On Friday, July 2, Secureworks® Counter Threat Unit™ (CTU) researchers began investigating an active attack on the Kaseya VSA Remote Monitoring and Management (RMM) software, which was observed distributing REvil ransomware.
CTU™ researchers have assessed with moderate confidence that this was a large-scale orchestrated attack by a GOLD SOUTHFIELD affiliate against a subset of Kaseya VSA clients, largely managed service providers (MSPs). Kaseya released a statement identifying a vulnerability in the VSA server that facilitated the attacks and signalled their intent to patch it. There is no available evidence to suggest that Kaseya's software update infrastructure has been compromised.
CTU™ researchers have assessed that this activity was an attack against clients of the Kaseya software and consider the timing of the activity around a major U.S. holiday as unlikely to be coincidental. According to Kaseya, the attack was limited to a small number of on-premise customers and did not impact their SaaS offering.
The infection chain begins with the legitimate Kaseya VSA agent executable, AgentMon.exe, executing a sequence of commands (see Figure 1).
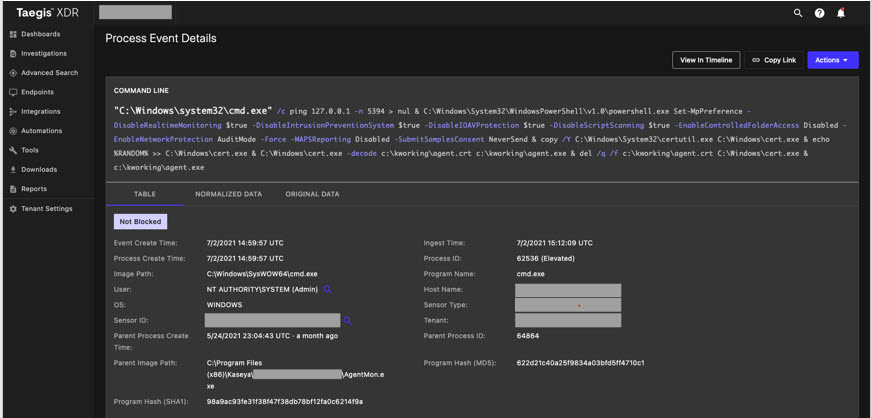
Figure 1. Kaseya agent executing command sequence to initiate REvil infection. (Source: Secureworks)
The sequence of commands carries out several tasks:
- Uses the ping command to delay execution by a random number of seconds.
- Disables various aspects of Microsoft Defender using PowerShell cmdlets.
- Copies the legitimate CertUtil executable and appends a random integer to cause its cryptographic hash to be randomized.
- Uses CertUtil to decode the encoded malware loader payload, deployed by the Kaseya agent as agent.crt, to agent.exe.
- Deletes the encoded payload file and copied version of CertUtil.
- Executes the decoded loader malware payload stored as agent.exe.
The agent.exe malware is a simple loader that deposits two files: C:\Windows\MsMpEng.exe and C:\Windows\mpsvc.dll. MsMpEng.exe is a legitimate copy of the Microsoft Defender program that loads mpsvc.dll upon execution. The malware first attempts to drop the files into C:\Windows. If it is unsuccessful, the malware drops the files to %TEMP%. The mpsvc.dll file is a cryptor that unpacks a headless instance of REvil into memory and executes it.
It is likely that any organizations who were going to be affected by this attack will have experienced some impact by now. Nevertheless, customers should ensure that they continue to follow the advice published by Kaseya on their website (https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689-Important-Notice-July-2nd-2021) and, where possible, ensure that endpoint controls are deployed to systems running Kaseya software and actively monitored for any evidence of intrusion activity. If there is a material update to the information contained in this advisory, Secureworks shall promptly issue an updated advisory. If you believe you were compromised, please call the Secureworks Incident Response hotline at +1-770-870-6343.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

