- Date: July 28, 2010
- Author: Joe Stewart, Director of Malware Research for SecureWorks
Summary
Three-month-long investigation by CTU uncovers inner workings of Russian check counterfeiting operation. SecureWorks has notified and is working with law enforcement on this scam. SecureWorks has protections in place for both the Zeus and the Gozi Trojans which are utilized in this scam.
Major findings
- Highly-automated system abusing multiple external services; eg: check archiving services, check verification services, online job sites and web mail services.
- Estimates of $9M worth of counterfeit checks printed in the last year
- Estimated 65,000 worth of credit-card fraud against an overnight package delivery service
- Large Scale Money Mule Recruitment Effort-- Names and addresses of 2,884 job seekers respond to hackers’ money mule emails
- Anti-fraud systems abused to help facilitate the fraud
- Novel use of VPN tunnels in botnet operation
Introduction
In April 2010, during the course of an unrelated investigation, SecureWorks' Counter Threat Unit (CTU) discovered a unique variant of the well-known ZeuS trojan. Note: SecureWorks was one of the first security groups, along with researcher Michael Leigh, to investigate and report on the Zeus Banking Trojan in November 2007.
Analysis of the sample revealed that in addition to the ordinary ZeuS functionality of stealing credentials, two new functions had been added:
- The infected system listens on a random TCP port in order to serve as a SOCKS proxy
- The infected system establishes a VPN (Virtual Private Network) connection to a remote server using the PPTP (Point-to-Point Tunneling Protocol) functionality built-in to Windows.
Although it is very common for trojans (especially ones designed to aid in financial fraud) to employ proxy server capability, this is the first time that the CTU has seen the use of VPN technology in such software. Criminals have long devised systems to encrypt the communications of their botnet trojans and have also incorporated schemes to allow traffic from the criminal's network to be tunneled through firewalls into protected systems. However, by employing the very simple VPN functionality built right in to Windows, the criminal bypasses the need to develop complex systems, and can simply route his/her malicious traffic over the VPN. If done correctly, this gives the criminal three primary benefits:
- The VPN traffic can be encrypted, defeating signature-based network IPS/IDS devices that might detect the malicious transfer of data
- A VPN can give the criminal the ability to connect-back into the protected computer, and even use the infected system as a route to other systems on the protected network
- The criminal could route all traffic from the bots to the botnet controller over the VPN, and deny connections to the VPN controller from all sources but the VPN exit IP address. In doing so, the criminal could make it appear to the world that the botnet controller is offline, while still serving commands to and stealing data from the infected systems under its control
All these advantages can be had for just a few extra lines of code, with perhaps only a telltale new connection under the network control panel (which of course could be hidden from view with the help of a rootkit). These considerations made this discovery seem fairly important, until further analysis revealed a few facts specific to this operation's use of the VPN capability:
- The VPN connection established by the related ZeuS samples was NOT encrypted, only encapsulated
- The ZeuS phone-home traffic was not even routed over the VPN
It became clear that the primary reason for the VPN tunnel was to allow the controller to proxy traffic back to the bots, bypassing any firewalls or NAT (network address translations) that would ordinarily block arbitrary incoming connections from the Internet. By joining the botnet as just another "infected" PC, CTU was able to uncover a great deal of information about the overall purpose of the botnet. Over the course of three months, using botnet monitoring, server reconnaissance and open- source intelligence gathering, the CTU found that the entire operation was dedicated to one purpose: stealing money from U.S. banks, businesses and individuals by counterfeiting checks.
The BigBoss Operation
Malware
After discovering the first ZeuS sample utilizing proxy/PPTP tunneling code, the CTU was able to locate many additional samples with the same characteristics, the oldest of which dated back to March 2008. The primary differentiators that can be seen in these samples are:
- The default ZeuS 1.0 executable name is changed from "wsnpoem.exe" to "wsnpoema.exe"
- The default ZeuS 1.0 file storage path is changed from "%system%\wsnpoem" to "%system%\wsnpoema"
- When executed, the file C:\Documents and Settings\All Users\Application Data\Microsoft\Network\Connections\Pbk\rasphone.pbk is altered, and a new network connection named "test" is inserted.
- TCP port 1723 traffic to 213.155.1.3 or fin-team.org
bigbossfinance.net/bigboss/config.bin
91.211.64.121/leprozorium/config.bin
calvinkleinstuffz.com/calvinklein/config.bin
Based on the ZeuS configuration file path above, CTU refers to this crime organization as "the BigBoss group" as a way to distinguish their activity for future reference (although this is almost certainly not the name they use themselves, if they even have a name for their group).
Later, the CTU found that the ZeuS 1.0 code was apparently abandoned by the group (probably due to the group being unable to obtain the source code to newer ZeuS releases) and the VPN/proxy code was split off into a standalone binary, called "booyaka.exe". This binary used the hostname eca-payments.com to find the IP of the VPN/proxy control server. This is the point from which all of the infected PCs making up the botnet can be accessed simply by connecting from the server's internal VPN interface to the VPN-assigned IP address of the bot, and this host became the next focus of the investigation.
Proxy/VPN Botnet
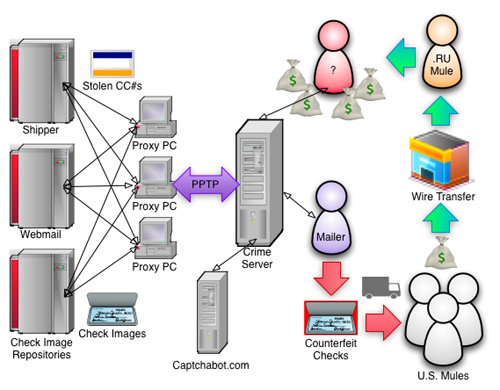
The proxy botnet is used for quite a few different aspects of the operation. It is the component that allows the group to act with anonymity when abusing external services. Having a botnet with thousands of infected PCs also allows the group to avoid being easily blocked when accessing remote websites. Below is some of the activity CTU observed traversing the proxy botnet at different times.
- Money mule job offer spam through multiple webmail services
- Scraping of job websites to obtain new email addresses to spam. Essentially, the hackers are logging into online job sites and pulling email addresses of those looking for jobs
- Automated webmail account creation to use in sending spam (using a CAPTCHA-breaking service)
- Abuse of URL-shortening services to obfuscate links in the spam
- Scraping of repositories for scanned processed checks
- Purchase of an overnight package delivery service’s self-print postage labels (using stolen credit cards) to send checks to money mules
Almost all aspects of the operation shown above are automated, and each plays a part in the ultimate objective of the group, which is moving money out of U.S. bank accounts and into Russia.
Money Mule Job Offers
The group is constantly recruiting new money mules to be unwitting pawns (or sometimes victims) in the operation. By accessing a variety of job sites (probably using stolen credentials); the group is able to automate the activity of pulling email addresses of job seekers into the spamming system. The offers are varied from run to run, but they are typically vague offers for the respondent to work for an international company performing financial transactions of some nature. An example email sent by the group is shown below:
Actual Hacker/Counterfeiter Email Sent to Money Mule
To: [job seeker's name]
From: Human Resource Department
Subject: Vacancy for [job seeker's name]
Dear [job seeker's name]
Our organization – “Global Business Payments Inc.” is processing with bastard banking services throughout the world for more than 10 years.
Now it is widen its presence and a pack of services in the United States. One of our new accommodations is transferring of money with the US check for non U.S. citizens. Therefore we need new executives for the position of "Check Processing Manager".
Responsibilities include:
Getting a check from an overnight delivery service
Check cashing
Money transferring to the client the mean they choose Accounting in the peculiar form for each check
Requirements, Demands, Claims:
Active US address
1-2 hours of free time per day
Positive credit history
Benefits:
High payment. From 100 $ up to 500 $ per day Guaranteed payment of min. 3 000 $ Few working hours Our organization takes care of all the taxes on executives’ done transactions.
In order to take this motion, please, register at our webpage and make the instructions.
Best wishes.
TOP MANAGER
Global Busines Payments Inc.
Over time, the group has had to shift the identity of the hiring company so as to seem legitimate in case the job seeker decides to check out the company's reputation online. The BigBoss group has used a number of fake company names over time, some of which may be similar to other legitimate firms (a way to cause brand confusion and make it appear as though the fake company actually exists). Some of the company names used by this group in the past are:
* Succes Payment Ltd
* Global Busines Payments Inc
* InterWeb Exchange
* Proteus Solutions
In most cases, the company claims to be a Finnish financial services firm seeking account executives. If the job seeker responds with his/her information, he/she will be sent a counterfeit check overnight and instructions via email on how to process the check. A typical set of instructions the money mule receives are shown below:
Actual Hacker/Counterfeiter Email Sent to Money Mule:
Subject: First Task for [money mule's name] from Global Business. Please follow the instruction attentively
From: Success Payment <[email protected]>
To: [redacted]
Dear [money mule's name]
Attention: Please reply to this letter not later then in 12 hours after receiving.
Our customer have sent you a check in amount - $2740 You will receive the check by overnight delivery from 07/10 until 07/12.
The overnight package delivery service tracking number is (xxx)
You can check your mail status on the overnight delivery website: Track and Confirm.
You can cash check at:
1) Bank that issued the check.
2) One of the check cashing places.
3) Deposit the check onto your bank account in any bank and wait until the check clears.
IN CASE YOU SEND MONEY SAME OR NEXT DAY FROM THE MOMENT YOU GET THE CHECK YOUR COMMISSION WILL BE HIGHER. YOUR SHARE WILL BE 15% (PERCENT) OF THE CHECK AMOUNT.
IF CHECK CASHING TIME EXCEEDS THIS TIME PERIOD YOU WILL GET STANDARD 8%
(PERCENT) COMMISSION OF THE CHECK AMOUNT.
Same or next day:
Amount to be send is 2204
Your money is 411
Wiring fees is 125
After two days:
Amount to be send is 2395
Your money is 220
Wiring fees is 125
If there are additional fee for check's cashing please deduct it from sending amount.
You will need only the following information to wire the payment ---
1) First Name ** [Russian mule's first name]
2) Last Name ** [Russian mule's last name]
3) City ** Saint-Petersburg
4) Country ** Russia
After you have transferred money you will be given the Money Transfer Control Number.....
(MTCN) number.
After you make the Transfer please email us the same day the following
data:
PLEASE, SPECIFY THE FOLLOWING DATA COMPLETELY
1) Your address (as you filled in the wire receipt):
2) Your full name (as you filled in the wire receipt):
3) Amount of the transfer:...............
4) MTCN
Please send scan copy or fax documents from the wire service (if possible).
After we our client receive transfer and are certain of your efficiency, the number of checks for cashing will be increased and you may be getting them on a daily basis. We appreciate the quality of our partnership and hope for mutual cooperation for a long time. Please you are kindly requested to email us back in regard of this message that you have read it and understood.
Thank you
There are some important factors in these instructions designed to create the greatest possibility of success for the counterfeiter. First, they need to get the money wired out of the account as fast as possible, so that when the bank comes back to the money mule for the stolen funds the money will already be in Russia. The check amount is always for a figure just under $3,000 USD - this is to avoid additional hold times that are usually placed on check deposits greater than that amount. The longer the check is held, the more likely the fraud will be caught and the funds will not be released. In order to incentivize the money mule to act quickly, they are offered 15% commission if they wire the money by the next day. If they wait longer than that, their commission drops to 8%.
If a mule does not respond via email with the wire information within a couple of days, the group does not give up - they will call the mule on the phone and ask about the money. With one of the money mules, a representative of the group (a female speaking English with a noticeable Russian accent) called and left several voice messages, urging the mule update them on the status of the check.

Photo: Counterfeit check
CTU spoke with some of the money mules to get insight into what transpired in other cases, and was able to obtain an image of one of the checks sent to a mule. The check is quite authentic-looking at first glance, and is even printed on paper with anti-counterfeiting features, and we assume, with magnetic ink. However, it has become apparent that the English language is not one of the group's stronger skills Aside from the poor grammar in the money mule emails and the misspelling of "Success" and "Business" in their fake company names, the counterfeiter misspelled the company name of the account holder, as well as the word "order" in "pay to the order of".
Point-and-Click Check Counterfeiting
Photo: A sea of stolen checks
A look at more of the activity emanating from the proxy botnet gave clues as to how the BigBoss operation is able to counterfeit checks. An automated process was designed to scrape images of processed checks from multiple services that archive checks on behalf of businesses. Ironically, one of these services the group pulled check images from is an anti-fraud network for merchants who have a check cashing service. The other service electronically archives all checks received by a business. The BigBoss group is continuously pulling images of checks from these systems, which gives them the ability to print forgeries, having the ABA routing number, account number, company name and address, and an image of the authorized signature at hand for thousands of businesses.
The group uses off-the-shelf commercial check printing software, the kind of program a real business might also use to manage the company checking account. At one point, the BigBoss group left a copy of the check software's database in a public location, where CTU was able to obtain and analyze it.
Inside the database are the names and addresses of 2,884 job seekers who responded to the money mule emails, along with account information and check templates for five companies. For a two-week period, counterfeit checks written on these accounts were set to be printed and dispatched to 14 money mules, for a total amount of $40,880 USD. Even after wire transfer fees and the money mule's 8-15% commission, this is still a pretty nice bi-weekly income for the group - assuming their conversion rate is close to 100%. However, in our discussions with the some of the mules, we found most of them did not complete the transaction and wire the money - either they got suspicious, or the bank alerted them to the fraud when they tried to deposit the check, or the bank put a hold on the check and refused to release the money when the check was discovered to be fraudulent. Therefore it is impossible for us to know the group's actual income from the check counterfeiting operation.
The database does give us a little bit of insight into how prolific the operation has been, showing 3,285 transactions (i.e. checks printed) on 1,280 accounts since Jun 24, 2009 when the current database was created.
Using a figure of $2,800 USD as a ballpark average, we estimate that the group has probably printed out and mailed over $9 million USD face value worth of counterfeit checks. Those 3,285 checks mailed next-day-delivery also probably represent over $65,000 USD in fraud against the overnight shipper.

Spear-Phishing Malware Operation
Occasionally the group will send spear-phishing emails to entice recipients to download credential-stealing malware. It is likely this part of the operation is used to gather credentials to services that might benefit the group, especially services that archive check images.
The email addresses appear to be from databases that have been gathered from third-party sites, probably using SQL injection. The recipients are largely involved with processing financial transactions for companies, and the email body uses the ploy of offering an update or plug-n for a financial software package. The download URL provided for the alleged update/plugin is actually a malware installer. CTU has observed both the ZeuS and Gozi credential-stealing trojans being delivered as the end payload of these spear-phishing runs. Note: SecureWorks’ Director of Threat Intelligence Don Jackson was the first to discover Gozi, a credential -stealing Trojan, which made news in 2007 with its owners’ innovative way of “selling time access ” to the stolen data it captured.
How to Defend Against Check Counterfeiting
Clearly, check counterfeiting has been brought into the 21st century by the BigBoss group and probably others. While it would be nice to be able to do away with the archaic system of easily-counterfeited paper checks, companies have few other alternatives to make payments that can be widely accepted by all the vendors and contractors they do business with. One thing a business can do to ensure that counterfeit checks will not present risk to their account is to get a service from the bank called "Positive Pay". This system allows the account holder to verify each check transaction presented matches a known payment before the bank processes it. If the account holder is diligent in reviewing the daily transactions, this system should help prevent them from losing money due to counterfeit checks.
In addition, anyone at the company accessing online banking or other financial portals should do so from protected computer systems that have been hardened, have very limited Internet access, and are isolated from the rest of the corporate network. These days the threat to a company's bank account from hackers is very real, and these criminals have developed sophisticated malware that can intercept and alter transactions in progress, even when two-factor authentication is in play.
Antivirus engines are unlikely to catch these malicious programs until it is too late, so having a dedicated workstation that doesn't have access to anything but the bank/financial portal is a good way to keep the hackers out of the company's accounts.
The counterfeit operation also relies on abuse and hacking of third- party systems. Weak authentication and/or SQL-injection flaws in sites that warehouse check information and images are a major benefit to the criminals. These systems need to employ third-party code auditors to find the weaknesses in the systems before the hackers do, and incorporate strong authentication systems that are immune to the latest trojan attacks, such as out-of-band or offline cryptographic transaction verification.
Financial services and even the webmail portals that the criminals use as a spam conduit can employ better bot-detection systems that can make it difficult to automate abuse on a large scale. And finally, it would be extremely beneficial if those signing up for a job site are required to read and understand about the different kinds of fraudulent job offers they might receive, what kinds of red flags they might see in a fraudulent offer, along with guidelines for checking out a prospective hirer's legitimacy. If all of these parties were able to block these kinds of abuses, the criminals would find it much more difficult to carry out an operation of this scale.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
