Cybercriminals focus on financial gain, often conducting opportunistic attacks without regard for the potentially devasting impact on their victims. For example, sextortion scams rely on baseless and crude scare tactics to demand ransom payments. The targeting is indiscriminate, and the emails contain falsified information to coerce victims into believing they have been recorded in a potentially humiliating scenario.
Sextortion is not a new tactic; Secureworks® Counter Threat Unit™ (CTU) researchers have tracked the scams since at least 2018. CTU™ researchers first observed the Phorpiex botnet (also known as Trik) delivering sextortion email spam in 2019, and the campaigns have continued into late 2024 (see Figure 1). In these Phorpiex-based scams, the alleged videos do not exist but the threat actors attempt to leverage recipients’ fear of exposure. Very little has changed in these attacks, suggesting that the tactics continue to be successful.
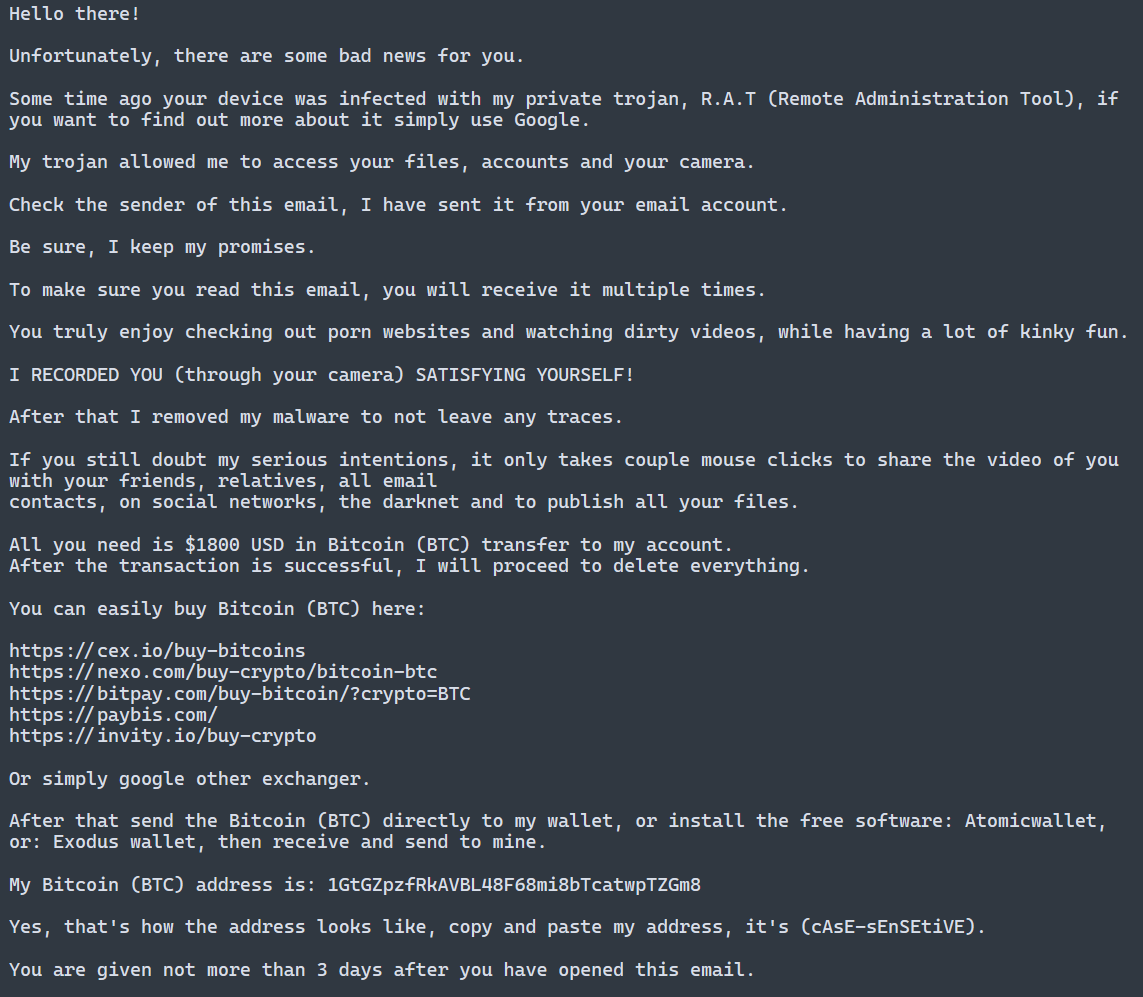
Figure 1. Example sextortion email delivered by the Phorpiex botnet. (Source: Secureworks)
These ongoing attacks are a reminder to be aware of this style of extortion in addition to other methods such as ransomware. The cybercriminals have no qualms about resorting to crude methods to elicit money.
To mitigate exposure to this malware, CTU researchers recommend that organizations use available controls to review and restrict access using the indicators listed in Table 1. Note that IP addresses can be reallocated. The IP addresses may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
|---|---|---|
| 185.215.113.66 | IP address | Phorpiex C2 server |
| 77.91.77.92 | IP address | Phorpiex C2 server |
| 91.202.233.141 | IP address | Phorpiex C2 server |
| 193.233.132.177 | IP address | Phorpiex C2 server |
| 5.42.96.117 | IP address | Phorpiex C2 server |
Table 1. Indicators for this threat.
Learn more about ransomware attacks in the 2024 State of the Threat report.