Overview
Since publishing information about top banking botnets and takedown efforts in 2014, Dell SecureWorks Counter Threat Unit™ (CTU) security intelligence researchers have observed cybercriminals learning from past experience and quickly adapting when banks and other financial institutions improve their security measures. Takedown efforts continued in 2015, with global law enforcement partnering with organizations in the private sector to launch operations targeting two of the most active banking botnets: Ramnit and Bugat v5 (Dridex). Europol collaborated with multiple law enforcement and industry partners in early 2015 to seize servers and other important infrastructure owned by the group operating the Ramnit botnet. In the fall of 2015, the CTU™ research team collaborated with the UK National Crime Agency (NCA), the U.S. Federal Bureau of Investigation (FBI), and the Shadowserver Foundation to take over the Bugat v5 banking botnet.
Threats are becoming more sophisticated, incorporating emerging technologies, advanced cryptography, and resilient infrastructure to resist surveillance and disruption. Modifications to banking trojans support stealing bank credentials and website cookies to impersonate victims, searching hard disks for specific files, granting threat actors remote access to a computer, and allowing threat actors to exfiltrate stolen information or download additional malware. Cybercriminals are also expanding beyond traditional banking botnets to evolve new attack vectors. CTU researchers observed an increase in persistent attacks targeting specific organizations to compromise financial accounts, illustrating use of a delivery method that was previously used only in advanced persistent threat (APT) attacks. With banks continuously moving to the mobile platform for payment and banking applications, cybercriminals' interest in targeting mobile banking services has increased. Attacks on mobile banking platforms, as well as advancements in bypassing advanced authentication mechanisms like two-factor authentication (2FA) and transaction authentication numbers (TANs), evolved in 2015.
Key findings
CTU analysis of banking botnet activity in 2015 revealed key findings:
- New targets included cloud service providers, app stores, online tech stores, and organizations in the shipping, warehousing, e-commerce, and marketing industries.
- Attackers used banking trojans to target more than 1,500 financial institutions across more than 100 countries. Over 80 percent of the institutions were located in the United States, but institutions in the United Kingdom, Europe, and Australia were also popular targets.
- Small and mid-sized businesses have become popular targets for online banking fraud through credential theft and subsequent fraud via Automated Clearing House (ACH) transactions or wire transfers.
- Malware families expanded to new regions: the ISFB variant of Gozi targeted organizations in Eastern Europe, particularly Bulgaria; Shifu (a variant of Shiz) introduced campaigns targeting Japan; and Tinba added targets in Romania and Singapore.
- The number of attacks in Asia and the Middle East continued to increase.
- The Shifu, Reactorbot, and Corebot botnets became active, and there was increased activity from Gozi ISFB. However, Dyre mysteriously disappeared from the threat landscape.
- The Ramnit botnet reemerged in the fall of 2015 after some of its infrastructure was seized by law enforcement earlier in the year, and Bugat v5 (Dridex) immediately reemerged after a takeover operation in the fall of 2015. This resiliency challenges efforts by law enforcement and the security industry to permanently disable the botnets.
- The introduction of new variant of Neverquest in the fall of 2015 and the constant evolution of ISFB, both variants of Gozi (originally discovered by Dell SecureWorks CTU) reflect the determination of attackers targeting the financial vertical.
- Botnets continue to rely on hidden network services such as Tor and Invisible Internet Project (I2P), as well as domain generation algorithms (DGAs), to resist surveillance and takedowns.
- By using private spam mailers, botnet groups continue to deviate from the “spam as a service” model.
Banking botnet activity
While most banking botnets that were active in 2014 continued their operations in 2015, Shifu, Corebot, and Reactorbot emerged as new additions. Increased activity from Qadars, Tinba, Gozi ISFB, and Gozi Neverquest reflected a consistent market for banking fraud, and the reemergence of Ramnit and Bugat v5 after takedowns showed the cybercriminals' resilience. A search for other revenue streams led to a steady shift in 2015 from botnet-driven infections to ransomware. Ransomware provides threat actors with a straightforward and direct revenue stream and does not require infrastructure maintenance.
The botnet-as-a-service model has grown increasingly popular. Threat actors rent subsets of their botnets for malicious activities such as distributed denial of service (DDoS) attacks, click fraud, cryptocurrency mining, and targeted attacks. Mobile botnets are also used for DDoS attacks, click fraud, and impersonation attacks. However, there is still a strong demand for the standalone botnet-as-a-kit service because it allows threat actors to maintain full control of the malware, infrastructure, and operation.
In 2015, CTU researchers observed banking botnet activity originating from the 14 botnets listed in Figure 1. Analysis of configuration files associated with observed samples revealed that targets included customers of more than 1,500 financial institutions.
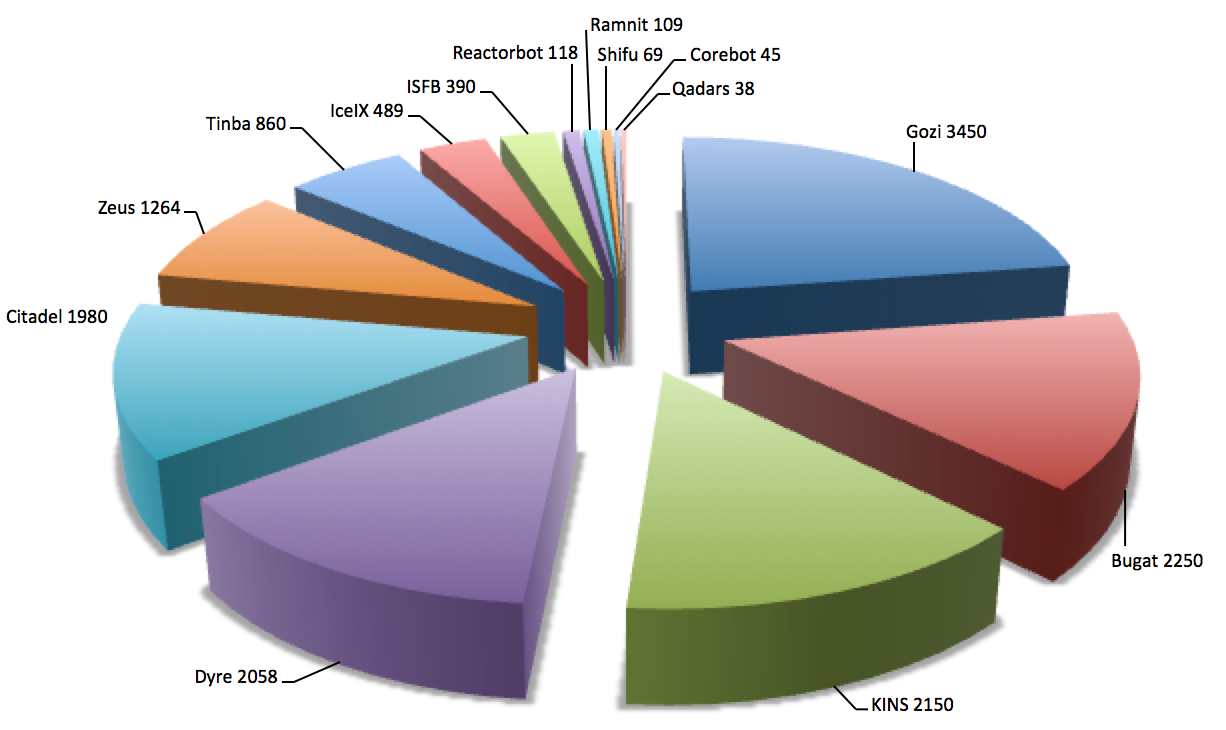
Figure 1. Prevalence of banking botnets in 2015 based on samples analyzed by CTU researchers. (Source: Dell SecureWorks)
The introduction of new targets in 2015 reflects the constant evolution of threat actors' tactics, techniques, and procedures (TTPs). The focus on cloud service providers, app stores, and tech stores suggests that cybercriminals are seeking ways to initiate mass infections on mobile platforms. Interest in targeting mobile banking services has also grown as the use of mobile devices has increased. Many mobile banking providers still use text messages to deliver strong 2FA, and smart phones are not always protected by security software. The addition of targets in the shipping, warehousing, and e-commerce industries reflects exploration of new ways to control money mule and shipping networks. Threat actors also continue to target social networking platforms, email services, employment portals, entertainment websites, hosting providers, phone companies, and dating portals to support social engineering and spam campaigns.
Banking botnets continued to target traditional banking and financial institution websites, corporate finance and payroll services, and stock trading organizations in developed countries with sizeable populations and wealthy residents (see Figure 2). In 2015, CTU researchers observed threat actors focusing on countries where institutions have weaker account security, and countries where international transactions are more difficult and require local intervention to launder money. There was a spike in attacks against banks and other financial institutions in the Asia-Pacific region, the Middle East, and Eastern Europe.
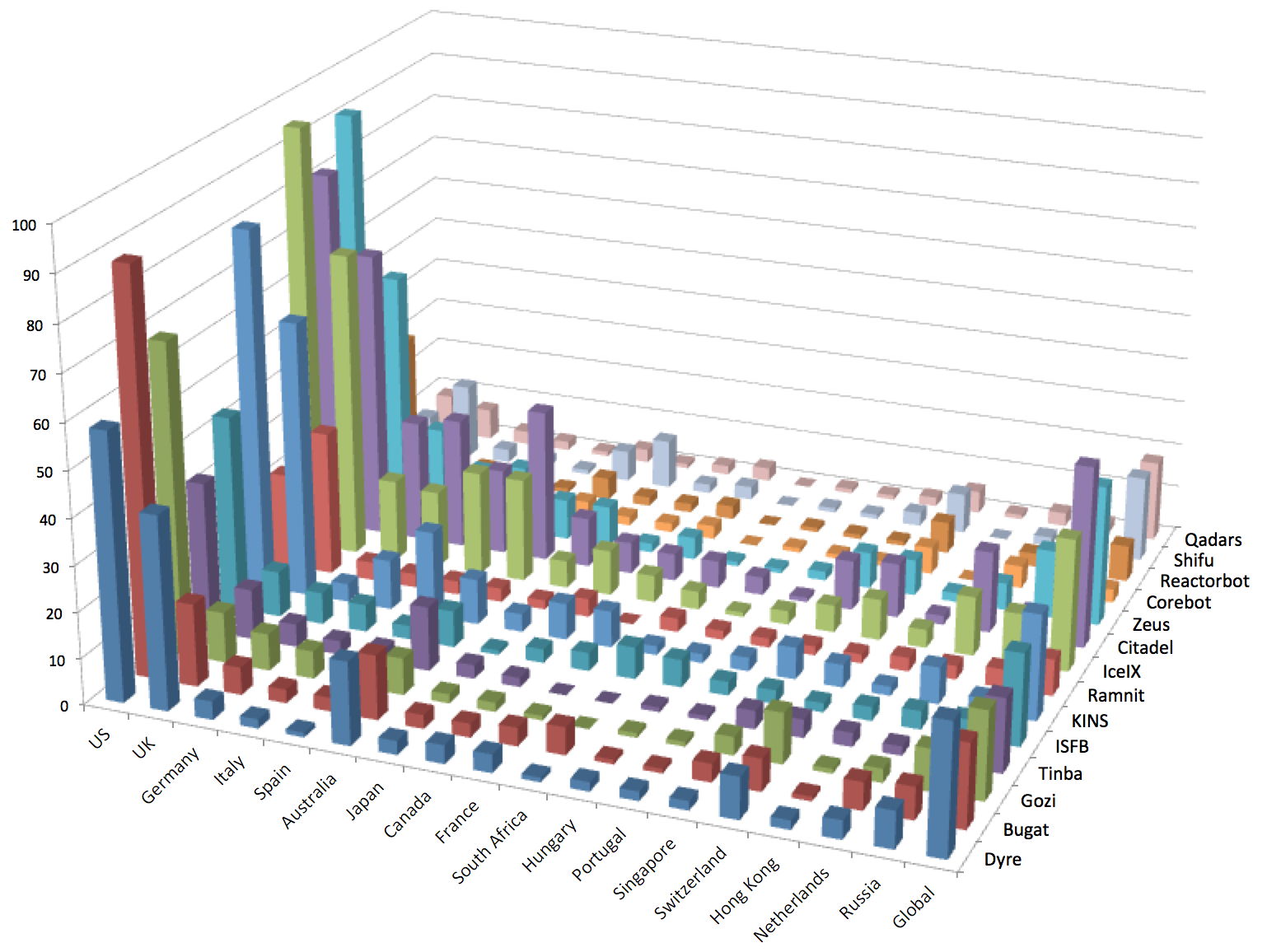
Figure 2. Countries targeted by banking trojans in 2015. The z-axis represents the number of targeted organizations. (Source: Dell SecureWorks)
Infection vectors
In 2015, banking trojans compromised systems via methods such as spam campaigns, downloader trojans, and drive-by download attacks using exploit kits.
- To avoid network perimeter blocking or monitoring, most of the trojans used port 80 (HTTP) or 443 (HTTPS) for communications between compromised systems and command and control (C2) servers. Increased use of HTTPS communication by major banking trojans makes surveillance and monitoring difficult.
- The botnets used four primary downloaders: Pony, Upatre, Gamarue (also known as Andromeda), and Kegotip. These downloaders serve as first-stage droppers/installers and use sophisticated techniques to avoid detection when dropping malware on a compromised system.
- Exploit kits including Angler, RIG, and Neutrino distributed banking trojans.
- In addition to traditional spam botnets like Cutwail, private spam mailers that operate multiple spam campaigns distributed banking trojans.
Features
Banking botnets have different features and technical proficiency. Although their primary focus is stealing financial information and using compromised systems for monetary gain, they also steal and use email credentials to compromise more systems. Banking botnets became more widespread, resilient, and evasive in 2015. Many of them now integrate multiple backup C2 solutions via backup DGA domains, use compromised routers as proxy servers to conceal actual C2 servers, host payloads on compromised websites, use peer-to-peer (P2P) networks to resist monitoring, and hide and protect their infrastructure and resist surveillance with anonymizing services such as Tor and I2P.
Cybercriminals often use infected computers as distribution channels to drop additional malware, and may use a combination of features to perform cyber fraud. Botnets may include features that perform a man-in-the-browser (MITB) attack to hijack a web session, that access a victim's computer using virtual network computing (VNC) and then redirect traffic to malicious websites, that control fraudulent transactions with backconnect, that capture important information via screenshots and video captures, that use proxies to tunnel traffic and conceal C2 activity, and that compromise mobile devices to circumvent security measures such as OTP or 2FA.
Active banking botnets
The following banking botnets affected financial institutions around the world in 2015.
Dyre
The Dyre banking trojan was originally identified by the CTU research team in June 2014. As of this publication, CTU researchers have not observed any new spam emails distributing Dyre since November 19, 2015, and the botnet's command and control (C2) infrastructure remains nonresponsive. The hiatus in Dyre botnet activity may be linked to a reported raid by Russian authorities in Moscow in November 2015. Before Dyre disappeared, it continued to incorporate refinements and new features in each iteration, and its advanced modular structure used web fakes and dynamic web injects to control the botnet. Dyre used SSL to encrypt all C2 communications, and it relied on a combination of standard crypto algorithms and RSA cryptography to digitally sign configuration files and malware plugins, preventing data tampering. Dyre hid its backend infrastructure behind a set of proxy servers that act as first-level C2 servers, and used DGA and the I2P anonymizing service to defeat surveillance and takedown efforts.
Dyre incorporated references to the United States, United Kingdom and Australia in its campaign names to reflect the malware distribution. For example, spam campaigns using U.S. lures dropped payloads with a U.S. campaign ID. CTU researchers observed more than 2,000 unique Dyre samples, and more than 150 targets were added in 2015, including cloud service providers, app stores, e-commerce and marketing sites, and online tech stores. CTU researchers identified more than 500 Dyre campaigns during 2015, with most targets located in the U.S., UK, Australia, and Switzerland.
Dyre primarily used the Cutwail spambot as a distribution channel, but the threat actors also used a private spam mailer. Upatre was the main downloader, but a new downloader known as Ruckguv was also used. Dyre dropped the Pushdo loader and the Kegotip credential stealer. On several occasions, CTU researchers observed commands to download the Neverquest variant of Gozi on the Dyre network, while the Gozi botnet was pushing commands to download Dyre on the Gozi network. This reciprocity may indicate a relationship between the Dyre and Gozi operators, possibly that the same threat actors are operating both botnets.
Gozi
The Gozi banking trojan, first discovered and named by the CTU research team in 2007, continues to be prominent. The Neverquest and ISFB variants of Gozi were both active in 2015.
Neverquest v1 and v2
CTU researchers first observed the v2 variant of Neverquest being distributed by a Cutwail spam campaign on September 23, 2015. A new build of Neverquest v1 was distributed via Cutwail on the same day. The threat actors updated the current variant while building and testing the new variant. Neverquest v1 became inactive around December 25, and the operation completely switched to Neverquest v2. Both variants are spread primarily through spam campaigns, redirecting victims to drive-by download exploit kits that install Gozi on compromised systems. Neverquest v1 used Chanitor as its first-stage downloader, and Chanitor downloaded Neverquest v1 payloads via Tor. Neverquest v2's first-stage downloader, Pony, downloads Neverquest v2 payloads from compromised websites.
Both Neverquest variants are divided into two parts: a dropper module and the main DLL module. The dropper loads a DLL that initializes the main DLL module. After a system is compromised, the DLL module connects to a predefined list of C2 servers and registers a bot. The C2 server responds with an encrypted configuration file that includes a list of banking websites and corresponding web inject scripts. Neverquest not only steals credentials from FTP, SMTP and POP applications, it can also harvest data from Google, Yahoo, Amazon AWS, Facebook, Twitter, and Skype. Threat actors use these accounts to distribute links to compromised websites to further spread Gozi and other malware. Similar to P2P Gameover Zeus, Neverquest operates with an affiliate model. The botnet is partitioned into sub-botnets, and each affiliate has access to its own subset of bots.
Within the first few weeks of Neverquest v2's introduction, CTU researchers identified ten different builds, indicating the botnet is in active development. The Neverquest v2 target list increased from 53 to more than 250 within first two weeks. While Neverquest v1 used Tor hidden services to push new C2 server lists, Neverquest v2 relies on hard-coded domains embedded inside each sample. Neverquest v2 uses different advanced encryption modules than Neverquest v1 for communication and configuration. The CTU research team identified more than 50 campaigns distributing Neverquest variants in 2015.
ISFB
ISFB, also called Ursnif, Papras, and Voslik, is derived from an early variant of Gozi. With its advanced capacity to steal bank account credentials, one-time-password (OTP) tokens, cookies, certificates, and other sensitive information, ISFB instantly became a popular alternative to the Zeus banking trojan. ISFB is a commercially available banking trojan that is available as a botnet kit. It is commonly distributed through exploit kits, spam campaigns, and existing botnets via pay-per-install. CTU researchers identified one ISFB threat group renting the spam service used by a threat group operating the Bugat v5 (Dridex) banking trojan. CTU researchers have observed 15 different versions of ISFB.
ISFB is divided into two parts: a dropper module and two versions of the main DLL module. The dropper determines the operating system's architecture, extracts and loads the corresponding 32-bit or 64-bit DLL module, and establishes persistence on compromised systems. ISFB includes a feature to configure bots that rely on DGA rather than on a set of hard-coded C2 domains and IP addresses. Multiple versions use either RC6 or Serpent to encrypt the HTTP query parameters. ISFB provides support for a large number of commands that enable the cybercriminals to control the botnet. The hash of each command is computed with the same cyclic redundancy check (CRC) algorithm used by Bugat v5.
Many threat actors using ISFB target specific regions. Several ISFB botnets target organizations in the UK, but the addition of targets in Saudi Arabia, Iran, Japan, Thailand, and Bulgaria indicate that the cybercriminals are shifting their focus toward countries where banking systems have weaker protection systems. CTU researchers have observed ISFB operators targeting a single bank in a new country for a few weeks, and then expanding to other banks from the same country if the test is successful. The CTU research team has tracked activities from more than 20 ISFB botnets and has captured configuration files associated with more than 750 unique targets.
Bugat v5 (Dridex)
The Bugat v5 (Dridex) variant of Bugat was introduced after the Gameover Zeus takedown. In the fall of 2015, the CTU research team collaborated with the UK National Crime Agency (NCA), the FBI, and the Shadowserver Foundation to take over Bugat v5, but it reemerged and rebuilt its botnet infrastructure.
Bugat v5 has four main components: a loader, a core module (DLL), a VNC module, and a backconnect module. Its modular architecture and hybrid peer-to-peer (P2P) network make it distinct from previous variants. Rather than nodes behaving autonomously and exchanging peer lists, configuration files, and binary updates with other peers, they tunnel almost everything to the backend infrastructure. Bots that perform node actions receive a special information packet that contains the location of an admin node (i.e., an upstream proxy). Similar to P2P Gameover Zeus and Gozi, Bugat v5 uses an affiliate model. The botnet is partitioned into sub-botnets, and each affiliate has access to its own subset of bots. CTU researchers have observed 16 sub-botnets: 120, 121, 122, 125, 126, 127, 200, 220, 223, 300, 301, 303, 305, 310, 320, and 888.
Bugat v5 is distributed primarily via Cutwail spam campaigns, using Microsoft Word or Excel file attachments that contain malicious macros. CTU researchers have observed Bugat v5 dropping the Kegotip credential stealer.
Tinba
Tinba's source code was leaked in mid-2014, and CTU researchers observed two new variants of Tinba in 2015. Tinba stages a system compromise via the legitimate Winver.exe Windows process. It then uses API hooking techniques to perform malicious operations via explorer.exe or svchost.exe. Tinba hooks WinINet APIs to perform browser injection and interception, and lowers browser security settings to perform browser injection. It uses RC4 to encrypt its C2 communications and relies on DGA as a fallback mechanism to phone home if the C2 communication fails. As part of its resilience mechanism, Tinba signs its commands and updates with a public key to guarantee they originated from a legitimate bot operator. CTU researchers have also observed a Tinba variant using a persistent user-mode rootkit and a generic form grabber.
Tinba is an affiliate-based botnet, and each affiliate targets a different region. During 2015, the CTU research team identified separate Tinba campaigns targeting banks and financial institutions in Russia, Poland, Germany, Italy, Netherlands, Romania, Japan, Indonesia, Singapore, and Malaysia. While sophisticated banking botnet such as Dyre, Bugat v5, and Gozi primarily focus on U.S., UK, and Australian banks and financial institutions, Tinba also focuses on targets in Asia. CTU researchers observed Tinba using campaign IDs similar to Bugat v5.
Ramnit
In early 2015, a joint effort between law enforcement and industry partners resulted in the seizure of servers and other infrastructure owned by the group behind Ramnit. On October 29, 2015, CTU researchers observed that Ramnit had reemerged and was spreading through the Angler exploit kit. The CTU research team identified six different Ramnit campaigns since its reemergence, targeting banks in the U.S., UK, Australia, Canada, and Finland.
The malware includes several components divided into small modules/plugins, including a dropper, a main DLL module, an MITB bundle, an FTP grabber, a VNC module, a form and cookie grabber, and an anti-antivirus module. Ramnit uses a configuration and web injects similar to Zeus. It injects its DLL module into newly created instances of explorer.exe or svchost.exe and periodically communicates with its C2 server. Ramnit uses pre-determined domain names generated by a DGA. The malware can receive and execute commands on behalf of a threat actor and can request additional RC4-encrypted modules and malware. To co-exist with other banking malware on a compromised system, Ramnit copies ntdll.dll and kernel32.dll to its local folder, which removes all in-line hooking for Ramnit when it loads. Ramnit generates a mutex name with a linear congruential generator (LCG) and uses the mutex to check if Ramnit has already infected the system.
KINS
First advertised in July 2013, KINS (also known as VMZeus and Zberp) is based on the leaked Zeus source code, and its toolkit also has three parts. However, it is significantly different from Zeus. KINS improvements have included revised cryptography, concealment of configuration files inside digital image files, sandbox detection, reporting of installed security product information, and command execution. Its “config steganography” feature allows the malware to disguise its configuration in digital image formats. CTU researchers observed two new KINS versions in 2015 that use an “invisible persistence” feature. The malware deletes its startup registry key when Windows starts and sets it again while Windows shuts down, evading antivirus (AV) software that scans for malware during system boot. Bugat v5 uses a similar technique. Changes to KINS' crypto module and VM-Opcodes architecture indicate that the developers are still actively maintaining the code.
CTU researchers observed KINS campaigns using the RIG exploit kit for distribution and dropping Gamarue (Andromeda) as a first-stage downloader.
Shifu
In April 2015, a new advanced banking trojan was discovered on the Internet. It was later identified as a variant of Shiz and was named Shifu. Shifu's architecture is heavily borrowed from Shiz, and it incorporated code from the Zeus and Gozi malware families to perform MITB attacks. Shifu's modular architecture supports separate modules for anti-research, anti-VM, anti-sandbox, web injects, keylogging, screenshots, a certificate grabber, and a bot control module that is similar to other remote access tools. The bot control module allows the operator to select which additional modules to download and install. Shifu can accept commands from a C2 server and can download additional modules from remote servers. CTU researchers observed a RAM-scraper module that can scrape memory for credit and debit card track data from infected systems that are point-of-sale (POS) endpoints. Shifu also has a module that allows it to search for “.tok” files, which store tokens used to authorize users on banking platforms.Shifu registers each infected bot with the C2 server, providing information such as malware version, OS uptime, OS version, local time, and installed AV software. It communicates over HTTPS and uses a self-signed certificate to secure communication. Shifu can accept commands from its botnet operator to perform actions including update malware, load additional malware, kill operating system, erase all cookies, and search local files.
The CTU research team identified six different Shifu versions in 2015. CTU researchers observed campaigns targeting banks and financial institutions in Japan, the UK, Germany, Austria, and Italy.
Corebot
Corebot was discovered in the fall of 2015, and initial samples indicated that it was simple malware without any web inject capability. Enhancements in a second iteration led CTU researchers to identify Corebot as a fully-capable banking trojan that supports browser hooking, form grabbing, MITM attacks, web injects (including dynamic web inject download from remote servers), and VNC for remote control. It has two parts: a loader and a main module. It uses DGA as a fallback mechanism. Analysis of Corebot's web inject capability revealed that it displays a wait notice instructing a victim to stay online while the botnet operator connects to the victim's computer over VNC to perform fraud. Like other banking trojans, Corebot also injects into the Internet Explorer (IE), Firefox, and Chrome browsers to steal web sessions. Corebot uses RC4 for encryption, and based on its RC4 keys and communication protocol, the CTU research team believes that Corebot has a kit-based architecture.
The initial Corebot configuration targeted 55 different banks and financial institutions across the U.S., UK, and Canada. CTU researchers observed later Corebot configurations targeting 123 unique banks and financial institutions in the U.S., UK, Canada, Australia, and Europe.
Reactorbot
The CTU research team first discovered a spam campaign distributing Reactorbot samples in early 2015. The Rovnix rootkit is often bundled with Reactorbot, so many AV signatures incorrectly identify Reactorbot as Rovnix. ISFB is also often bundled with Rovnix. Initially, Reactorbot was distributed via a Word attachment with embedded malicious macros, a technique also used by Bugat v5. The Word file prompts a victim to enable macros, which allows the malicious macros in the attachment to download the malware payload from a remote compromised server. Subsequent campaigns also used spam themes with malicious attachments.
Reactorbot is composed of three components: a dropper, a bootkit (not always included), and a main module DLL. Reactorbot uses DGA as a fallback mechanism, and the DGA uses .com, .net, .biz, and .cn TLDs for domain generation. Reactorbot enumerates all running processes and checks for process names as part of its anti-sandbox check. It checks for AV program names during its anti-AV checks.
The CTU research team identified five Reactorbot campaigns in 2015. The initial version of Reactorbot primarily targeted banks and financial institutions in Germany and Netherlands. Subsequent campaigns added targets in the U.S., UK, Australia, Japan, and Belgium.
Qadars
Qadars has been active since the spring of 2013, but the CTU research team identified an increase in Qadars activity in 2015. Qadars has two components: a dropper and a main module. It is heavily based on Zeus source code, even sharing its version number structure with Zeus and being identified as Zbot by many AV vendors. Qadars supports many Zeus-like commands that give the operator remote control (e.g., upload, update, start, stop, reboot, and uninstall). It uses an uncommon persistence mechanism, scheduling a task execution at the next login. It uses AES in ECB mode and a Base64 crypto module to encrypt its network communication. Qadars' network communication protocol follows a well-formatted structure to exchange encryption keys. Many Qadars web injects include Android mobile components.
CTU researchers observed Qadars targeting mobile users, particularly in Australia, Netherlands, Canada, and Italy, as well as major banks and financial institutions in the U.S., UK, and India. Qadars campaigns target specific regions, and CTU researchers observed campaigns targeting the U.S., UK, Canada, and Australia during 2015.
Zeus
The Zeus banking trojan (originally called PRG or Zbot) was first discovered by the CTU research team in 2007. Since the Zeus source code was leaked in 2011, almost all banking trojans have incorporated Zeus features. Zeus is still very effective, compromising thousands of systems and resulting in the theft of hundreds of thousands of dollars. The Zeus toolkit contains three parts: a builder that allows the attacker to build the trojan, the Trojan horse malware that modifies a compromised computer and steals information, and a C2 web panel that monitors and controls the trojan and stores stolen data. Because the Zeus architecture is simple and the Zeus toolkit is freely available in underground market, it is used on many compromised servers. CTU researchers did not observe any new versions of Zeus in 2015.
IceIX
IceIX is based on the Zeus source code and does not appear to offer any unique functionality. The minor differences in IceIX are the inclusion of the IceIX version rather than Zeus version number in configuration files, the use of a slightly modified RC4 algorithm instead of the standard RC4, and a custom HTTP POST request to download IceIX's dynamic configuration. The CTU research team did not identify any new versions of IceIX in 2015.
Citadel
The Citadel banking trojan is based on the leaked Zeus source code and, like Zeus and IceIX, has three parts. Citadel kits are circulating in underground markets, but its development appears to have stalled. The latest version observed by CTU researchers as of this publication is from April 2014, and there were no significant changes in 2015.
Conclusion
Some old banking trojans reappeared and increased their activity in 2015. Takedowns and arrests temporarily reduced botnet activity, but the reemergence of Bugat v5 and Ramnit reflected the determination of cybercriminals targeting the financial vertical. Botnets are part of a well-organized service industry that is constantly improving and evolving. Threat actors compete for the same share of the market, and to surpass their competition they expand operations to untapped markets and locations where they can apply existing techniques. These organized groups continually explore new ways to steal money from victims, as illustrated by the increase in ransomware and mobile malware in 2015.
Although CTU security intelligence researchers did not observe much innovation in fraud techniques in 2015, traditional solutions to protect against threats prove ineffective against modern banking trojans. Small and mid-sized businesses have become popular targets for online banking fraud through credential theft and subsequent fraud via Automated Clearing House (ACH) transactions or wire transfers. Credentials used for online banking or other finance activities are at exceptional risk. An organization's response may include resetting credentials and reviewing transactions for a compromised account to identify anomalies. Automated attack detection requires collecting, combining, and automatically analyzing data to extract relevant information and apply security countermeasures. Combining this data with intelligence on known botnets will help enlarge the knowledge base for identifying attacks and selecting appropriate attack mitigation tools.