- Date: January 26, 2006
- Author: Joe Stewart
Analysis
As reported in the previous analysis, BlackWorm contacts a web stats counter to report infections. Working with the ISP hosting the counter along with the TISF BlackWorm task force, we have obtained and analyzed the logs from the counter.
Update: February 6, 2006
The folks at CAIDA have done a terrific job of applying statistical theory to the raw log hits - if you're looking for in-depth statistical analysis, you should check out their writeup.
An attempt was made by an unknown party to artificially inflate the counter using a set of 279 distributed (presumably compromised) computers. However, it is easy to differentiate these requests from the actual infected systems. As of the time these statistics were taken, the counter is well above 5 million, however, the actual count of infected users is closer to 300,000 worldwide and not increasing at too great a rate.
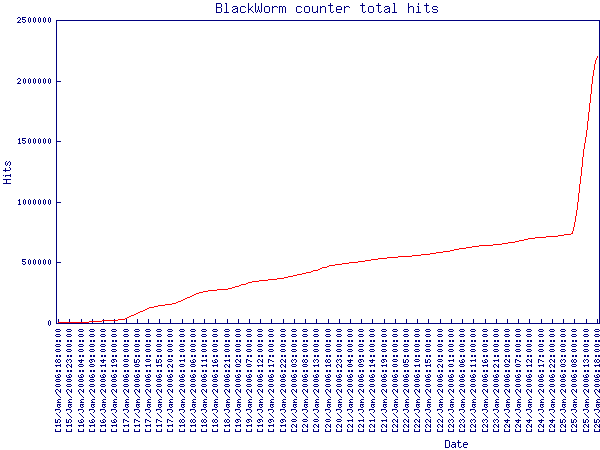
The graph above shows the total hits from all sources on the counter. Notice the sharp increase on Jan 25 at 8:00AM, as the coordinated attack on the counter begins.
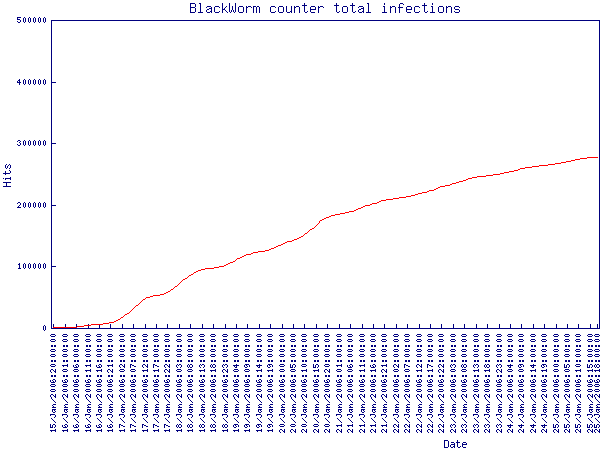
The graph above shows the total infections, after removing the attacking IPs and other hits which do not conform to the signature of the worm's requests. Duplicate IP addresses with the same user-agent have been removed as well, giving us as near to an actual infection count as possible, given the use of proxy/cache servers.
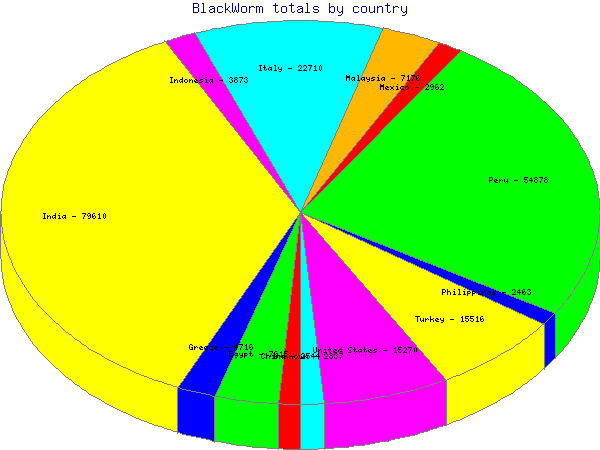
The pie chart above shows the total infections by country for all countries with greater than 2000 infected IP addresses. The high infection rates in India, Peru and Italy are interesting to note. It is possible some of these figures are skewed by ARIN IP address reassignment, but we do believe India is the hardest-hit country by far in terms of overall infection rate.
Even so, 300,000 infected users worldwide is not a terribly large amount when compared to previous worms like Sober or Mydoom. However, with this worm it isn't the quantity of infected users, it is the destructive payload which is most concerning.
Frequently Asked Questions
Q: What did you use to match IP addresses to countries?
A: The IP::Country and Geography::Countries Perl modules.
Q: Isn't it impossible to get an exact count, due to proxy/cache servers and NAT?
A: Yes, this is a well-known problem with taking web statistics. We've tried to eliminate this skew as much as possible by checking the user-agent string as well as the IP, but even that is not perfect. One thing to consider is that users on dialup lines will skew the count in the other direction, showing up as multiple IPs for one infection, so you're never going to have a 100% accurate count.
Q: Can you share the complete counts for all infected countries?
A: Sure:
|
|
Q: Those stats look a little off. How can Turkey, with a much smaller Internet-connected population have more infections than the United States?
A: Indeed - it does appear strange - however, viruses don't always spread uniformly. There are many factors at play which are hard to quantify, such as the initial seeding, social-engineering, AV deployment, and random chance. And, as with all statistics, take with a grain of salt.
Q: Peru? Are you sure?
A: Yes, we have resolved the hostnames and they belong primarily to a single Peruvian ISP. We can only speculate that someone with a large list of customers at that ISP became infected and most of the users received the attachment.
Q: How can I keep current on this threat until February 3?
A: Sites with frequent updates on BlackWorm are http://isc.sans.org/blackworm/and http://blogs.securiteam.org/
Update - January 31, 2006
We decided to take a different approach to de-duplicating the IP addresses in the logs. Instead of only counting unique IP/User-Agent pairs, this time we make an educated guess as to what constitues a single user rebooting multiple times, and what constitutes a company or organization utilizing one or several NAT devices. In this case we unscientifically picked a number, ten. IP addresses with fewer than this number of hits are considered to fall into the individual user/multiple reboots category. IP addresses with more than this number of hits are considered one infection per hit. Still plenty of room for error, but we get some interesting results:
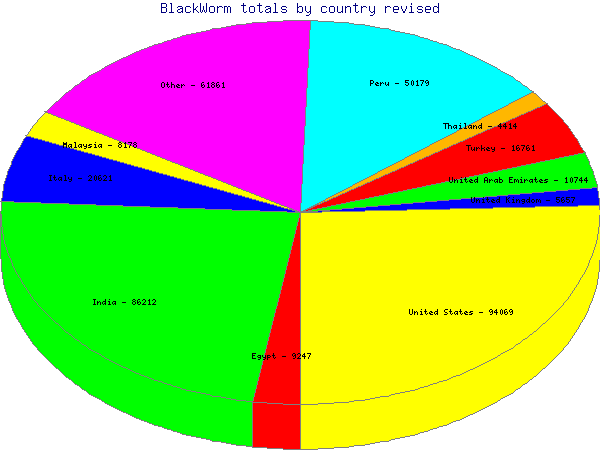
In the chart above, we have an additional day's worth of logs, and we have combined all countries with fewer than around 4000 hits together in the "Other" grouping.
We can see that the United States now tops India in the total number of infections, as one might expect. Surprisingly though, the bulk (75,435) of these hits are from two NAT devices at a single US company. Based on the more recent logs plus the different methodology, we believe the total number of users infected worldwide is actually closer to 600,000.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
