Operation Cronos continues
On September 30, 2024, the UK's National Crime Agency (NCA), U.S. Federal Bureau of Investigation (FBI), and Europol again resurrected the LockBit leak site to announce additional actions against the ransomware scheme and its affiliates. The site displayed a countdown prior to exposing tiles containing information about the joint investigation and ongoing activity under Phase 3 of Operation Cronos (see Figure 1).
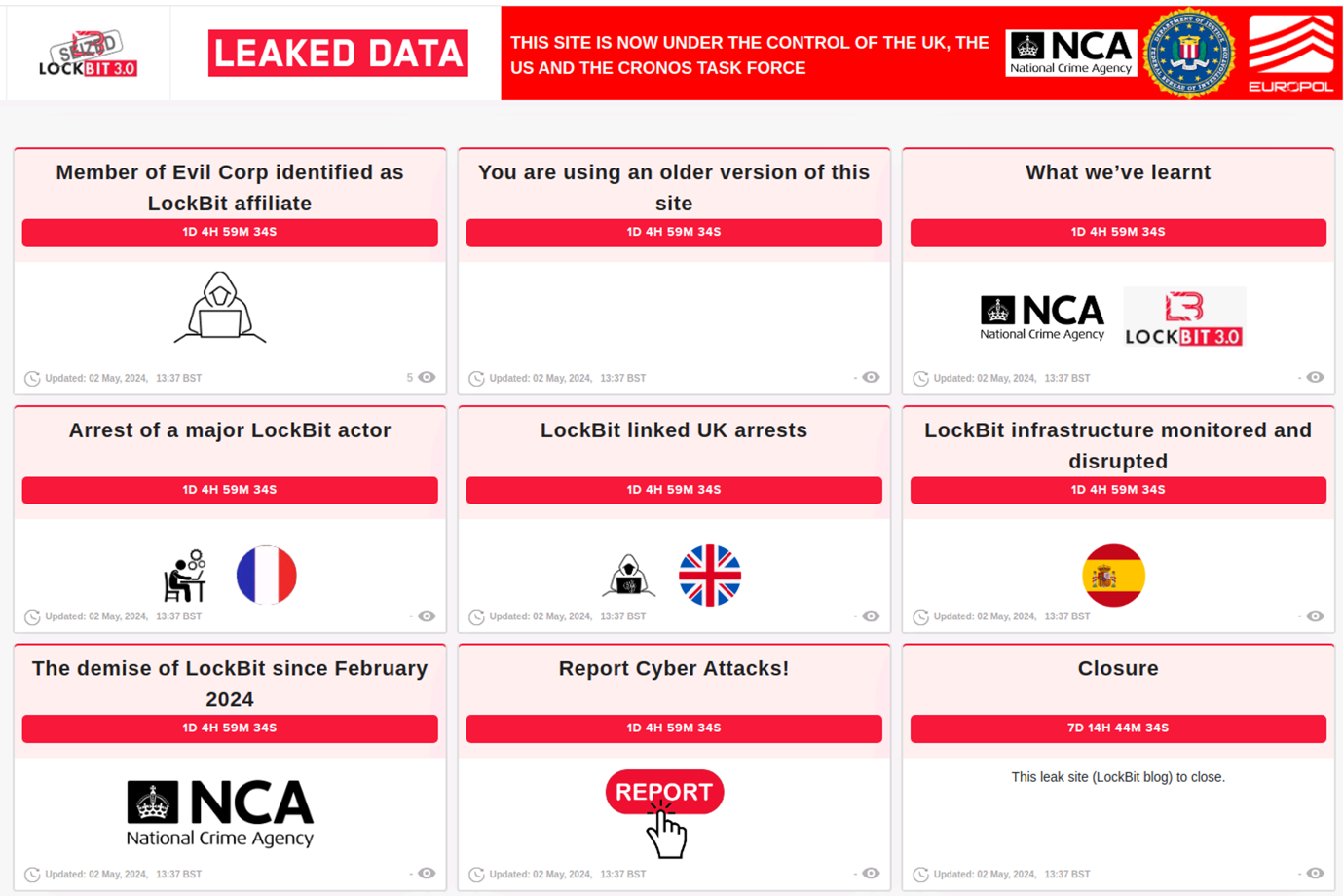
Figure 1. Resurrected leak site outlining law enforcement actions against LockBit co-conspirators. (Source: Secureworks)
Arrests and sanctions
The content of each tile was revealed on October 1 at 10:15 am EDT and mentions several arrests:
- An individual identified as a LockBit developer was arrested at the request of French authorities while on vacation in an unidentified location outside Russia.
- An alleged LockBit affiliate and an individual involved in money laundering were arrested in the UK.
- The Spanish Guardia Civil arrested the owner of a bulletproof hosting service and seized nine servers hosting LockBit infrastructure.
Other revelations include a summary of insights the NCA learned throughout the investigation and a description of how the LockBit operation had been impacted since Phase 1 of Operation Cronos in February. A notable highlight is confirmation that a member of the Evil Corp cybercrime group (which Secureworks® Counter Threat Unit™ (CTU) researchers track as GOLD DRAKE) operated as a LockBit affiliate. The NCA established a separate Tor-based website to detail the discovery and law enforcement actions against the group (see Figure 2).
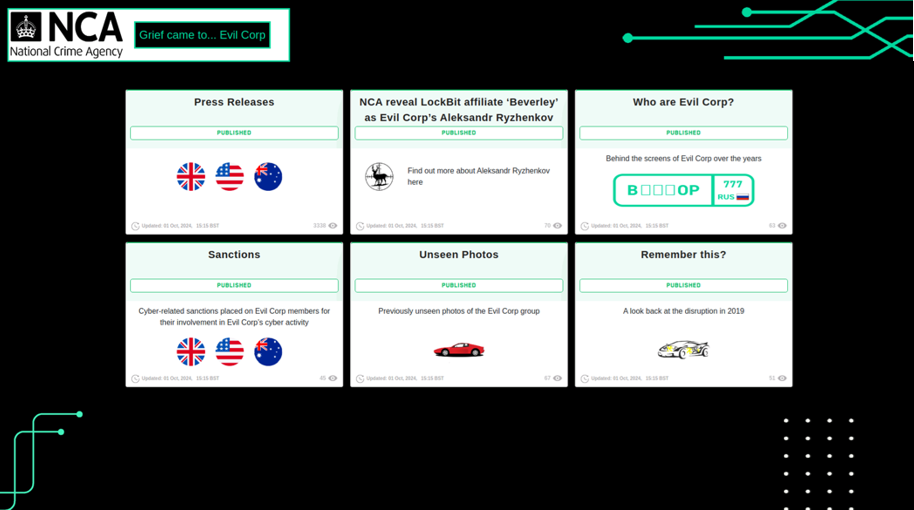
Figure 2. Tor website detailing the NCA's investigation into Evil Corp. (Source: Secureworks)
The website links to a history of the group's activities and details sanctions against associated individuals and business entities (see Table 1). Many of the individuals performed supporting roles in Evil Corp operations.
| Individual/entity | Designating authority | ||
|---|---|---|---|
| U.S. | UK | Australia | |
| Maksim Yakubets | X | X | X |
| Igor Turashev | X | X | X |
| Aleksandr Ryzhenkov | X | X | X |
| Eduard Benderskiy | X | X | |
| Vadim Pogodin | X | X | |
| Aleksey Shchetinin | X | X | |
| Beyat Ramazanov | X | X | |
| Viktor Yakubets | X | X | |
| Sergey Ryzhenkov | X | X | |
| Denis Gusev | X | X | |
| Dmitriy Smirnov | X | X | |
| Artem Yakubets | X | X | |
| Ivan Tuchkov | X | X | |
| Andrey Plotnitskiy/Kovalskiy | X | X | |
| Dmitriy Slobodskoy | X | X | |
| Kirill Slobodskoy | X | X | |
| Vympel-Assistance LLC | X | ||
| Solar Invest LLC | X | ||
Table 1. Individuals and entities sanctioned by U.S., UK, and Australian authorities for involvement in Evil Corp-related cybercrime.
Maksim Yakubets and Igor Turashev were previously sanctioned by the U.S. Office of Foreign Assets Control (OFAC) as members of Evil Corp in 2019. The UK's Foreign Commonwealth and Development Office (FCDO) and Australia's Department of Foreign Affairs and Trade (OFAT) have formally issued sanctions as well. Aleksandr Ryzhenkov, identified as Yakubets' second-in-command by the NCA, is also now sanctioned by all three authorities.
Some of the other individuals on the list are members of Yakubets' family. Viktor Yakubets is Maksim's father, who in 2021 denied that his son was engaged in criminal activity. Sanctions also extend to Maksim's brother (Artem Yakubets), cousins (Kirill and Dmitry Slobodskoy), and father-in-law (Eduard Benderskiy). Benderskiy owns the two sanctioned companies: Vympel-Assistance and Solar Invest.
As chairman of the Vympel Charitable Fund for Former FSB Spetsnaz Officers, Benderskiy allegedly holds considerable sway in the Russian state. His support and protection of GOLD DRAKE members provide them the freedom to operate without unwanted interference. Benderskiy reportedly organized the assassination of a Georgian dissident in Berlin in August 2019. The individual prosecuted and imprisoned for that crime, Vadim Krasikov, was released in August 2024 as part of a high-profile prisoner swap between the U.S. and Russia. Krasikov was warmly greeted by Vladimir Putin upon his return to Moscow.
Beyond Benderskiy's protection, GOLD DRAKE's links to Russian state-sponsored activity are less clear. The involvement identified by law enforcement appears to pre-date a 2019 indictment against the group, in which the FBI claimed that Maksim Yakubets ("aqua") was employed by Russia's Federal Security Service (FSB). According to the NCA's documentation about Evil Corp's history, Russian intelligence services tasked the group with conducting cyberattacks and espionage against NATO allies prior to 2019.
In addition to the sanctions, the U.S. Department of Justice (DOJ) unsealed an indictment against Aleksandr Ryzhenkov for his involvement in deploying the BitPaymer ransomware. The indictment does not reference his use of LockBit, but the resurrected leak site describes Ryzhenkov as a LockBit affiliate known as "Beverley" who "made over 60 LockBit ransomware builds and sought to extort at least $100 million [USD] from victims in ransom demands." The NCA associates Ryzhenkov with the UNC2165 group that represents "an evolution of Evil Corp affiliated actors."
GOLD DRAKE evolution
In 2022, Mandiant publicly disclosed that UNC2165 was a possible affiliate of the LockBit ransomware-as-a-service (RaaS) scheme. This revelation prompted the LockBit administrator to add Mandiant's name to the leak site in retaliation and claim that the company had been attacked by a LockBit affiliate. However, the tile associated with the "leak" just denounced Mandiant's claim that LockBit was working with Evil Corp.
GOLD DRAKE has deployed multiple ransomware variants since U.S. sanctions in 2019 made it effectively illegal for any organization incorporated in the U.S. to pay a ransom to Evil Corp. From July 2017 to early 2020, GOLD DRAKE developed and distributed the BitPaymer ransomware during post-intrusion attacks facilitated by Dridex. The threat actors developed and distributed the WastedLocker ransomware from May 2020. Between December 2020 until around March 2021, GOLD DRAKE distributed the Hades, Phoenix CryptoLocker, and Payload.Bin ransomware in name-and-shame attacks. The ransomware changes, abandonment of signature tools, and modification of intrusion techniques were likely intended to prevent victims from realizing that they were paying the group.
Members of GOLD DRAKE have been engaged in various forms of cybercriminal activity since at least 2011. Maksim Yakubets was a member of Yevgeniy Bogachev's Business Club (GOLD EVERGREEN) and actively engaged in the administration of the Gameover Zeus botnet using the "aqua" persona. After law enforcement and industry partners such as Secureworks took down Gameover Zeus in May 2014, GOLD DRAKE began operating the Dridex (also known as Bugat v5) botnet in high-volume campaigns intended to infect large numbers of individual systems. A 2015 takedown by law enforcement and partners including Secureworks temporarily deterred Dridex activity, but the group was able to resurrect the botnet. In June 2016, GOLD DRAKE consistently decreased the cadence of distribution campaigns, using the botnet for more targeted attacks. In December 2019, the DOJ indicted Maksim Yakubets and Igor Turashev for their roles in the Dridex operation.
Despite facing close scrutiny after the 2019 law enforcement intervention, high-volume campaigns paradoxically resumed in early 2020. GOLD DRAKE distributed Dridex via various methods, including spam emails from GOLD ESSEX's Cutwail botnet, second-stage downloads from Gozi ISFB and GOLD CRESTWOOD's Emotet botnet, and drive-by downloads using GOLD PRELUDE's SocGholish malware. When GOLD DRAKE swapped BitPaymer for WastedLocker in May 2020, they abandoned Dridex and transitioned to PowerShell scripts distributed by SocGholish to execute payloads. With Hades attacks, GOLD DRAKE again diversified, making extensive use of Cobalt Strike and common post-compromise tools. SocGholish has continued to be used for initial access, although CTU™ researchers also observed Hades ransomware attacks in early 2021 using stolen credentials as the initial access vector.
CTU analysis indicates that GOLD DRAKE members in possession of the BitPaymer and Dridex source code formed the GOLD HERON threat group in early 2019. This new group operated the DoppelPaymer ransomware from June 2019 until May 2021, when they replaced it with the Grief ransomware. GOLD HERON continued to use Dridex (often referred to as Dridex 2.0 or DoppelDridex) sparingly until Grief operations ceased in May 2022.
GOLD DRAKE's adoption of LockBit made sense from a business perspective. It enabled the group to avoid the costs associated with maintaining infrastructure and with adapting or creating new ransomware to avoid detection and circumvent sanctions. Given LockBit's historically prolific activity, GOLD DRAKE's actions would blend in with the noise and delay identifying the group as an affiliate of the scheme.
Law enforcement impact
While announcing that Operation Cronos's impact on LockBit operations has been significant, the NCA acknowledges that many affiliates have likely moved to other schemes and that revenue from all ransomware operations actually increased in 2024 (see Figure 3). CTU analysis supports the claim that this increase has "almost certainly" been reduced as a result of the law enforcement efforts.
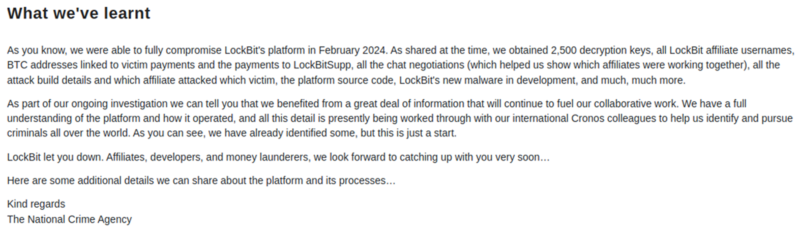
Figure 3. NCA statement regarding Operation Cronos's impact on the LockBit RaaS scheme. (Source: Secureworks)
Leak site data indicates that the operation has significantly damaged the ransomware scheme. Despite a surge in victim naming following Phase 2 of Operation Cronos in May, the monthly average is well below the pre-takedown numbers (see Figure 4).
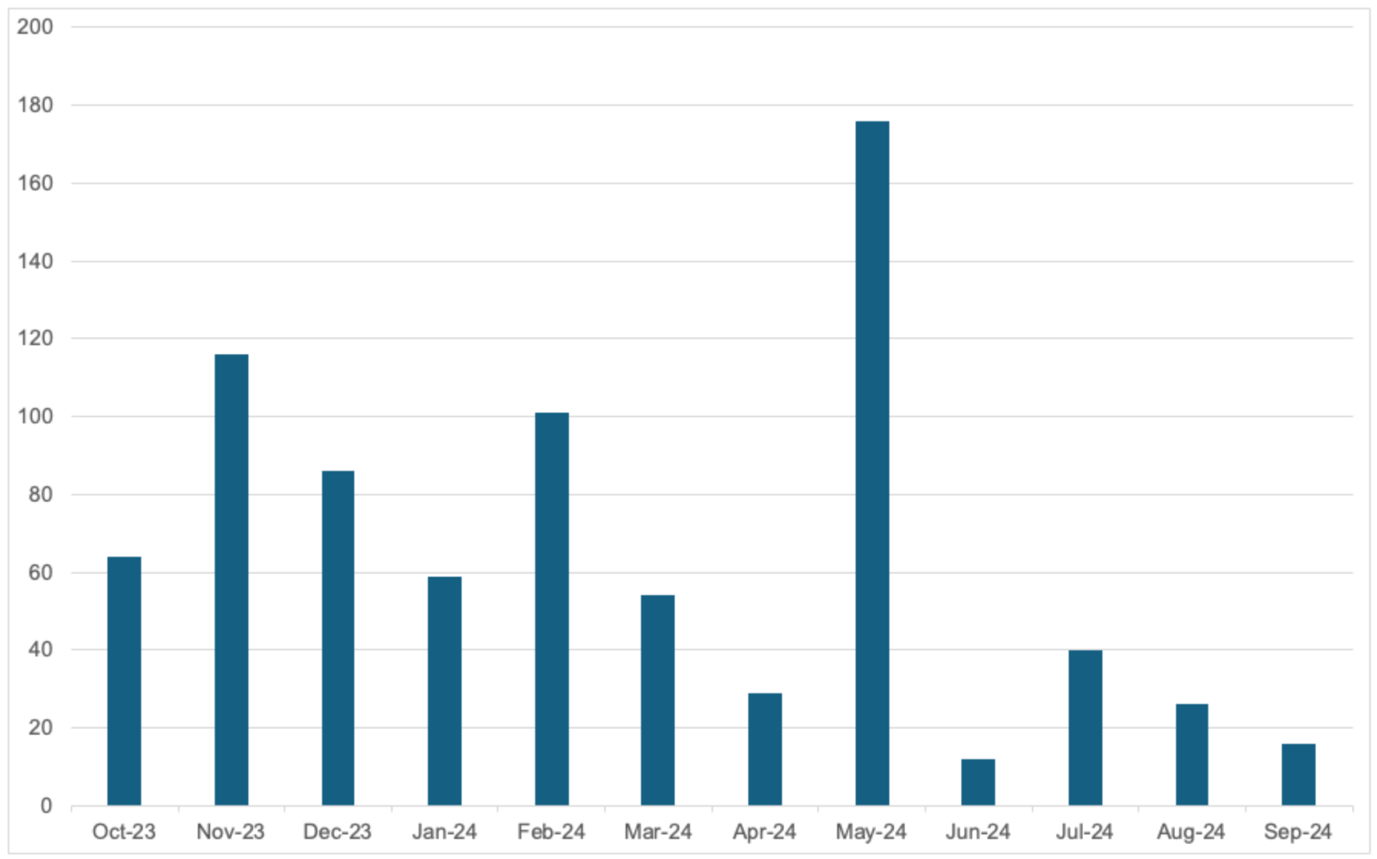
Figure 4. Number of LockBit victims named on leak sites from October 2023 through September 2024. (Source: Secureworks)
The NCA reported that the number of LockBit affiliates dropped between the first two Operation Cronos phases, from 194 in February 2024 to only 69 by May 2024. The number has likely declined further since the May U.S. sanctions against LockBit administrator Dmitry Khoroshev effectively make paying a ransom to a LockBit affiliate illegal for organizations incorporated in the U.S. or UK. However, an analysis of LockBit leak site data suggests that the proportion of U.S. or UK-based victims has remained fairly consistent (see Figure 5). That said, the NCA claims that much of the post-takedown LockBit victim data is likely to be false.
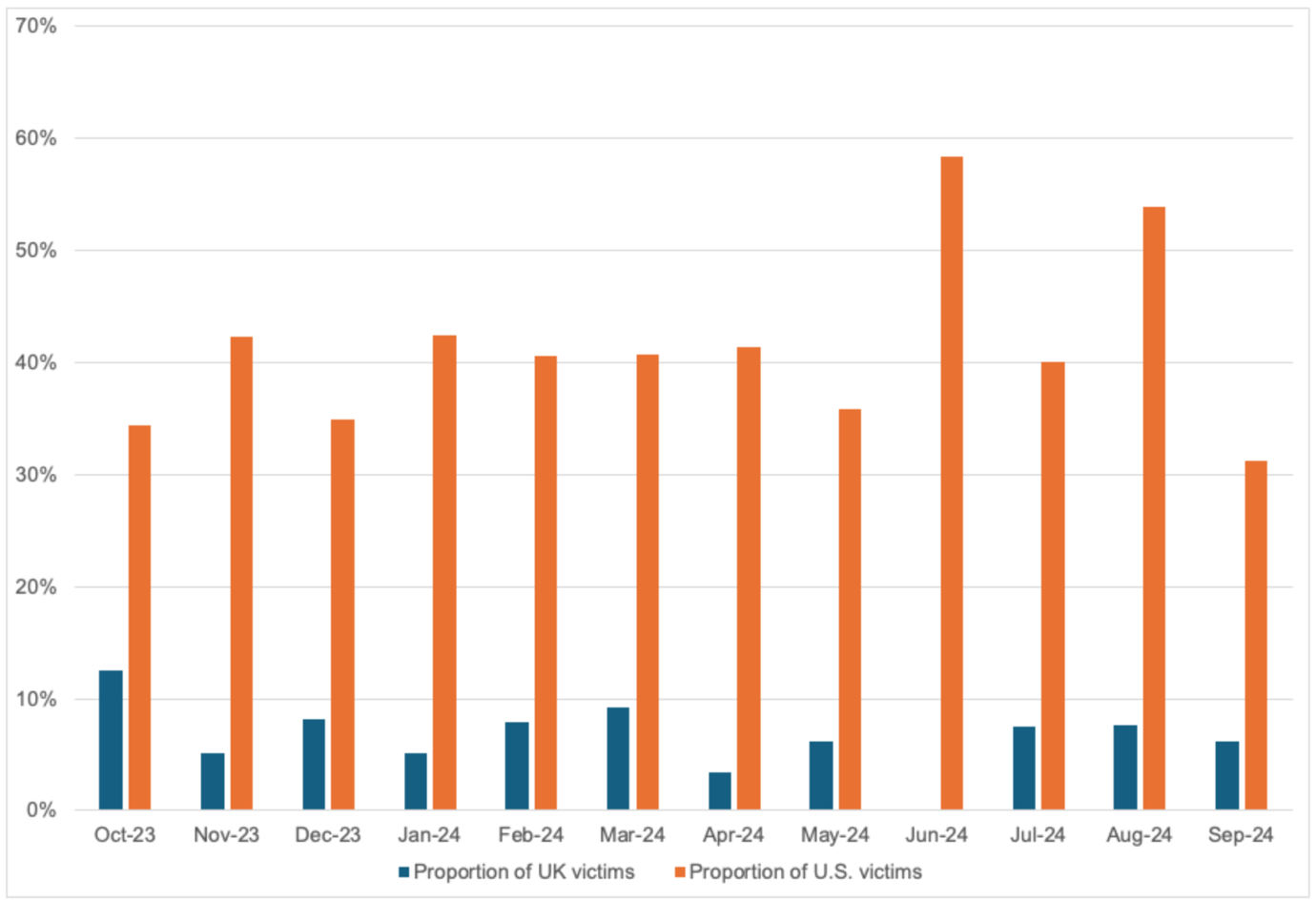
Figure 5. Proportion of LockBit victims incorporated in the U.S. or UK from October 2023 through September 2024. (Source: Secureworks)
A key goal of Operation Cronos is damaging Khoroshev's reputation. In Phase 3, the NCA reiterated that he does not keep his promises to delete victim data after a ransom is paid. Analysis of an administration panel illustrated that no victim data was recorded as deleted since 2022 (see Figure 6).
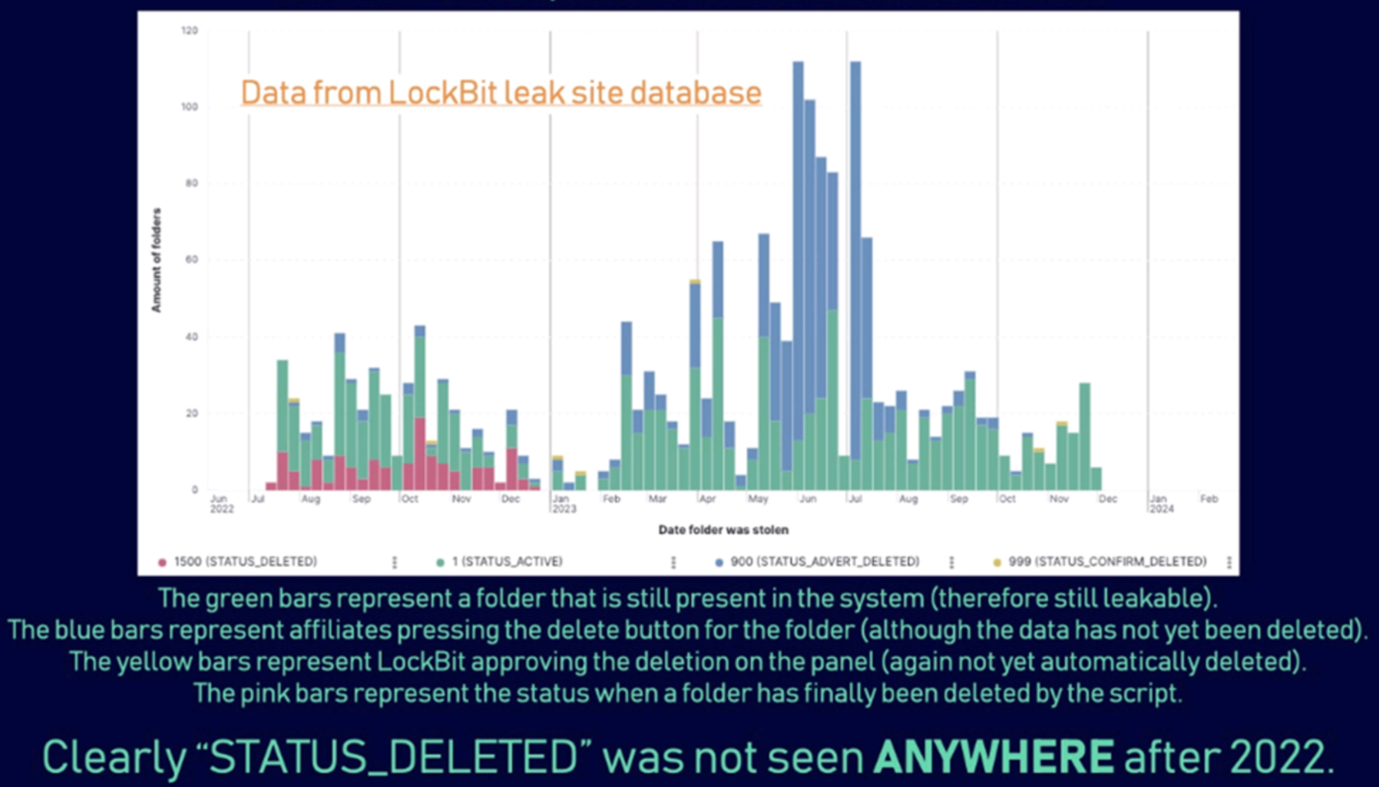
Figure 6. NCA analysis of LockBit infrastructure showing that victim data was not deleted following ransom payments. (Source: NCA)
Conclusion
Actions against Evil Corp (GOLD DRAKE) in Phase 3 of Operation Cronos represent efforts to disrupt and expose one of the world's most prolific cybercrime groups. The sanctions will make it harder for the named individuals to conduct business but will likely not stop them from operating from a permissive jurisdiction. The sanctions require victims to consider the ultimate destination of their payments if they decide to pay the ransom.
The NCA's analysis paints the clearest picture to date of the confluence of Russian cybercrime and the Russian Federation's intelligence services. However, the revelations do not definitively establish state-directed tasking of cybercriminal groups.
For more details about LockBit and previous Operation Cronos activity, read Unpicking LockBit — 22 Cases of Affiliate Tradecraft.