Cybersecurity has historically been viewed as a technological challenge. The operative theory has been that the best way to stop malicious activity is to provide your SOC with as many different types of advanced cybersecurity technology as you can afford — because the more tools you have, the better.
Right? Not so fast.
That theory may sound logical. But it's problematic for several reasons:
- The increasingly stealthy behavior of threat actors
- The undersupply of skilled cybersecurity professionals
- Limited cybersecurity budgets
- Alert fatigue and its adverse effects on SOC staff performance
- The importance of rapid, effective response to discovered threats
In short: It isn't enough to spend money gathering data and generating alerts. To keep your organization safe, you must excel at process and efficiency as well as the technology of anomaly detection.
To do that, you need to move beyond technologies of the past, to solutions that will make your organization future ready.
SIEM + IDS + EDR = TMI
There's nothing wrong per se with spending money on technologies such as SIEM and IDS — which can both be very useful for cyber defense.
The problem is that organizations have finite security budgets. Every dollar needs to stretch, and every investment needs to be useful for the organization's specific and unique needs. And here's another angle: given constrained security staff headcounts, more information isn't necessarily better. After all, does all that information lead to more effective action?
SOC staff simply can't afford to spend their days clearing false positives, chasing true-but-trivial, low-risk positives, and trying to determine the underlying nature of threats that have triggered serious alerts.
That last issue is particularly problematic, because time is of the essence in thwarting threat actors. You and your team need to piece together the facts quickly to identify the exact nature of that threat — an essential requirement before you can effectively neutralize an attack.
The objective can't be to simply generate more data.
You need a solution that delivers relevant, actionable insight to the people who need it — without throwing a lot of distracting data “noise” at them as well.
And there it is. Because unfortunately, “noise” is exactly what happens when organizations spend too much money and rely too heavily on telemetry and detection technology. They flood the limited attention space of their SOC staff with inputs, creating a counterproductive bottleneck in SOC workflow. It's almost like some kind of self-inflicted DDoS attack. And it's not making anyone safer.
A smarter, leaner approach
Rather than leading with technology, SOCs need to lead with knowledge — specifically the knowledge provided by threat intelligence. Threat intelligence tells your SOC what to look for. Once your SOC finds something, threat intelligence tells them what it is.
The result: Reduced risk due to faster, more decisive interdiction.
An excessively data-centric approach to cyber defense, driven primarily by the combination of raw telemetry and SIEM, does just the opposite.
It generates lots of activity, much of which is unproductive or even counterproductive. And that's a big problem when your headcount is constrained and time is of the essence.
Here's a simplified way to visualize the difference between these two approaches:
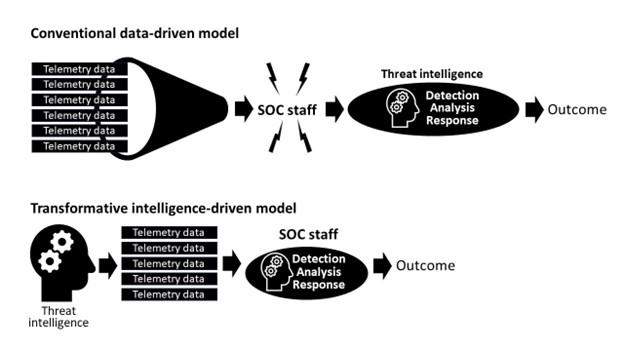
Organizations that put the data “cart” before the threat intelligence “horse” force their SOC staff — whether that staff is internal, external, or hybrid — to wrestle with more unfiltered information, perform more unassisted analysis, and execute more manual responses.
Organizations that process their telemetry data through the lens of comprehensive, up-to-date threat intelligence ease the burden on their SOC staff and achieve faster, more successful outcomes.
Threat intelligence-enabled XDR
Because they function primarily as telemetry generators and aggregators, SIEM, IDS, and conventional EDR are incapable of enabling a threat intelligence-driven SOC.
There's only one current technology that can enable the transformation of your SOC — taking operations from slow and labor-intensive, data-driven to leaner, effective, and intelligence-driven. The answer is extended detection and response (XDR) with threat intelligence built directly into the platform.
A TI-enabled XDR platform does this for you in two ways.
First, it aggregates telemetry from all your data sources: endpoints, networks, the cloud, etc. It thus serves the function of a SIEM at far less cost — while also leveraging your existing investments in EDR, IDS, and other telemetry generators.
Second, it applies the insights into threat actor behaviors gathered by threat researchers in the form of built-in threat detectors. These detectors use AI, machine learning, and other methods to match disparate telemetry data against known indicators of malicious activity. SOC staff get more reliably alerted to both the potential presence of a threat and the exact nature of that threat.
But TI-enabled XDR isn't just about faster, more reliable detection. XDR with integrated threat intelligence is better at identifying the exact nature of detected threats, making it ideal for triggering automated responses. This response automation neutralizes attacks faster while also easing burdens on overworked SOC teams.
In the case of a platform like Secureworks' Taegis™ XDR, new threat intelligence can continuously and rapidly drive the creation of new threat detectors — so that your ability to defend your organization can keep pace with the relentless innovation of your adversary.
Learn more about how you can enhance the effectiveness and efficiency of your SOC with an intelligence-driven approach to cyber defense.