Implement two-factor authentication (2FA) on necessary externally accessible services. Consider using custom solutions for functions such as remote workstation administration rather than standard ports and protocols.
- Review and apply appropriate security updates for operating systems and applications in a timely manner.
- Apply the principle of least privilege for system and application credentials, limiting administrator-level access to authorized users and contexts. For Windows systems, consider a solution such as Microsoft's Local Administrator Password Solution (LAPS) to simplify and strengthen password management.
- If possible, implement endpoint and network security technologies and centralized logging to detect, restrict, and capture malicious activity. Managing outbound network connections through monitored egress points can help to identify outbound cryptocurrency mining traffic, particularly unencrypted traffic using non-standard ports.
Conclusion
Cryptocurrency mining is an attractive proposition for threat actors seeking to monetize unauthorized access to computing resources. It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. There has been a significant increase in cryptocurrency mining activity across the Secureworks client base since July 2017.
Although cryptocurrency malware may not seem as serious as threats such as ransomware, it can have a significant impact on business-critical assets. Organizations should ensure that appropriate technical controls are in place. The mitigations for installation, persistence, and lateral movement techniques associated with cryptocurrency malware are also effective against commodity and targeted threats.
References
Abbasi, Dr. Fahim, et al. "Resurrection of the Evil Miner." FireEye. June 20, 2016. https://www.fireeye.com/blog/threat-research/2016/06/resurrection-of-the-evil-miner.html
Bort, Julie. "May 22 Is Bitcoin Pizza Day Thanks To These Two Pizzas Worth $5 Million Today." Business Insider. May 21, 2014. http://www.businessinsider.com/may-22-bitcoin-pizza-day-2014-5?IR=T
Cimpanu, Catalin. "Android Malware Will Destroy Your Phone. No Ifs and Buts About It." BleepingComputer. December 18, 2017. https://www.bleepingcomputer.com/news/security/android-malware-will-destroy-your-phone-no-ifs-and-buts-about-it/
Goodin, Dan. "Web host agrees to pay $1m after it's hit by Linux-targeting ransomware." Ars Technica. June 19, 2017. https://arstechnica.com/information-technology/2017/06/web-host-agrees-to-pay-1m-after-its-hit-by-linux-targeting-ransomware/
Gu, Jason; Zhang, Veo; and Shen, Seven. "Coin Miner Mobile Malware Returns, Hits Google Play." Trend Micro. October 30, 2017. http://blog.trendmicro.com/trendlabs-security-intelligence/coin-miner-mobile-malware-returns-hits-google-play/
Haas, Brad. "Cryptocurrency Miners Exploiting WordPress Sites." Wordfence. October 26, 2017. https://www.wordfence.com/blog/2017/10/cryptocurrency-mining-wordpress/
Higgins, Stan. "$600 Billion: Cryptocurrency Market Cap Sets New Record." CoinDesk. December 18, 2017. https://www.coindesk.com/600-billion-cryptocurrency-market-cap-sets-new-record/
Higgins, Stan. "Google Pulls Five Mobile Wallpaper Apps Due to Bitcoin Mining Malware." CoinDesk. April 24, 2014. https://www.coindesk.com/google-pulls-six-mobile-wallpaper-apps-bitcoin-mining-malware
Kafeine. "Adylkuzz Cryptocurrency Mining Malware Spreading for Weeks via EternalBlue/DoublePulsar." Proofpoint. May 15, 2017. https://www.proofpoint.com/us/threat-insight/post/adylkuzz-cryptocurrency-mining-malware-spreading-for-weeks-via-eternalblue-doublepulsar
Kelion, Leo. "Starbucks cafe's wi-fi made computers mine crypto-currency." BBC. December 13, 2017. http://www.bbc.co.uk/news/technology-42338754
McCarthy, Kieren. "CBS's Showtime Caught Mining Crypto-coins in Viewers' Web Browsers." The Register. September 25, 2017. https://www.theregister.co.uk/2017/09/25/showtime_hit_with_coinmining_script/
My Online Security. "Fake fidelity Investments Secure Documents malspam delivers Trickbot banking trojan." December 20, 2017. https://myonlinesecurity.co.uk/fake-fidelity-investments-secure-documents-malspam-delivers-trickbot-banking-trojan/
Nakamoto, Satoshi. "Bitcoin: A Peer-to-Peer Electronic Cash System." Bitcoin.org. October 31, 2008. https://bitcoin.org/bitcoin.pdf
Secureworks. "2017 State of Cybercrime Report." September 18, 2017. https://www.secureworks.com/resources/rp-2017-state-of-cybercrime
Secureworks. "BGP Hijacking for Cryptocurrency Profit." August 7, 2014. https://www.secureworks.com/research/bgp-hijacking-for-cryptocurrency-profit
Segura, Jerome. "Persistent drive-by cryptomining coming to a browser near you." Malwarebytes. November 29, 2017. https://blog.malwarebytes.com/cybercrime/2017/11/persistent-drive-by-cryptomining-coming-to-a-browser-near-you/
Sulleyman, Aatif. "Hackers Infect Facebook Messenger Users with Malware that Secretly Mines Bitcoin Alternative Monero." The Independent. December 22, 2017. http://www.independent.co.uk/life-style/gadgets-and-tech/news/digmine-facebook-messenger-cryptocurrency-mining-malware-monero-bitcoin-a8125021.html
wh1sks. "The ShadowBrokers may have received up to 1500 Monero (~$66,000) from their June 'Monthly Dump Service.'" Steemit. June 28, 2017. https://steemit.com/shadowbrokers/@wh1sks/theshadowbrokers-may-have-received-up-to-1500-monero-usd66-000-from-their-june-monthly-dump-service
Zavodchik, Maxim and Segal, Liron. "Zealot: New Apache Struts Campaign Uses EternalBlue and EternalSynergy to Mine Monero on Internal Networks." F5 Labs. December 15, 2017. https://f5.com/labs/articles/threat-intelligence/cyber-security/zealot-new-apache-struts-campaign-uses-eternalblue-and-eternalsynergy-to-mine-monero-on-internal-networks
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
