Secureworks® Counter Threat Unit™ (CTU) researchers are investigating network infrastructure links between North Korean IT worker schemes and a 2016 crowdfunding scam. The CTU™ research team attributes the IT worker schemes to the NICKEL TAPESTRY threat group.
In September 2018, the U.S. Department of Treasury's Office of Foreign Asset Control (OFAC) designated two information technology companies as violating sanctions, including operating as front companies to facilitate employment of North Korean IT workers and channeling illicit revenue to North Korea (officially the Democratic People's Republic of Korea (DPRK)) from overseas IT workers. The designated companies were China-based Yanbian Silverstar Network Technology Co., Ltd (“Yanbian Silverstar”) and Russia-based Volasys Silver Star. Yanbian is a Korean autonomous prefecture in Jilin, China, located near China's border with North Korea (see Figure 1).
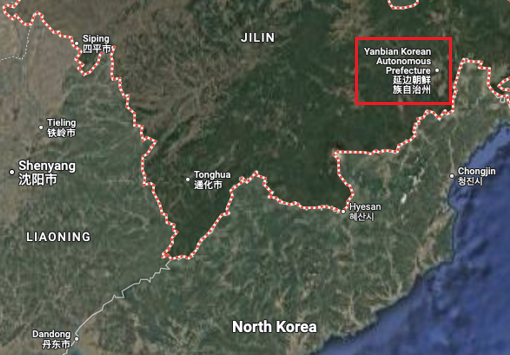
Figure 1. Location of Yanbian Korean autonomous prefecture. (Source: Google Maps)
According to a U.S. Federal Bureau of Investigation (FBI) affidavit filed in October 2023, multiple accounts used by Yanbian Silverstar freelancers were accessed between 2018 to 2019 from IP address 36 . 97 . 143 . 26 . This IP address resolves to a dedicated server geolocated in Jilin, China. The affidavit provides evidence that North Korean IT workers were living in China and working at Yanbian Silverstar. The CEO of Yanbian Silverstar and Volasys Silver Star, a North Korean national named Jong Song Hwa, was also designated in the affidavit.
One domain name associated with the Silver Star front companies (silverstarchina . com) was used as a reference to help North Korean IT workers surreptitiously obtain freelance jobs. After the domain was seized in 2024, the registrant email address (jinmaolin0628 @ hotmail . com) was publicly visible in the historical WHOIS record data (see Figure 2). This email address was previously hidden behind WHOIS privacy protection. The Chang Bai Shan Dong Lu registrant street address matches the reported location of Yanbian Silverstar offices located in the Yanbian prefecture. This same registrant email and street address were also listed in the registration data of several other domain names.
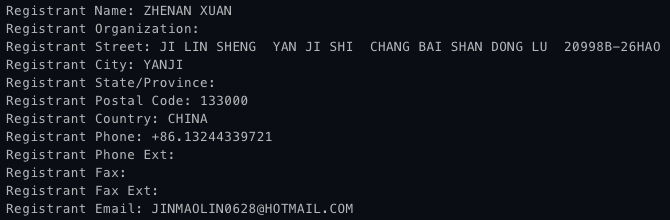
Figure 2. WHOIS data for silverstarchina . com. (Source: Secureworks)
CTU researchers discovered that one of those domain names (kratosmemory . com) was linked to a 2016 IndieGoGo crowdfunding campaign. The campaign advertised a Kratos portable wireless memory device (see Figure 3). However, buyer comments indicate that the campaign was a scam and that the campaign backers never received a product or refund from the seller.

Figure 3. Kratos campaign on IndieGoGo. (Source: Secureworks)
Around mid-2016, WHOIS registrant information for kratosmemory . com was updated to reflect a different persona named Dan Moulding (see Figure 4). This persona name matches the IndieGoGo user profile for the Kratos scam. CTU researchers have not observed this persona in registrant data for other domains.
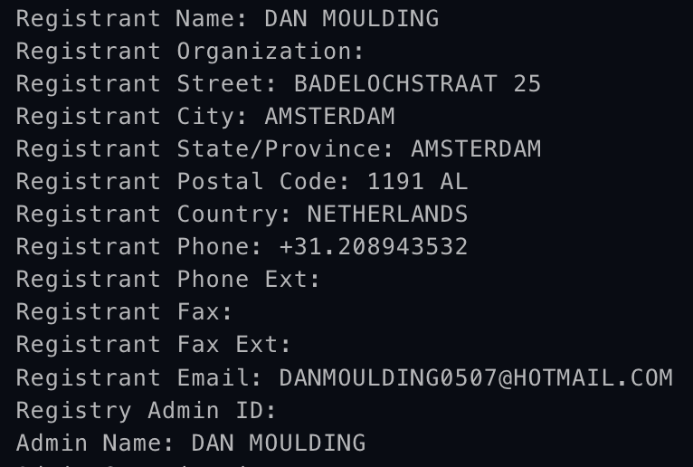
Figure 4. WHOIS data for kratosmemory . com as of June 22, 2016. (Source: Secureworks)
Based on the IndieGoGo campaign page, the scam garnered roughly $20,000 USD. This 2016 campaign was a low-effort, small monetary-return endeavor compared to the more elaborate North Korean IT worker schemes active as of this publication. However, it showcases an earlier example of North Korean threat actors experimenting with various money-making schemes. The network infrastructure overlap between the crowdfunding and IT worker campaigns indicates an association between the IndieGoGo scam operators and the NICKEL TAPESTRY threat group.
To mitigate exposure to this malware, CTU researchers recommend that organizations use available controls to review and restrict access using the indicators listed in Table 1. Note that IP addresses can be reallocated. The domains and IP address may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
|---|---|---|
| 36.97.143.26 | IP address | Used in NICKEL TAPESTRY operations |
| silverstarchina.com | Domain name | Seized infrastructure used in NICKEL TAPESTRY operations |
| kratosmemory.com | Domain name | Linked to a 2016 crowdfunding scam and known NICKEL TAPESTRY operations |
Table 1. Indicators for this threat.
Read more about North Korean IT worker schemes in our 2024 State of the Threat report.