Media Alert: Tinba Banking Malware Also Targeting Financial Institutions in Japan and many other countries
ATLANTA , November 3, 2015 – Security researchers with Dell SecureWorks’ Counter Threat Unit™ (CTU) team have found that an instance of the Tinba banking trojan, also known as Tiny Banker for its small code size, is targeting customers of top banks and popular payment service providers in Russia. Dell SecureWorks can confirm that configuration files for the malware show that one of its Russian targets is among the biggest banks in Europe, in addition to two popular Russian payment service providers.
Russian Banks and Russian Financial Organizations Not Frequently Targeted by Top Banking Trojans
Historically, security researchers have found that many of the masterminds behind some of the most pervasive banking trojans and other money-making malware (such as spam bots) tend to be from Russia, Ukraine or Eastern Europe. And similarly, we have seen very few of these bank trojans and other families of malware target Russian computer users. In fact, in the past some of these trojans were designed to do automatic checks of the victim’s computer keyboard and language settings. If the malware saw that the primary language was Russian and the keyboard was in Cyrillic, the malware would immediately exit or uninstall. There definitely seemed to be a propensity on the part of the cyber criminals behind these operations not to compromise Eastern European and Russian computers.
One reason that may explain why Russia is not more frequently targeted is because Russian law enforcement has cracked down on cybercriminals targeting their citizens. For example, the Carberp banking trojan that targeted Russian banks in 2013 led to the arrest of several members of the Carberp gang and its leader, a 28-year old Russian national, as a part of a joint operation between the Security Service of Ukraine and the Russian Federal Security Service. According to a report in the Ukrainian media outlet, Kommersant Ukraine, the Carpberb gang successfully stole $250 million from Ukrainian and Russian banks.
Tinba Also Targeting Japanese Banks
Tinba has also joined the growing ranks of banking malware targeting financial institutions in Asia, specifically Japan. Currently, Tinba threat actors are focused on customers of Shinkin financial institutions. Shinkin banks are cooperative regional financial institutions that service small and medium businesses, as well as local residents.
During the last two years, the number of banking trojans infecting computers in the Asia Pacific region has continued to increase, and currently includes Trojans like Shiz (aka Shifu) and Reactorbot. In addition to Japan, there have also been widespread infections seen in Indonesia and Malaysia during the past year.
Tinba is a botnet kit with many threat groups going after banks in not only Russia and Japan, but many financial organizations in other parts of the world including North America, the United Kingdom, Europe and Australia, in addition to large credit card companies, online payment providers, shopping portals and social media sites.
History of Tinba Banking Trojan and How it Works
Tinba provides many features to steal financial account credentials, one-time passwords and other sensitive information from a compromised system that can be used to commit Automated Clearing House (ACH) and wire fraud. There are two versions of the Tinba trojan. The source code for Tinba 1.0 was leaked in July 2014 and the authors were believed to be out of Eastern Europe. Tinba 1.0 is still used by a few threat groups, but is nowhere near as popular as the latest Tinba 2.0 variant, which appears to be controlled by one threat group and sold as a botnet kit to multiple cybercriminal gangs. The threat group controlling Tinba 2.0 is also believed to be out of Eastern Europe. It is the Tinba 2.0 version that has been observed infecting victims in Russia and Japan.
Tinba 2.0 added several new features since Tinba 1.0’s source code was leaked. The most significant among them was a domain generation algorithm (DGA) designed to make mitigation efforts by security professionals more difficult. While the first variant of Tinba 2.0 attempted to generate 1,000 domains, using a single hard-coded Top-Level Domain (TLD), the newer variant of Tinba 2.0 generates 100 domains using four hard-coded TLDs, resulting in a total of 400 possible domains. Only one of these domains is needed by the threat actors for them to maintain control of their botnet.
Tinba 2.0 also added RSA signature verification to determine whether the Command and Controller (C2) that it is communicating with it is a true C2 or a security researcher’s sinkhole.
Each Tinba 2.0 botnet kit is configured with different parameters such as distinct domain names, RSA keys, and request paths. As of October 2015, CTU researchers had observed 655 registered domains, 62 unique request paths and 43 unique encryption keys. This information indicates there are likely more than a dozen threat actors or groups operating Tinba 2.0 botnets.
Since its release in September 2014, Tinba 2.0 has been extremely active and is responsible for tens of thousands of active malware infections. On October 15th, 2015, abuse.ch collected data from several sinkholed Tinba botnets and documented infections from 32,805 unique IP addresses, which does not include all currently active Tinba 2.0 botnets. A total of 34.5% of the victims observed at the botnet sinkhole were located in Russia, while Poland and Indonesia made up 22 % and 7.2% of the victims respectively.
However, the large concentration of infections in Russia is not representative of all Tinba 2.0 botnets, because many threat groups using the Tinba malware target specific regions, as we garnered from the vast list of web injection targets. Figure 1 shows a world map of Tinba 2.0 infections observed from the abuse.ch sinkhole on October 15, 2015.
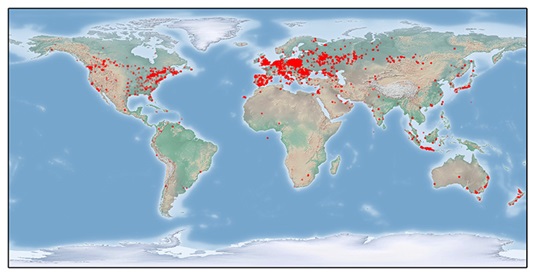
Figure 1: Map of Tinba 2.0 infections on October 15, 2015. (Source: Dell SecureWorks and abuse.ch)
Mapping the IP addresses of Tinba 2.0 infections observed at the sinkhole on October 15th, 2015 to their locations reveals the following top 10 affected countries:
- Russia (34.5%)
- Poland (22.0%)
- Indonesia (7.2%)
- Spain (6.5%)
- Canada (5.6%)
- Romania (5.0%)
- Germany (2.6%)
- Australia (1.8%)
- United Kingdom (1.8%)
- Japan (1.7%)
How Tinba is Infecting its Victims
Currently, Tinba 2.0 is being distributed through spam email and exploit kits such as Nuclear, Neutrino and Angler, and is targeting financial institutions, webmail services, social networking sites and other organizations around the world.
“The malware provides an effective and lightweight alternative to the Zeus banking trojan, with numerous methods to harvest sensitive information from a compromised system,” said Dr. Brett Stone-Gross, Sr. Security Researcher with Dell SecureWorks. “Threat actors can use this information to steal a victim’s identity and commit ACH or wire fraud. The command-and-control communications rely on a domain generation algorithm (DGA) and verify the legitimacy of the server through RSA cryptography, making Tinba 2.0 botnets more challenging to disrupt. As a result, CTU researchers expect Tinba 2.0 to continue to remain popular in the foreseeable future.”
How Computer Users Can Protect themselves from the Tinba Banking Trojan
The following actions may mitigate the risk of becoming infected with the Tinba Banking trojan:
- Keep antivirus, operating systems, browsers, and browser plugins, such as Java and Silverlight, fully updated to prevent compromises resulting from exposure to exploit kits.
- Filter email / scan email file attachment contents and consider blocking executable file types (including those found in ZIP attachments).
- Educate users about the dangers of clicking on links and attachments in emails, instant messages, and on social networking sites.
