Although international law enforcement operations have successfully disrupted prominent ransomware schemes, cybercriminals continue to demonstrate their resilience and adaptability. In 2025, Secureworks® Counter Threat Unit™ (CTU) researchers observed the DragonForce and Anubis ransomware operators introducing novel models to attract affiliates and increase profits.
DragonForce: Distributed affiliate branding model
DragonForce emerged in August 2023 as a traditional ransomware-as-a-service (RaaS) scheme. After the operators began advertising the offering on underground forums in February 2024, the number of victims posted to the associated leak site steadily grew to 136 as of March 24, 2025. In a March 19, 2025 underground post, DragonForce rebranded itself as a "cartel" and announced its shift to a distributed model that allows affiliates to create their own "brands" (see Figure 1).
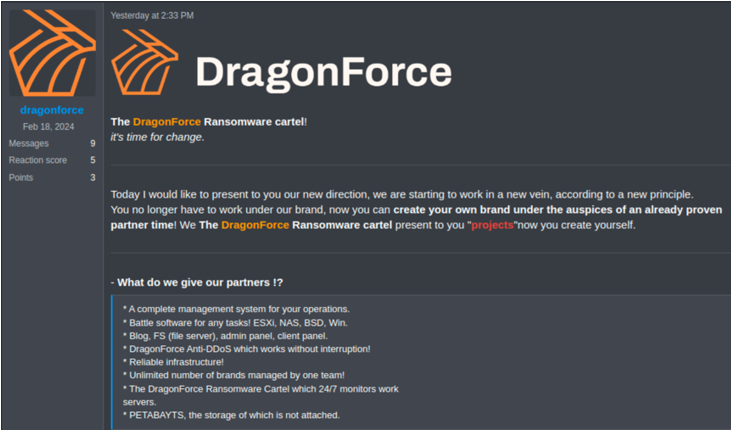
Figure 1. DragonForce announcement about the shift to a customizable affiliate model. (Source: Secureworks)
In this model, DragonForce provides its infrastructure and tools but doesn't require affiliates to deploy its ransomware. Advertised features include administration and client panels, encryption and ransom negotiation tools, a file storage system, a Tor-based leak site and .onion domain, and support services.
This approach differentiates DragonForce from other RaaS offerings and may appeal to a range of affiliates. For example, the established infrastructure and accessible tools expand opportunities to threat actors who have limited technical knowledge. Even sophisticated threat actors may appreciate the flexibility that allows them to deploy their own malware without creating and maintaining their own infrastructure. By broadening its affiliate base, DragonForce can increase its potential for financial gain. However, the shared infrastructure does introduce risk to DragonForce and its affiliates. If one affiliate is compromised, other affiliates' operational and victim details could be exposed as well.
Anubis: Three extortion options
The Anubis operators use a different tactic to entice affiliates. This extortion scheme, which was first advertised on underground forums in late February 2025, offers three modes:
- RaaS – a traditional approach that involves file encryption and offers affiliates 80% of the ransom
- Data ransom – a data theft-only extortion option in which affiliates receive 60% of the ransom
- Accesses monetization – a service that helps threat actors extort victims they've already compromised and offers affiliates 50% of the ransom
The "data ransom" option involves publishing a detailed "investigative article" to a password-protected Tor website. The article contains an analysis of the victim's sensitive data. The victim is granted access to that article and is given a link to negotiate payment. If the victim does not pay the ransom, the threat actors threaten to publish the article on the Anubis leak site. The operators increase pressure by publishing victim names via an X (formerly Twitter) account. The threat actors claim they will also notify the victims' customers about the compromise. These tactics have been used by multiple ransomware groups, but the Anubis operators threaten to take the notifications a step further. The advertisement indicates that they will report the compromises to the following authorities:
- The UK Information Commissioner's Office (ICO), which focuses on data protection and information rights
- The U.S. Department of Health and Human Services (HHS)
- The European Data Protection Board (EDPB), which ensures consistent application of the General Data Protection Regulation (GDPR)
This escalation strategy has not been widely adopted but does have precedent. In November 2023, the GOLD BLAZER threat group reported an ALPHV (also known as BlackCat) compromise to the U.S. Securities and Exchange Commission (SEC) after a victim failed to pay a ransom. CTU™ researchers are unaware of other ransomware groups filing reports with regulatory or compliance organizations.
The "accesses monetization" option focuses on post-compromise activity by helping affiliates extract ransom payments from their victims. Similar to the data theft-only option, the affiliate receives a detailed analysis of the victim's data that they can use to increase pressure during ransom negotiations (see Figure 2).
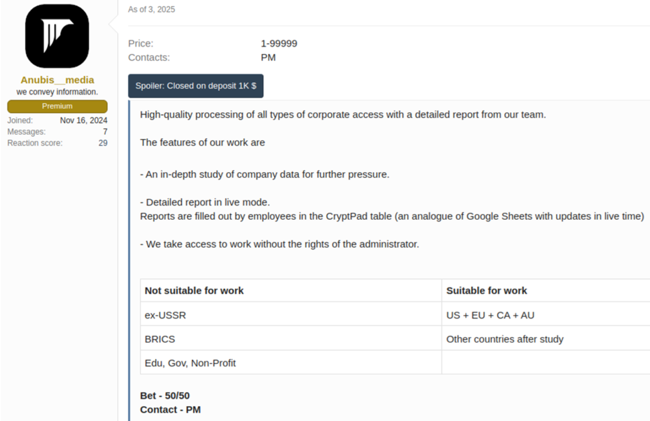
Figure 2. Advertisement for Anubis "accesses monetization" service. (Source: Secureworks)
The advertisement specifies that victims in certain regions and sectors are excluded. As with many ransomware groups, the Anubis operators restrict targeting of organizations in post-Soviet states. Additionally, they exclude the countries that compose the BRICS intergovernmental organization (Brazil, Russia, India, China, South Africa, Egypt, Ethiopia, Indonesia, Iran, and the United Arab Emirates). While the advertisement indicates that Anubis explicitly restricts targeting of educational institutions, government entities, and non-profit organizations, it does not mention healthcare entities. Healthcare organizations may be desirable targets in the Anubis model due to their access to an abundance of sensitive information and their regulatory compliance requirements.
Moving forward
The Secureworks 2024 State of the Threat report reinforces that ransomware remains a significant threat to organizations. As operations are taken down by law enforcement efforts, other schemes emerge. However, third-party reporting indicates that ransom payments are decreasing. This trend is supported by an increase in the number of victims posted to ransomware leak sites, as those posts reflect victims who haven't paid the ransom. Cybercriminals are motivated by financial gain, so they are adopting innovative models and aggressive pressure tactics to shift the trend in their favor.
While the decision whether to pay a ransom is based on an organization's individual risk assessment, a ransom payment doesn't guarantee that the victim will regain access to their data or avoid public exposure. A proactive preventative approach can be more effective. CTU researchers recommend that organizations regularly patch internet-facing devices, implement phishing-resistant multi-factor authentication (MFA) as part of a conditional access policy, maintain robust backups, and monitor their network and endpoints for malicious activity. Additionally, organizations should develop and regularly test an incident response plan to quickly remediate ransomware activity. The U.S. Cybersecurity & Infrastructure Security Agency (CISA) and the UK National Cyber Security Centre (NCSC) have also published guidance for mitigating the risk of ransomware attacks.
Learn more about how threat actors have historically adapted ransomware operations in the Secureworks Ransomware Evolution report. If you need urgent assistance with an incident, contact the Secureworks Incident Response team.