Secureworks® Counter Threat Unit™ (CTU) researchers are investigating activity attributed to the Iranian Cyber Av3ngers hacktivist group. This group has been linked to attacks dating back to at least February 2022. The attacks often target Unitronics programmable logic controller (PLC) systems.
On November 25, 2023, the Municipal Water Authority of Aliquippa near Pittsburgh reportedly experienced a cyberattack. The reports indicate that threat actors claiming to be affiliated with the Cyber Av3ngers anti-Israeli hacktivist group shut down a pump on a supply line that provides drinking water from the Aliquippa treatment plant to two townships. Images released by the Aliquippa Water Authority show the systems control panel displaying the message "You have been hacked. Down with Israel. Every Equipment 'made in Israel' is Cyber Av3ngers legal target" (see Figure 1). Although this was a high-profile attack that prompted many headlines and an alert from the U.S. Cybersecurity & Infrastructure Security Agency (CISA), the impact to the water authority's customers was minimal. The compromised device was isolated from the primary network.
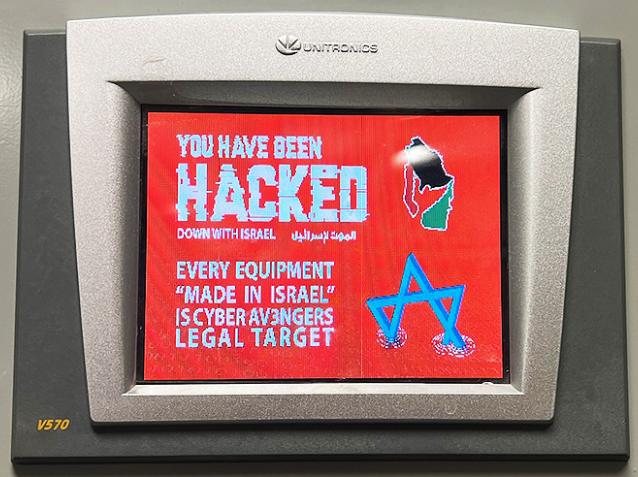
Figure 1. Control panel display for the Aliquippa Municipal Water Authority. (Source: https://beavercountian.com/content/special-coverage/iranian-linked-cyber-army-had-partial-control-of-aliquippa-water-system)
Although originally investigated as an isolated attack, CTU™ researchers discovered reports of devices from four additional organizations that appear to have been compromised in this campaign: a water company in Romania, a factory in the Czech Republic, a system controlling mineral water drinking fountains in the Czech Republic, and a brewery control system in Pittsburgh. It is likely that devices at other organizations were also compromised but have not been publicized.
In February 2022, Unitronics devices associated with the E-Post parcel distribution centers in two Israeli cities were compromised, allowing the threat actors to remotely open some postboxes and prevent access to others. In April 2023, a cyberattack impacted ten water controllers linked to irrigation systems on several farms in the northern region of Israel. In both of these attacks, the message displayed on Unitronics devices was similar to the message in the Aliquippa attack (see Figure 2). These images do not reference Cyber Av3ngers, but they use the same style and imagery. The messages and targeting of Unitronics devices suggest that the same group is responsible for these three attacks. However, the lack of information about the tactics, techniques, and procedures (TTPs) or tools used in the attacks makes definitive attribution more difficult.
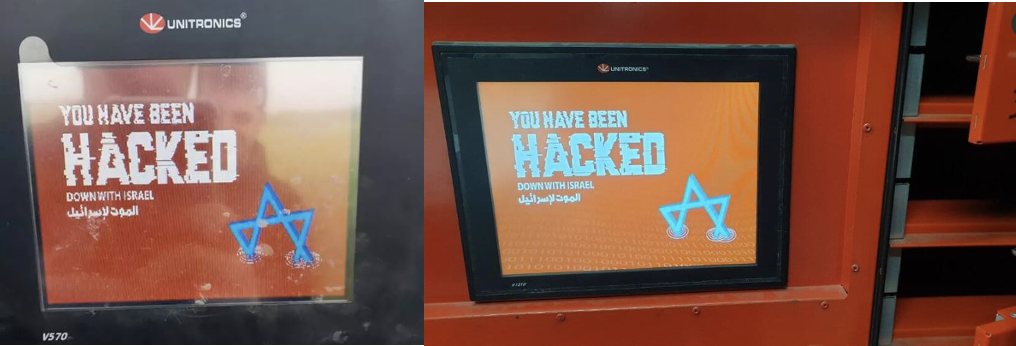
Figure 2. Unitronics displays in the irrigation (left, Source: https://www.jns.org/cyberattack-shutters-galilee-farm-water-controllers/) and E-Post (right, Source: https://firedome.io/blog/unitronics-plc-cyber-attack/) attacks.
Unitronics devices have become a target for pro-Palestinian hacktivists because they are made in Israel. In October 2023, another pro-Palestine hacking collective named GhostSec claimed attacks on multiple Unitronics devices controlling water pumps across Israel (see Figure 3).
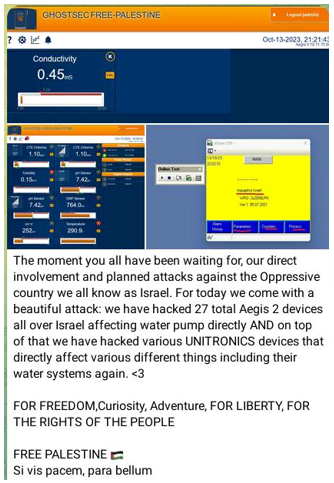
Figure 3. GhostSec claiming attacks on Unitronics devices in Israel. (Source: Secureworks)
The NewBloodProject Telegram channel, which is associated with GhostSec and describes itself as "a community for learning everything related to ethical hacking and hacktivism," posted a PDF guide to compromising ICS and SCADA systems in March. This guide contains a section dedicated to Unitronics devices (see Figure 4).

Figure 4. NewBloodProject guide for compromising ICS and SCADA systems includes a section on Unitronics devices. (Source: Secureworks)
Cyber Av3ngers is active on social media, regularly claiming attacks against Israeli critical national infrastructure. One of the Telegram posts links to a July 2020 article describing an attack that allegedly involved 150 Israeli railway system servers and impacted 28 railway stations. Cyber Avengers (spelled at the time without the '3') claimed responsibility. The time of the attack aligned with the airstrikes that killed Islamic Republican Guard Corp (IRGC) Commander Qasem Soleimani on January 3. In September 2023, the hacktivists used their X account to advertise data seemingly stolen during the July attack. They offered to sell information about 3,000 employees and over 10 million journeys, including passenger details, for 4 BTC (approximately $108,000 USD at the time of posting).
Throughout October 2023, Cyber Av3ngers continued to post claims of high-profile attacks against power plants, gas stations, and other critical national infrastructure assets. However, most of these claims were exposed as exaggerated or fabricated. The group claimed an attack on the Dorad power station in Israel, posting images of SCADA systems to Telegram as proof (see Figure 5). However, security researchers determined that these "leaked" documents had been recycled and repurposed from an attack by the Moses Staff hacktivist group, which CTU analysis suggests is linked to the IRGC. CTU researchers associate the Moses Staff persona with the COBALT SAPLING threat group. Cyber Av3ngers may have reused images downloaded from Moses Staff's leak site, or the two groups may be coordinating behind the scenes.
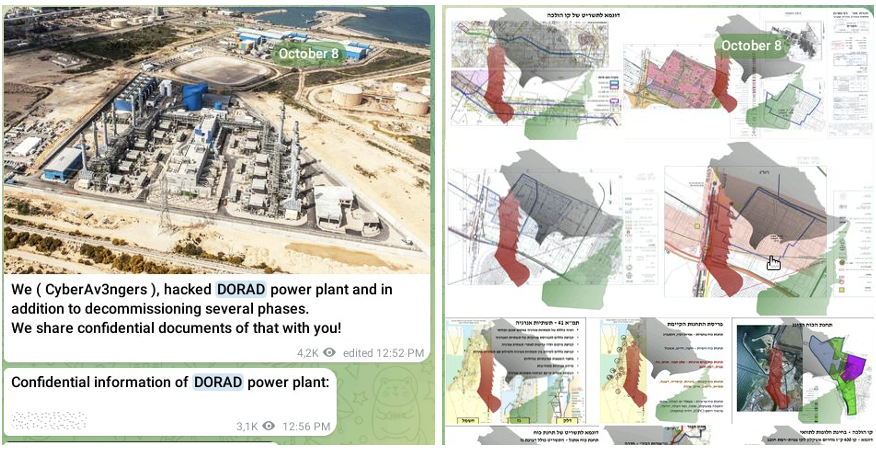
Figure 5. Cyber Av3ngers claiming an attack on the Dorad power station. (Source: Secureworks)
The compromise of the Unitronics device at the Aliquippa water authority is a significant escalation in hacktivist activity. Although it was not more technically proficient than previous attacks, it was the first Cyber Av3ngers attack on a U.S. facility. The attack generated a great deal of media attention and undoubtedly put the group in the sights of U.S. authorities.
It is highly likely that Cyber Av3ngers is operated by an Iranian state-sponsored threat group in the same way that COBALT SAPLING operates the Moses Staff and Abraham's Ax personas. This assessment is based on Iranian news media references to the early attacks when few other outlets covered them and CISA's attribution of the November 2023 attacks to an IRGC-affiliated unit. Cyber Av3ngers' likely use of digital reconnaissance techniques such as searching internet survey services (e.g., Shodan, Censys) to identify vulnerable Unitronics devices is also similar to tactics used by Iranian groups. A July 2021 report discussed leaked documents allegedly compiled by a team named "Intelligence Team 13" within Shahid Kaveh unit. The documents detailed digital reconnaissance against industrial systems such as ballast water pumps in ships, fuel pump systems, and maritime communications systems beginning in late 2020.
CTU researchers recommend that organizations using Unitronics devices review the information in the CISA advisory and apply the guidance as appropriate. The UK National Cyber Security Centre (NCSC) echoed the CISA advice.
Learn more about scan-and-exploit attacks and other threats in the 2023 State of the Threat report. If you need urgent assistance with an incident, contact the Secureworks Incident Response team.